Security Dialog
Authorized Users and Roles
This pane provides a list of users and roles that can access the named resource in the top panel. For example, if you click Machines, a dialog displays where you can add the users or roles and set their permissions to access the Machines panel.
Inherit Parent's Security Settings
This option allows you to set whether the current item should inherit permissions from its parent in the Security tree.
For example, in the next diagram, a TimerProcessArchive application inherits all security settings from Management Consoles, which in turn inherits all settings from timertest, which inherits from Application Management.
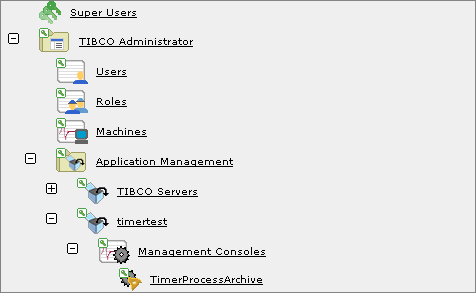
By default, if you grant permissions to a user to the Application Management folder, that user also has the same permission to all items contained in the folder’s tree. To give that user permission to only one application, or to only the applications, but not the TIBCO Servers, you must change the Inherit Parent’s Security Settings.
You don’t need to grant read permission at the top level since consoles which are parents to ones a user has read permission for show up in the console tree. This is true even if the user does not have read permission to the parent. However, the parent only displays those children needed to navigate to consoles for which the user does have read access
View Inheritance
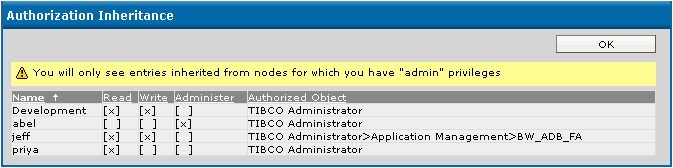
You must have Administer permissions for the object you are querying to view inheritance. The dialog that displays lists the name of the object that has permission, the access permission and the parent object that provides the permission setting for the object in question.
For example, the next diagram shows the permissions that are inherited by a service object. The Development role has Write permissions assigned on the service object’s parent BW_ADB_FA. Three users also have permissions assigned to the service object at the top level TIBCO Administrator folder.
Add Users
Displays the Add Users dialog where you can add users and then specify their access rights. Select one or more users from the Users list, and then click the Add button. Click OK to add the users to the new role. You can also change security settings. See Permissions Tab for a description of security settings.
Add Roles
Displays the Add Roles dialog where you can add roles and then specify their access rights.
Remove
Removes the selected user and role from the access list.
View all authorized users
Lists all users who have been authorized to use this console. This includes the users and roles membership inherited from parent resources, if any, and also those directly specified for the selected console. Security rights are listed for each user.