Using X.509 Certificates or SAML Tokens for SSO Authentication
TIBCO ActiveMatrix BPM supports the use of X.509 certificates or signed SAML tokens to facilitate SSO authentication. This means that a user who already has a login session with the client application does not need to provide their login credentials again when calling a TIBCO ActiveMatrix BPM service (provided that their credentials are also valid for logging in to TIBCO ActiveMatrix BPM).
Web service security (WS-security) protocols are used to enforce authentication requirements. Every API call to a TIBCO ActiveMatrix BPM service must include an appropriate token in the SOAP header that can be used to authenticate the calling entity (as a user who is registered in the TIBCO ActiveMatrix BPM organization model). An API call that does not meet this requirement is rejected.
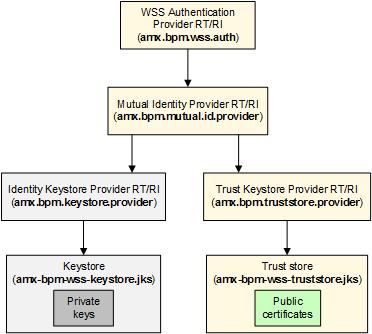
At runtime, TIBCO ActiveMatrix BPM WSS authentication provider shared resources are used to enforce security policies on the endpoint of every TIBCO ActiveMatrix BPM service, to ensure that access to those services is restricted to authenticated users.
To enable SSO, TIBCO ActiveMatrix BPM must have access at runtime to the public certificate provided by a client application, so that it can validate the digital signature on an incoming message. The following illustration shows the TIBCO ActiveMatrix runtime resource instances (RI) and resource templates (RT) that are used to provide this access.