Example 3 - Impersonation Using a SOAP Binding
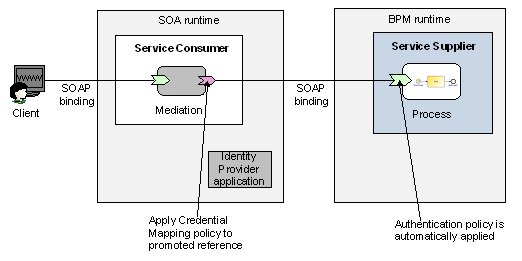
In this example, the Mediation application accesses the BPM service using a fixed (impersonated) identity, no matter what credentials are used to access the Mediation application itself. (The Mediation application may even allow anonymous access.)
An identity provider application must be created to provide the valid identity that will be used to access the BPM service.
To enforce authentication using impersonation:
Procedure
- In the SOA runtime, create and configure an identity provider application that will be used to inject the appropriate credentials into the call to the BPM service.
- Add an appropriate credential mapping policy to the promoted reference. The policy will be applied at runtime, forcing the reference to propagate the identity defined in the referenced keystore to the endpoint of the exposed service.
Copyright © Cloud Software Group, Inc. All rights reserved.