Overview of Security Policies
This section explains the security policies supported by TIBCO API Exchange Gateway software.
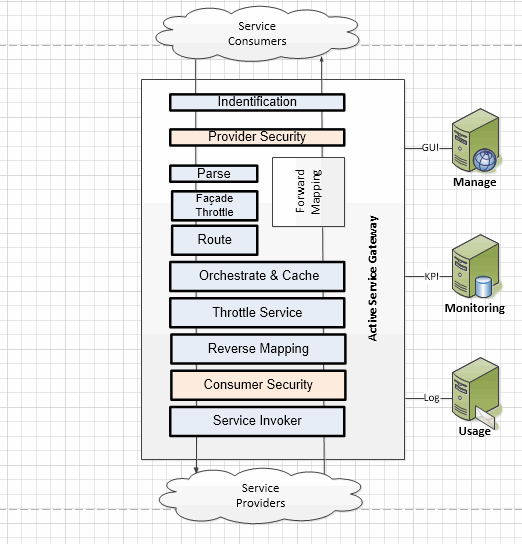
TIBCO API Exchange Gateway allows you to secure a facade operation or a target operation using various types of security policies. This allows you to apply the policy to the incoming messages received from the service consumers and also apply the policy to the outgoing messages forwarded to the service providers. You can apply the policies at the endpoints of facade or target operations. See Types of Security Policies for the details on the supported policies.
The figure below illustrates the security policy enforcement points in the standard request processing pipeline.
- Security Concepts
- Types of Security Policies
The following types of security policies are supported by TIBCO API Exchange Gateway. - Manage Policies
- Policy Use Cases
This section describes the use cases for supported policies. - Types of Security Shared Resources
- Shared Resources Properties
- Authentication using File-Based Identity Store
Overview of file-based authentication. - Data Masking and Selective Log Policy
TIBCO API Exchange Gateway masks the sensitive data in a payload and selectively logs only the relevant data. - AntiVirus Scan of Request and Response Payloads
TIBCO API Exchange Gateway can scan the request and response payloads of a facade operation.
Copyright © Cloud Software Group, Inc. All rights reserved.