Creating or Editing a SAML Authentication Shared Resource
SAML Authentication shared resources can be created or edited using the TIBCO BPM Enterprise Administrator.
- Procedure
- From the
TIBCO BPM Enterprise Administrator screen, select
Shared Resources Manager.
- From the Shared Resources List in the left pane, select
SAML Authentication.

- In SAML authentication, click
 .
.
- Add the new SAML Authentication shared resource details based on the following description:
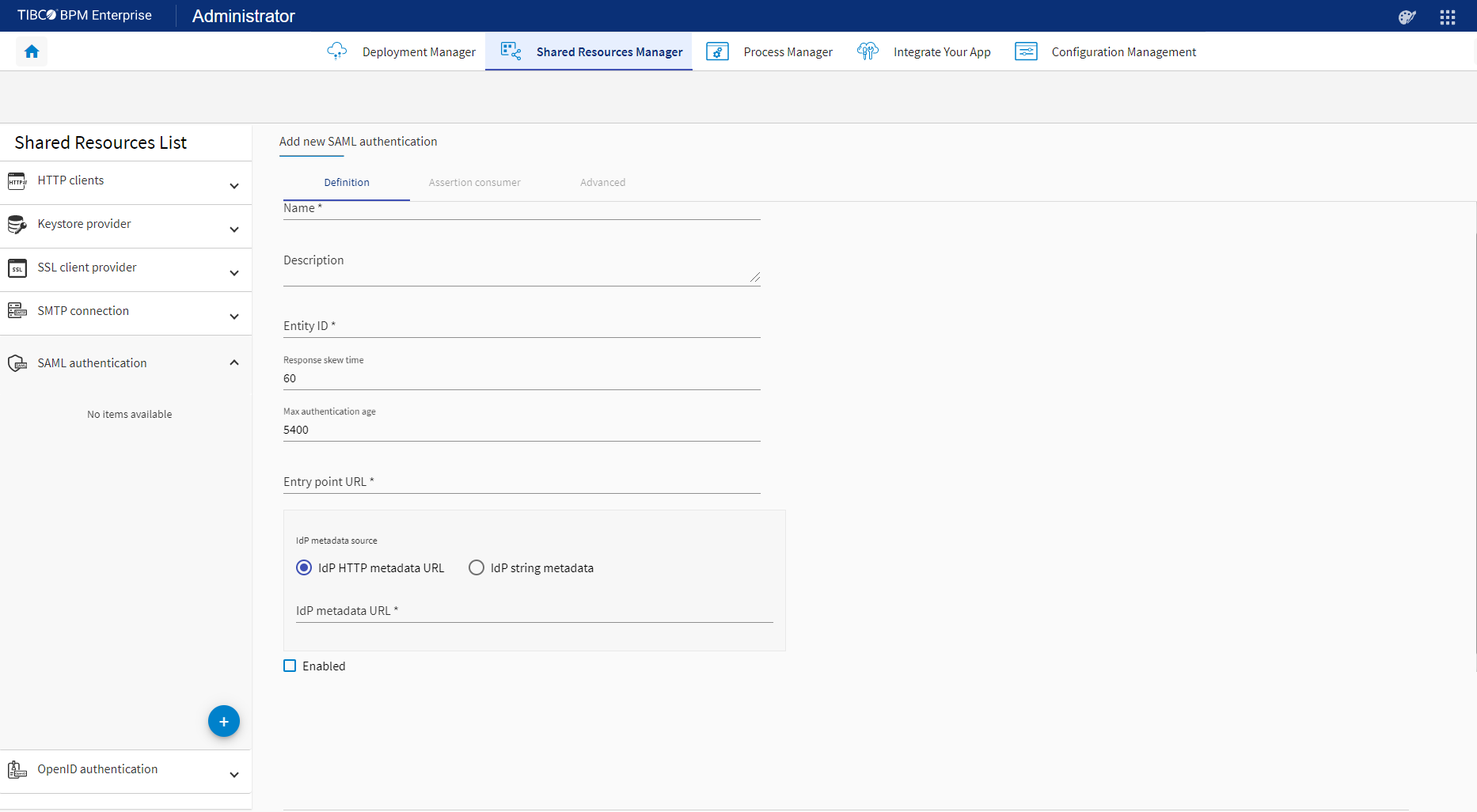
Definition Property Description Name (Required) The unique name of the SAML authentication shared resource. The values in this field are not case sensitive. Description A description of the SAML authentication shared resource. Entity ID (Required) A unique ID that identifies the service provider and application that has been registered with the IdP. This must match the ID that was configured at the IdP. Response skew time Specifies, in seconds, the maximum difference allowed between the clocks of the IdP and the TIBCO BPM Enterprise server. Default: 60
Max authentication age Specifies, in seconds, the maximum time an authentication will remain valid. Default: 5400
Note: 'Max authentication age' value should match with 'Session duration' set on the IDP. For example, 'max Authentication Age' should have a larger value than what a user sets for 'Session never expire' in the Google IDP while configuring the SAML shared resource (for example, 30 days means 2592000 seconds).IdP metadata source (Required) Specifies the source of the metadata file from the IdP. Click one of the following two options: IdP HTTP Metadata URL, if you have the URL location for the IdP metadata. Enter the HTTP URL for the location where the metadata provided by the IDP is hosted. For example,
http://hostname/Metadata.xmlIdP String Metadata, if you have the metadata file from the IdP. Enter the Metadata provided by the IdP.
Alternatively, click Upload XML metadata file, if you have a local IdP metadata file. When the IdP metadata file is uploaded, the file content is populated in the text box.
Entry Point URL (Required) The relative entry point URL to initiate the SAML handshake with IdP. For example, /saml/loginEnabled Select this check box to enable the SAML Authentication shared resource for Single Sign-On (SSO). Currently, only one SAML Authentication shared resource can be enabled. Note: At any point, only a single SSO related shared resource can be enabled, that is, either SAML or OpenID.Assertion consumer
All the fields in the Assertion consumer tab except the Assertion Consumer Service URL are read-only. The values of the read-only fields are derived from the value in the Assertion Consumer Service URL field.
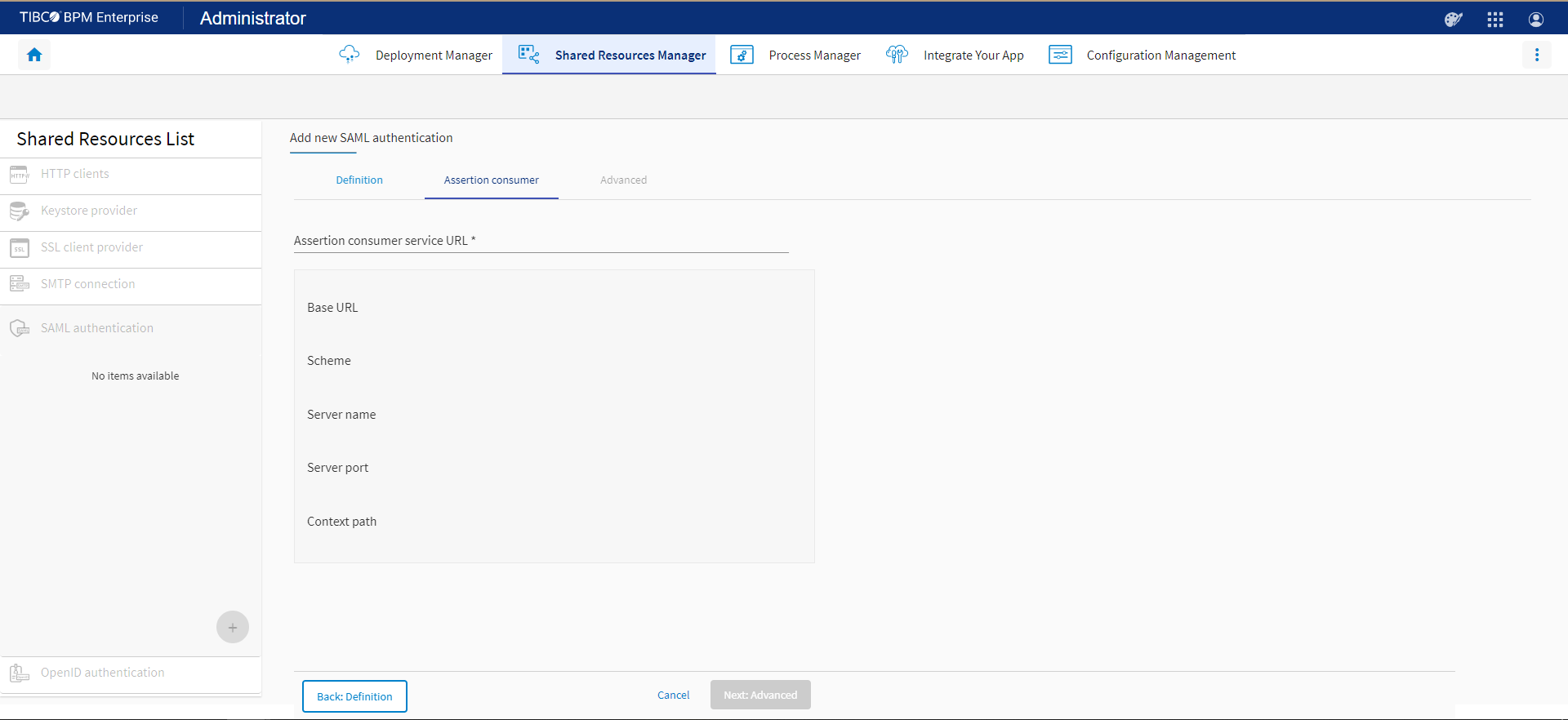
Property Description Assertion Consumer Service URL (Required) Assertion Consumer Service (ACS) URL defines the endpoint that receives authentication assertions from the IdP.
The IdP must use the same URL to configure Assertion Consumer Service (ACS) endpoint. For example,
http://bpm-host:8228/saml/SSOBase URL The base URL where TIBCO BPM Enterprise is hosted. For example, http://bpm-hostScheme The HTTP scheme. For example, httporhttps. This is a part of the ACS URL.Server name The server name. This is a part of the ACS URL. Server port The server port. This is either a part of the ACS URL or takes the default value. Context path The context path. This is a part of the ACS URL. Advanced
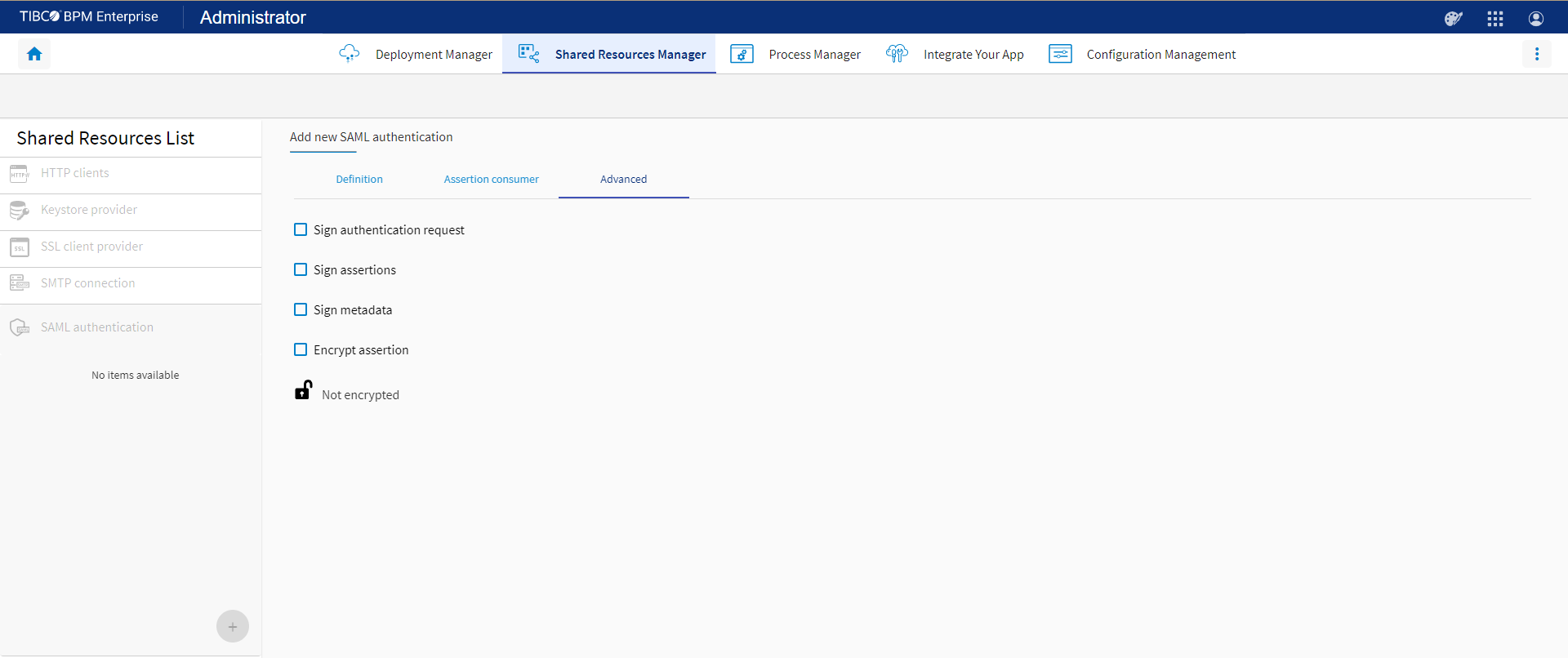
Property Description Sign authentication request Select the check box to sign the authentication request. Ensure that the authentication request from the service provider is signed before you select this check box. Provide a valid public key or certificate to the IdP to identify signed requests. Sign assertions Select to sign assertions. Sign metadata Select to sign metadata. Encrypt assertion Select to encrypt assertion. The following fields are displayed if any one of the above options is selected. Keystore provider name (Required) The name of the KeyStore Provider used for encrypting and signing. Key alias to encrypt (Required when Encrypt assertion is selected) The alias of the key used for encrypting. Key alias to encrypt password (Required when Encrypt assertion is selected) The password for the key that is used for encrypting. Default key alias (Required) The alias of the default key. Default key alias password (Required) The password for the default key. Key alias to sign (Required when one of the signing related options is selected)The alias of the key used for signing. Key alias to sign password (Required when one of the signing related options is selected) The password for the key is used for signing. 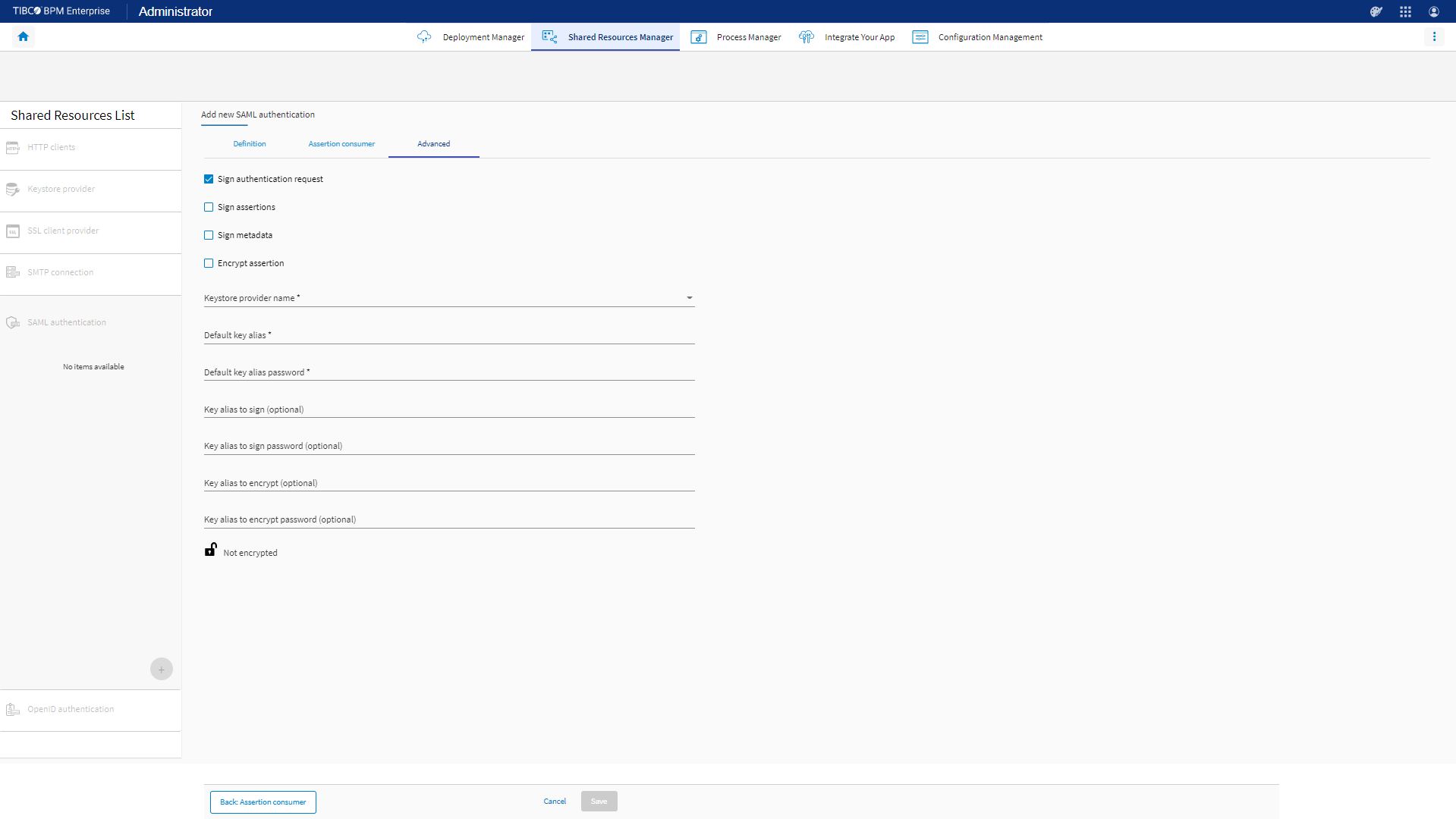
- Click
Save.
Note: It is necessary to restart the TIBCO BPM Enterprise containers so the SAML shared resource can be used for authentication.