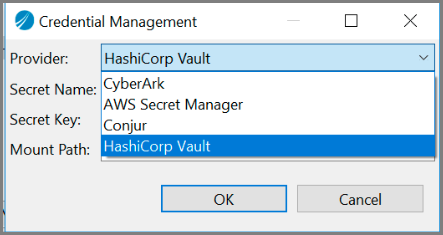
Using HashiCorp Vault for Credential Management Service
HashiCorp Vault is used to integrate with TIBCO BusinessWorks™ Container Edition for credential management system to retrieve passwords from the vault to use it within the application at runtime when the password is required. This would avoid adding any passwords in the deployment configuration and redeploying the application.
A new HashiCorp Vault provider is added for the Credential Management for property of type password.
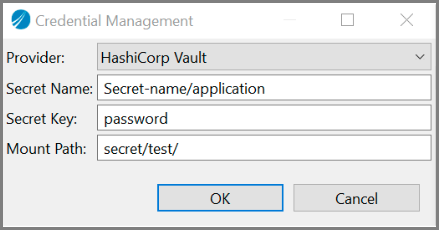
On TIBCO Business Studio™ for BusinessWorks™, the format is stored as #Secret_Name::Secret_key::Mount_Path#
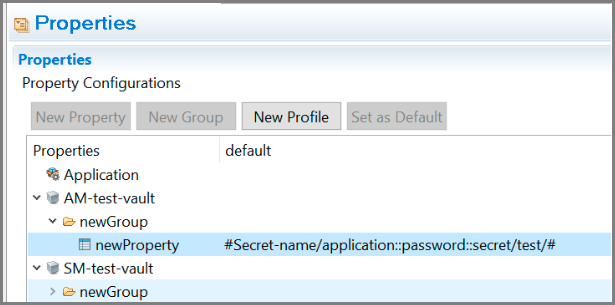
- HASHICORP_VAULT_ADDR
- HASHICORP_VAULT_AUTH
- VAULT_AUTH_PATH
- HASHICORP_VAULT_KV_VERSION
- APP_CONFIG_PROFILE
The authentication methods supported for HashiCorp Vault are Token, AppRole, and Userpass.
Secrets engines are components which store, generate or encrypt data. Some secrets engines simply store and read data while others connect to services and generate dynamic credentials on demand. Other secrets engines also provide encryption as a service. Secrets engines are enabled at a "path" in the Vault. When a request comes to the Vault, the router automatically routes anything with the route prefix to the secrets engine. The supported secret engine currently is Key Value Engine.
The KeyValue (KV) engine is the supported secret engine for HashiCorp Vault. The default engine used is the KeyValue (KV) engine version 2. If the HASHICORP_VAULT_KV_VERSION environment variable is set to 1, KeyValue (KV) engine version 1 is used.
HTTPS Support:
The HASHICORP_CACERT environment variable needs to be set to the path of the certificate.
In TIBCO Business Studio™ for BusinessWorks™ provide the path of the certificate in the HASHICORP_CACERT environment variable.
In Docker, place the certificate in the /resources/addons/certs/ folder.