Using AWS Secret Manager for Credential Management Service
AWS provides AWS Secret Manager Service for easier management of secrets. Secrets can be database credentials, passwords, third-party API keys, and arbitrary text. Secrets Manager is used to replace hardcoded credentials in the code, including passwords, with API calls to Secrets Manager to retrieve the secret programmatically.
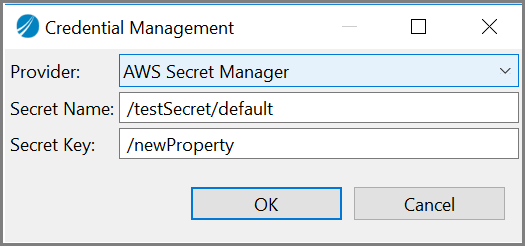
A new AWS Secret Manager provider is added for the Credential Management for property of type password.
The AWS Secret Manager has two fields, Secret Name and Secret Key. In the Secret Name and Secret Key fields , add the secret name and secret key that is to be retrieved from the AWS secret manager.
On the AWS systems manager console or using AWS CLI, the password properties need to be stored in AWS secret manager. The recommended format is to have secret name as/<applicationModule_name/<profile_name>.This makes sure that the property names are unique within the AWS secret manager as well as within the application. However other names can be used. The recommended format is using secret key as the /<property_name>
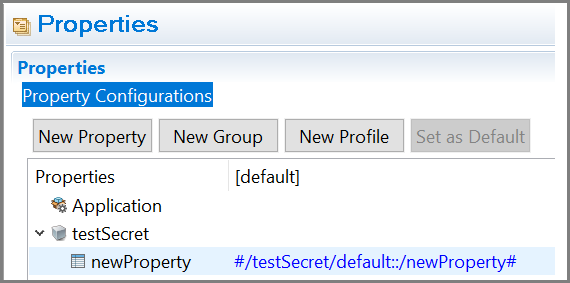
The secret name can either be the application module name or the shared module name along with the profile name, and the secret key is the key whose value is to be retrieved from AWS secret manager. On TIBCO Business Studio™ for BusinessWorks™, the format is stored as <secret_name>::<secret_key>.
For example, #/testSecret/default::/newProperty#.
Procedure
- Set the environment variables AWS_ACCESS_KEY, AWS_SECRET_KEY,AWS_REGION, AWS_SECRET_MANAGER, and APP_CONFIG_PROFILE. The AWS_ACCESS_KEY and AWS_SECRET_KEY environment variables are used as credentials for authentication. In order to enable assume role, the following additional environment variables should be passed, AWS_ROLE_ARN, AWS_ROLE_SESSION_ARN, AWS_EXTERNAL_ID (optional), and AWS_EXPIRATION_ID (optional). For more information on the environment variables, see Environment Variables for Docker.
- In the application properties section, select the Credential Management option, and select AWS Secret Manager and the value gets populated with the following format <secret_name>::<secret_key>.
Integrating ECS Services with AWS Secret Manager
Support for credential management service for AWS Secret Manager is provided while deploying application on ECS service.