Using Conjur for Credential Management Service
CyberArk Conjur is used to integrate with TIBCO BusinessWorks™ Container Edition for password management which enables a TIBCO BusinessWorks Container Edition application to retrieve passwords from Conjur when a password is needed at runtime. This avoids adding any passwords during deploying configuration or redeploying the application.
Conjur manages the secrets required by applications and other non-human identities to gain access to critical infrastructure, data and other resources. Conjur secures this access by managing secrets with granular Role-Based Access Control (RBAC) and other security best practices and techniques.
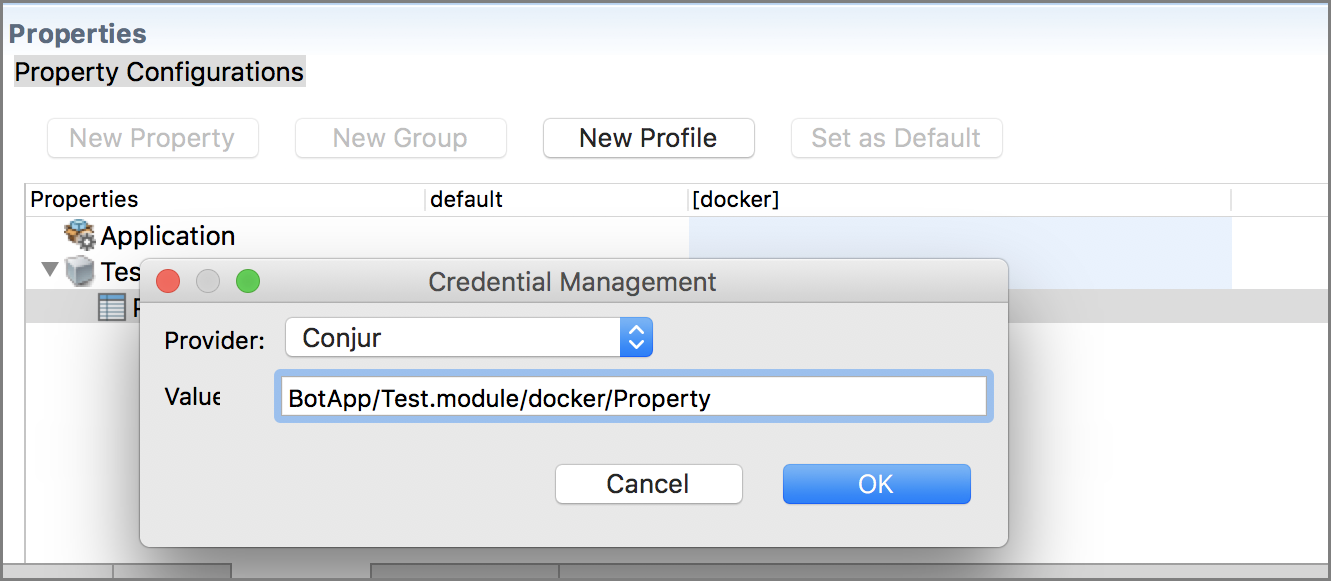
On the Conjur Server, the recommended name for secrets is <applicationModule_name>/<profile_name>/<property_name>. This ensures the property names are unique within the Conjur Server as well as in the application. However, other names can also be used.
In application properties, a new Conjur provider is added for Credential Management. To retrieve a secret from the Conjur Server enter the name of the secret.
For more informaton on the environment variables, see Environment Variables.
SSL Verification
By default, the Conjur appliance generates and uses self-signed SSL certificates (Java-specific certificates known as cacerts). This certificate should be loaded into Java's CA keystore that holds the list of all the allowed certificates for HTTPS connections. This certificate can be obtained by using the Conjur CLI.
Run the following command from the Conjur CLI to initialize Conjur in order to retrieve Conjur certificates:
conjur init
While running the command on docker, the certificate needs to be added in the /resources/addons/certs folder.
While running the command on TIBCO Business Studio™ for BusinessWorks™, the certificate needs to be added to the Java CA keystore located at BW_HOME/tibcojre64/1.8.0/lib/security/cacerts.
To disable the SSL Verification pass the following environment variable
CONJUR_DISABLE_SSL= true