Overview
You can use TIBCO ActiveMatrix BusinessWorks™ Plug-in for Confidentiality to encrypt data in your processes to handle sensitive data in a TIBCO ActiveMatrix BusinessWorks™ application. You can configure the security providers, keystores, encryption, and decryption algorithms. ActiveMatrix BusinessWorks™ Plug-in for Confidentiality includes a set of XPath functions to encrypt, decrypt, and mask data.
Encryption and Decryption
The plug-in supports encryption and decryption of data by using AES(Advanced Encryption Standard) and DESede(Triple Data Encryption Standard) algorithms. The plug-in supports a combination of algorithm, mode and padding, based on the security provider. BouncyCastle FIPS(Federal Information Processing Standards) is a supported security provider. The plug-in provides flexibility to configure all the configuration parameters. A key stored on the key store is used to encrypt and decrypt the input based on the selected algorithm, mode, and padding.
The following figure shows the encryption process. Plain text is encrypted by using the key from the key store and by applying an encryption type which is a combination of algorithm, mode, and padding to generate the cipher text as an output.
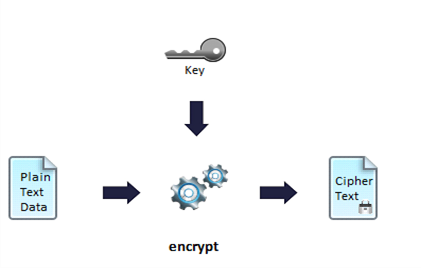
The following figure shows the decryption process. Cipher text is decrypted by using the same key stored in the key store and by applying an encryption type which is a combination of the same algorithm, mode, and padding, provided at the time of encryption, to generate the original plain text.

Two-Key Encryption and Decryption
The plug-in also provides a two-key encryption and decryption approach where the data key and master key are used for encryption and decryption.
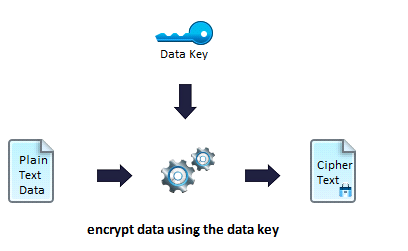
The following figure shows the two-key encryption approach. For each plain text input given to the XPath function, the plug-in internally generates a data key. The key from the key store is treated as a master key and is used to encrypt the generated data key.
Plain text is encrypted by using the internally generated data key and encryption type which is a combination of algorithm, mode, and padding, provided through the Confidentiality Shared Resource.
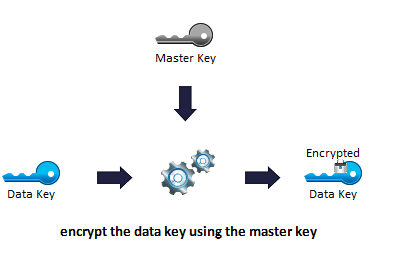
The internally generated data key is encrypted by using the master key from the key store and encryption type which is a combination of algorithm, mode, and padding(AES/CBC/PKCS5Padding).
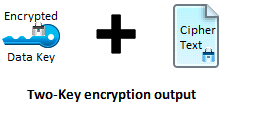
The encrypted data key and the cipher text is the final output.
In the two-key decryption approach, the encrypted data key is decrypted by using the master key provided through the Confidentiality Shared Resource. Using the same encryption type which is a combination of algorithm, mode, and padding, and the decrypted data key, the input cipher text is decrypted to the original plain text.
Mask Data
The maskString XPath function is used to mask a string and the maskDocumentField XPath function is used to mask a field in the XML or JSON file. For example, these mask functions can be used to mask the digits of a credit card or any other sensitive data.
