Using the Built in mTLS Based Authentication Service
mTLS (Mutual transport layer Security) allows client-to-server or server-to-server connections to authenticate each other during the TLS handshake. mTLS in FTL requires user-defined certificates.
For details, see: Enabling TLS for FTL Server
The picture below shows interactions between client and server during mTLS based authentication.
Figure 39: Built in mTLS based authentication
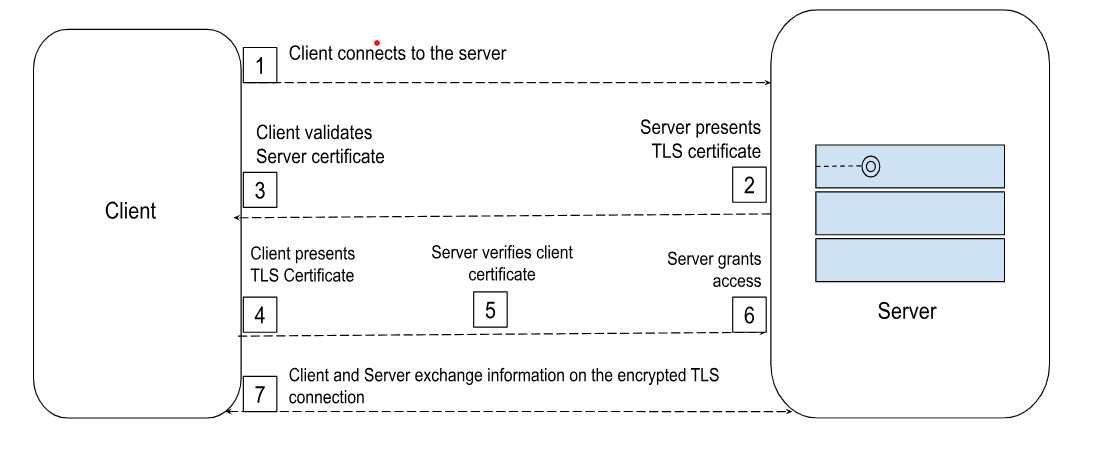
In order to enable mTLS for incoming connections, the ‘auth.providers’ in the FTLServer yaml configuration must include ‘mtls’ as one of the providers. In addition, configure the "tls.server.trust.file parameter in the FTL server yaml configuration file.
For details, see FTL Server Configuration Parameters
Ensure that TLS with user-defined certificates is also configured, see Enabling TLS for FTL Server
When a client or another FTL server connects to FTL server and sends its client certificate, FTL server will verify the client certificate using tls.server.trust.file.
If the certificate is valid, FTL server will then parse the common name (CN) of the certificate. The CN must be a string in the following format:
<username>:<role1>[,<role2>,...]
For example, here are some valid common names:
admin:ftl-admin
internal:ftl-internal
subcribe-user:ftl,sub
The username and roles in the CN string become the username and roles for the incoming client or FTL server.
See samples/yaml/mtls in the FTL installation for example yaml configurations and certificates. See samples/yaml/certs in the FTL installation for an example of how to generate certificates for mTLS.
Some key points to consider while using mTLS
-
When accessing the REST API, the REST client may authenticate itself with a client certificate
-
mTLS is not supported for the UI, so another authentication provider must be configured to support UI users.
-
mTLS is not supported for eFTL clients or the eFTL REST API.