Example 2- Calling an Inbound Web Service Operation Using SOAP/HTTP and Basic Authentication
This section describes:
| • | Aims of the Example |
| • | Looking at the getNodeName_SOAP Process |
| • | How to Run the Example |
Aims of the Example
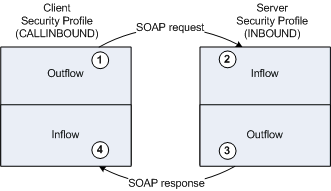
The following example shows a loopback test that demonstrates how basic authentication works when enabled for both inflow and outflow:
| 1. | The Web Service Client has a security profile callinbound that specifies a username and password for outflow security. The username - password token is inserted into the SOAP request to the Server. |
| 2. | The Server has a security profile Inbound to deal with SOAP requests. The username and password in the SOAP Request must match the username and password specified for Inflow security defined in the Inbound profile. |
| 3. | The Server sends the SOAP response with the username - password token specified for Outflow Security defined in the Inbound profile. |
| 4. | The Client receives the SOAP response and compares the received username and password to those specified for Inflow Security in the callinbound security profile. The usernames and passwords must match. |
Looking at the INBOUND Procedure
-
The INBOUND Procedure has three steps:
-
The first step, RELEASE displays a form stating that the Procedure will next call Inbound web service getNodeName. The Web Services step GETNODE performs the call, and OUTPUT displays the result.
-
Double-click GETNODE to see how the call-out is defined.
-
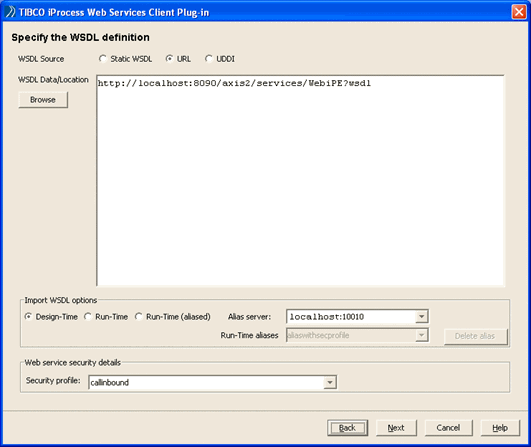
Note that in the Specify the WSDL definition dialog, the WSDL is obtained via URL from localhost. If this is not the case for your environment, modify the URL as necessary. Also make sure that you have the correct Alias server selected (if you do not, you will not be able to see the example security profile that you imported in Task 6: Import the Example Security Profiles. Note that the security profile is defined as callinbound.
| 5. | Examine the callinbound security profile by starting the Security Profile Administrator - run the JETTY_HOME\securitymanager script (on Windows, securitymanager.cmd, on UNIX, securitymanager.sh). |
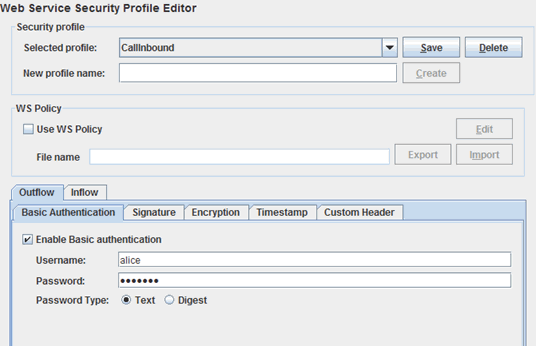
| 6. | The Outflow security of callinbound specifies alice as the username. This username and password will be applied to the SOAP request from the INBOUND Procedure to the iProcess Web Service. |
| 7. | Now examine the Inflow portion of the Inbound security profile. You can see that this also specifies alice as the username. This means that if the passwords match, the SOAP request will be authenticated. |
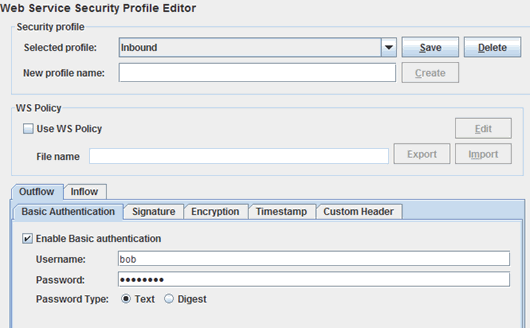
| 8. | The SOAP response (from getNodeName) will have the security specified on the Outflow portion of the Inbound profile. This specifies bob as the username. |
| 9. | Now examine the Inflow portion of the callinbound security profile. You can see that this also specifies bob as the username. This means that if the passwords match, the SOAP response will be authenticated. |
How to Run the Example
To run this example, do the following:
-
Start a case of the INBOUND procedure.
-
Release the first form step.
-
The node name returned by getNodeName is displayed in a form.
-
The Jetty log file (log.txt) located in the following directory shows messages related to the authentication of the username and password:
SWDIR/jetty-9.4.35/tibco
-
The Case Administrator also shows information about the processing of the case.