Creating a Connection using Authentication and/or Encryption Mode
You can encrypt the information delivered between LogLogic® Universal Collector and LMI server or syslog server.
To secure communication between LogLogic® Universal Collector and LMI or Syslog server, authentication between LogLogic® Universal Collector and LMI or Syslog server must be done using public and private key mechanism. Communication between LogLogic® Universal Collector and LMI or Syslog server must be encrypted.
Note: If you must use AES192 or AES256 key, you must install the Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 7 package from Oracle. The 2 JAR files included in this package must be loaded into the
lib/security directory of the Java instance that
LogLogic® Universal Collector uses to utilize AES192 or AES256 key ciphers. If you do not have JCE installed, then the
LogLogic® Universal Collector Console will fail when you try to import an AES192 or AES256 key.
As a requirement, you need a Public Key Infrastructure (PKI), OpenSSL or other compatible tools.
Procedure
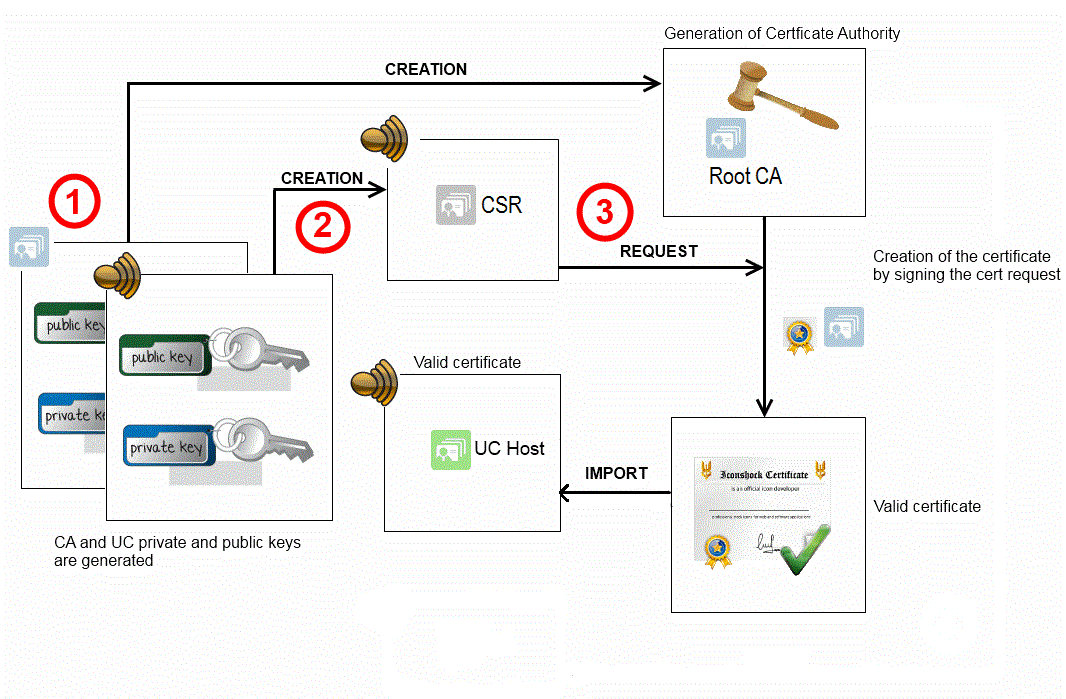
- A public key and a private key are used to create a Root Certificate Authority (Root CA).
- A public key and a private key are generated to create the Certificate Signing Request (CSR) of LogLogic® Universal Collector.
- This request will be sent along with the identity information of LogLogic® Universal Collector and the public key and then the Root CA creates the certificate by signing the Certificate Signing Request. The certificate of LogLogic® Universal Collector is sent with the Authority’s certificate.
Copyright © Cloud Software Group, Inc. All rights reserved.