Step 5 Configure the Forwarding Process
If the connection is authenticated or encrypted, the necessary cryptographic elements must be imported.
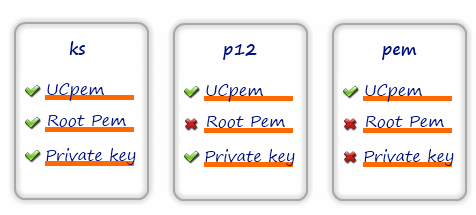
The three supported formats are:
- *.ks--A keystore in the JKS format containing the root CA, the private key and the associated
LogLogic® Universal Collector certificate.
Associated configuration elements are a keystore file name and a password for the keystore (mandatory)
- *.p12--A keystore in the PKCS#12 format, containing the private key and the associated
LogLogic® Universal Collector certificate and the root CA (in *.pem format) as a separate file.
Associated configuration elements are a PKCS#12 (.p12) file, a password protected PKCS#12 file (mandatory) and a root CA file.
- *.pem--A private key (encrypted or not), a certificate to be used by
LogLogic® Universal Collector in PEM format, a root CA certificate in PEM format. Associated configuration elements are a private key file, a password if the private key is encrypted (mandatory), a
LogLogic® Universal Collector certificate file, a root CA certificate file.
The Certificate Authority’s certificate allows to check the validity of LogLogic LMI or syslog server’s certificate towards LogLogic® Universal Collector.
The LogLogic® Universal Collector valid certificate allows you to identify LogLogic® Universal Collector from LogLogic LMI.
Procedure
Copyright © Cloud Software Group, Inc. All rights reserved.