One-Way HTTPS Client Configuration
Use the following steps to set up a one-way HTTPS client configuration.
- From
Endpoints > Endpoint > HTTPS Client Profile select
one_way_profile_001.
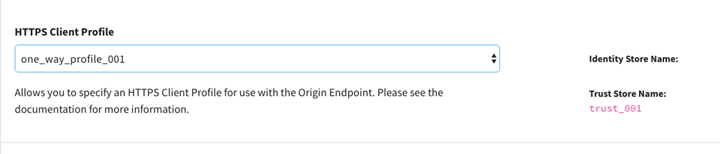
- Click Save then click the Home link.
- Export the changes to a folder, for example:
<User-home>/api-config/
A new data.zip will be created in the folder.
- Copy the data.zip file from <User-home>/api-config/ to <install-root>/tmgc-deploy/properties folder.
- Follow the rest of the installation process as documented in the Installation guide.
Once the ML cluster is up and running, follow the next steps.
- Log in to the CLI container. This example uses the Kubernetes deployment.
kubectlexec-it cm-deploy-0-76ffbdbb6b-jjb44envCOLUMNS=$COLUMNS LINES=$LINES TERM=$TERMbash
- Narrow down the scope of operations using the command line interface as seen below.
[root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager ls clusters Cluster ID Cluster Name ------------------------------------- -------------------- 6b08d0e3-637e-4e18-b628-2b934db0abfc Tibco Mashery Loc... [root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager use cluster 6b08d0e3-637e-4e18-b628-2b934db0abfc Using cluster [Tibco Mashery Local Reference Cluster] [root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager ls zones Using cluster [Tibco Mashery Local Reference Cluster] Zone ID Zone Name ------------------------------------- -------------------- 0f7c76d8-feb6-4d65-8dd9-532e43fe7eef local [root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager use zone 0f7c76d8-feb6-4d65-8dd9-532e43fe7eef Using cluster [Tibco Mashery Local Reference Cluster] Using Zone [local]
- Upload the Truststore certificate.
- List all certificates:
[root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager ls certificates clusterId [6b08d0e3-637e-4e18-b628-2b934db0abfc] and zoneId [0f7c76d8-feb6-4d65-8dd9-532e43fe7eef] Using cluster name [Tibco Mashery Local Reference Cluster] Using Zone name [local] UUID Name Area ID Expiration ---------------------------------------- ------------- ---------- -------------------- cb4d2bc2-f863-440b-1001-1d11369404d8 trust_001 0 cb4d2bc2-f863-440b-1002-1d11369404d8 trust_002 0 cb4d2bc2-f863-440b-1003-1d11369404d8 trust_003 0 cb4d2bc2-f863-440b-1004-1d11369404d8 trust_004 0 cb4d2bc2-f863-440b-1005-1d11369404d8 trust_005 0 cb4d2bc2-f863-440b-1006-1d11369404d8 trust_006 0 cb4d2bc2-f863-440b-1007-1d11369404d8 trust_007 0 cb4d2bc2-f863-440b-1008-1d11369404d8 trust_008 0 cb4d2bc2-f863-440b-1009-1d11369404d8 trust_009 0 cb4d2bc2-f863-440b-1010-1d11369404d8 trust_010 0 cb4d2bc2-f863-440b-1011-1d11369404d8 trust_011 0 cb4d2bc2-f863-440b-1012-1d11369404d8 trust_012 0 cb4d2bc2-f863-440b-1013-1d11369404d8 trust_013 0 cb4d2bc2-f863-440b-1014-1d11369404d8 trust_014 0 cb4d2bc2-f863-440b-1015-1d11369404d8 trust_015 0 cb4d2bc2-f863-440b-1016-1d11369404d8 trust_016 0 cb4d2bc2-f863-440b-1017-1d11369404d8 trust_017 0 cb4d2bc2-f863-440b-1018-1d11369404d8 trust_018 0 cb4d2bc2-f863-440b-1019-1d11369404d8 trust_019 0 cb4d2bc2-f863-440b-1020-1d11369404d8 trust_020 0 cb4d2bc2-f863-440b-1021-1d11369404d8 trust_021 0 cb4d2bc2-f863-440b-1022-1d11369404d8 trust_022 0 cb4d2bc2-f863-440b-1023-1d11369404d8 trust_023 0 cb4d2bc2-f863-440b-1024-1d11369404d8 trust_024 0 cb4d2bc2-f863-440b-1025-1d11369404d8 trust_025 0 cb4d2bc2-f863-440b-1026-1d11369404d8 trust_026 0 cb4d2bc2-f863-440b-1027-1d11369404d8 trust_027 0 cb4d2bc2-f863-440b-1028-1d11369404d8 trust_028 0 cb4d2bc2-f863-440b-1029-1d11369404d8 trust_029 0 cb4d2bc2-f863-440b-1030-1d11369404d8 trust_030 0 cb4d2bc2-f863-440b-1031-1d11369404d8 trust_031 0 cb4d2bc2-f863-440b-1032-1d11369404d8 trust_032 0 cb4d2bc2-f863-440b-1033-1d11369404d8 trust_033 0 cb4d2bc2-f863-440b-1034-1d11369404d8 trust_034 0 cb4d2bc2-f863-440b-1035-1d11369404d8 trust_035 0 cb4d2bc2-f863-440b-1036-1d11369404d8 trust_036 0 cb4d2bc2-f863-440b-1037-1d11369404d8 trust_037 0 cb4d2bc2-f863-440b-1038-1d11369404d8 trust_038 0 cb4d2bc2-f863-440b-1039-1d11369404d8 trust_039 0 cb4d2bc2-f863-440b-1040-1d11369404d8 trust_040 0
Note that we selected Trust Store trust_001 to update as follows.
- Set the trust store certificate file to the trust_001 trust store entry.
- Copy the Trust store certificate file to the CLI container.
admin-MBP15:properties admin$ kubectl get pods NAME READY STATUS RESTARTS AGE cache-deploy-0-577f7d5c7b-42pfn 1/1 Running 0 47m cass-set-0-0 1/1 Running 0 48m cm-deploy-0-76ffbdbb6b-jjb44 1/1 Running 0 47m log-set-0-0 1/1 Running 0 47m mysql-set-0-0 1/1 Running 0 47m tm-deploy-0-5b584758bb-9m6cn 1/1 Running 0 47m admin-MBP15:properties admin$ kubectl cp ~/Downloads/samplecert.cer cm-deploy-0-76ffbdbb6b-jjb44:/usr/local/bin/
- Use the command line interface to update the trust store as seen below.
[root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager set certificate --uuid cb4d2bc2-f863-440b-1001-1d11369404d8 --file /usr/local/bin/samplecert.cer Updating certificate for cluster ID 6b08d0e3-637e-4e18-b628-2b934db0abfc and zone ID 0f7c76d8-feb6-4d65-8dd9-532e43fe7eef Successfully updated certificate for cluster ID 6b08d0e3-637e-4e18-b628-2b934db0abfc of zone ID 0f7c76d8-feb6-4d65-8dd9-532e43fe7eef Mutual HTTPS Client Configuration
- List all certificates:
Copyright © Cloud Software Group, Inc. All rights reserved.
