One-Way HTTPS Client Configuration
To create one-way HTTPS client configuration:
- Login the CLI container.
kubectlexec-it cm-deploy-0-76ffbdbb6b-jjb44envCOLUMNS=$COLUMNS LINES=$LINES TERM=$TERMbash
- In the command line interface, input the scope of operation as below:
[root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager ls clusters Cluster ID Cluster Name ------------------------------------- -------------------- 6b08d0e3-637e-4e18-b628-2b934db0abfc Tibco Mashery Loc... [root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager use cluster 6b08d0e3-637e-4e18-b628-2b934db0abfc Using cluster [Tibco Mashery Local Reference Cluster] [root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager ls zones Using cluster [Tibco Mashery Local Reference Cluster] Zone ID Zone Name ------------------------------------- -------------------- 0f7c76d8-feb6-4d65-8dd9-532e43fe7eef local [root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager use zone 0f7c76d8-feb6-4d65-8dd9-532e43fe7eef Using cluster [Tibco Mashery Local Reference Cluster] Using Zone [local]
- Upload the trust certificate.
- Copy the trust certificate file to the CLI container.
admin-MBP15:properties admin$ kubectl get pods NAME READY STATUS RESTARTS AGE cache-deploy-0-577f7d5c7b-42pfn 1/1 Running 0 47m cass-set-0-0 1/1 Running 0 48m cm-deploy-0-76ffbdbb6b-jjb44 1/1 Running 0 47m log-set-0-0 1/1 Running 0 47m mysql-set-0-0 1/1 Running 0 47m tm-deploy-0-5b584758bb-9m6cn 1/1 Running 0 47m admin-MBP15:properties admin$ kubectl cp ~/Downloads/samplecert.cer cm-deploy-0-76ffbdbb6b-jjb44:/usr/local/bin/
- Upload the trust certificate as shown:
[root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager create certificate --file /usr/local/bin/samplecert.cer Creating certificate for cluster ID 6b08d0e3-637e-4e18-b628-2b934db0abfc and zone ID 0f7c76d8-feb6-4d65-8dd9-532e43fe7eef Successfully created certificate for cluster ID 6b08d0e3-637e-4e18-b628-2b934db0abfc of zone ID 0f7c76d8-feb6-4d65-8dd9-532e43fe7eef
- For tethered mode, update the trust as shown:
[root@cm-deploy-0-76ffbdbb6b-jjb44 builder]# clustermanager set certificate --uuid cb4d2bc2-f863-440b-1001-1d11369404d8 --file /usr/local/bin/samplecert.cer Updating certificate for cluster ID 6b08d0e3-637e-4e18-b628-2b934db0abfc and zone ID 0f7c76d8-feb6-4d65-8dd9-532e43fe7eef Successfully updated certificate for cluster ID 6b08d0e3-637e-4e18-b628-2b934db0abfc of zone ID 0f7c76d8-feb6-4d65-8dd9-532e43fe7eef
- Copy the trust certificate file to the CLI container.
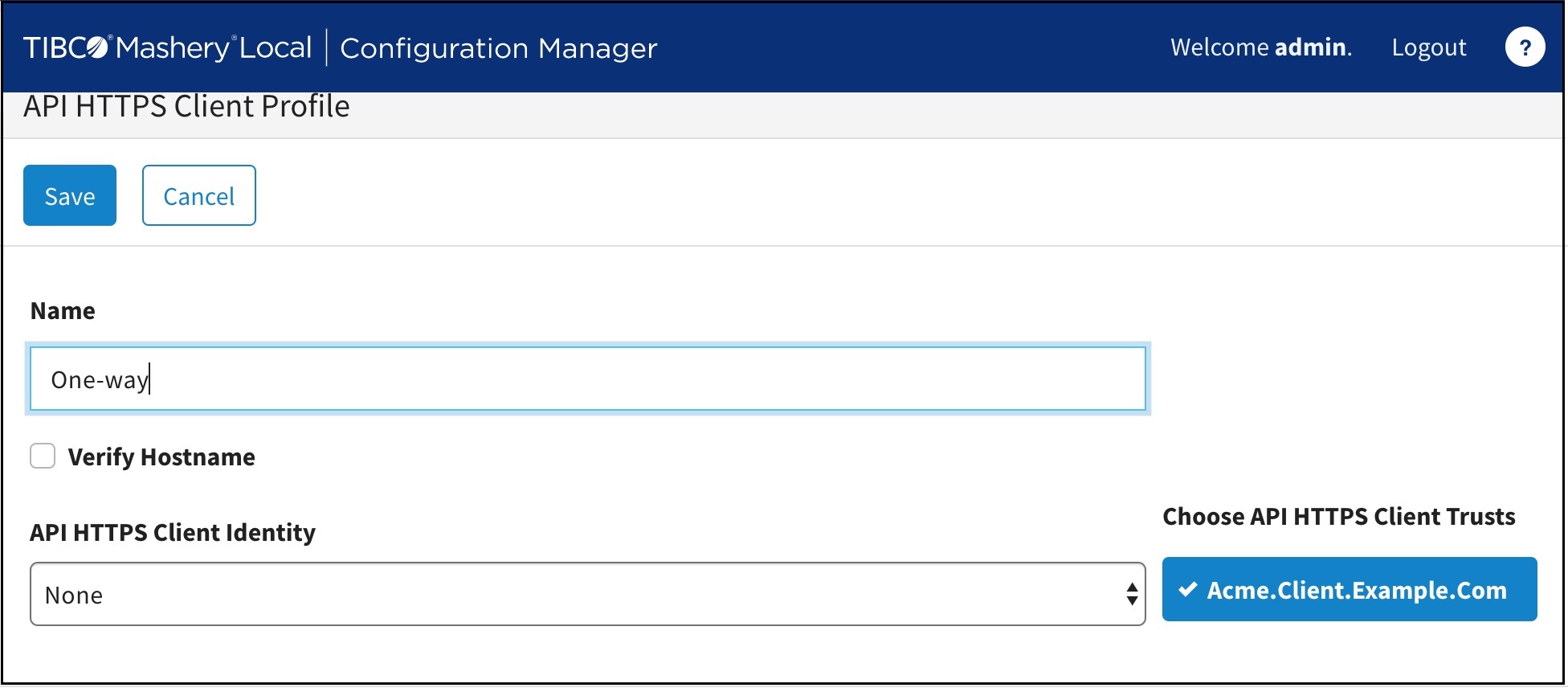
- Open the Configuration Manager and sign in. Create the new configuration.
Copyright © Cloud Software Group, Inc. All rights reserved.
