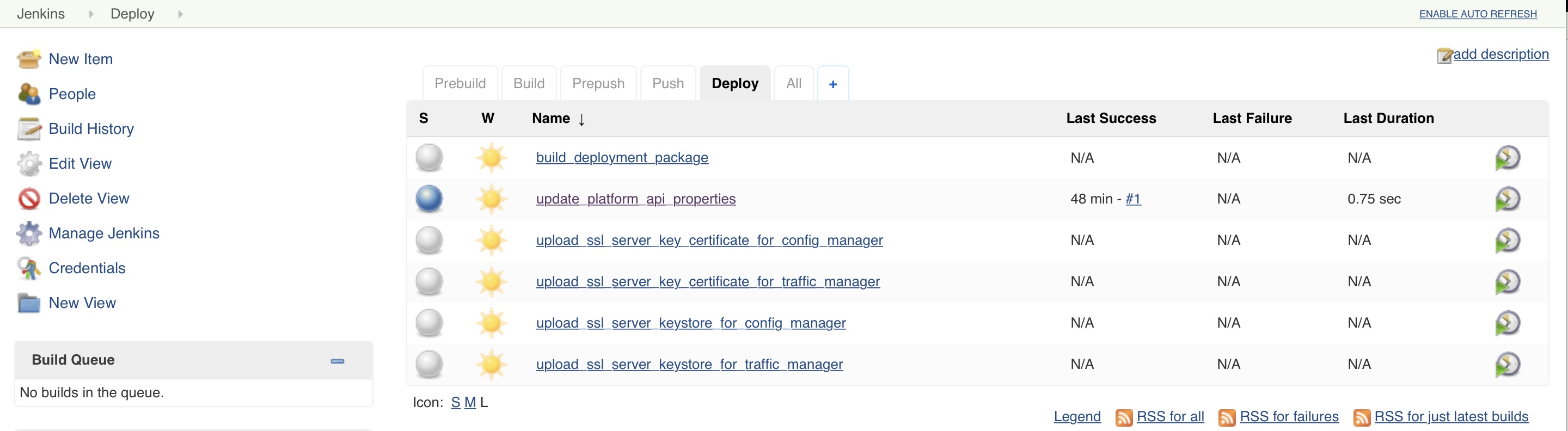
Customizing Deployment
The deployment artifacts can be optionally customized prior to deployment. If you do not customize the artifacts, all defaults take effect in the Mashery Local deployment.
The following can be customized prior to deployment:
Platform API Properties Customization
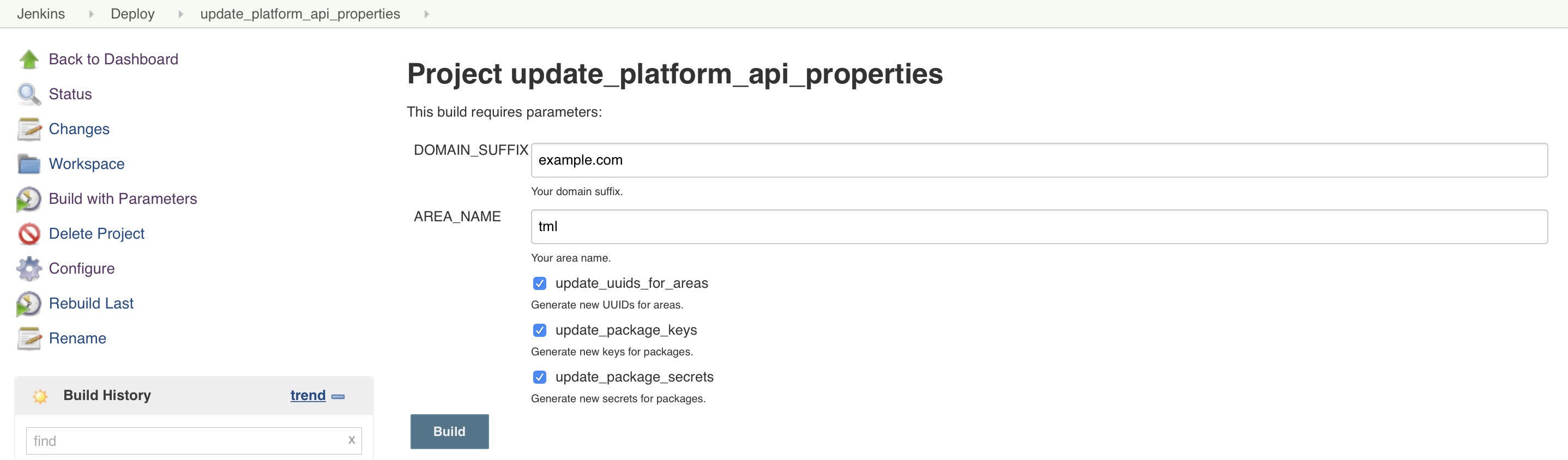
Platform API properties are customized using the update_platform_api_properties Jenkins job.
Using the update_platform_api_properties Jenkins job, you can:
The Jenkins job updates the /var/jenkins_home/docker-deploy/properties/tml_papi_properties.json file.
KeyStores for Traffic Manager Customization
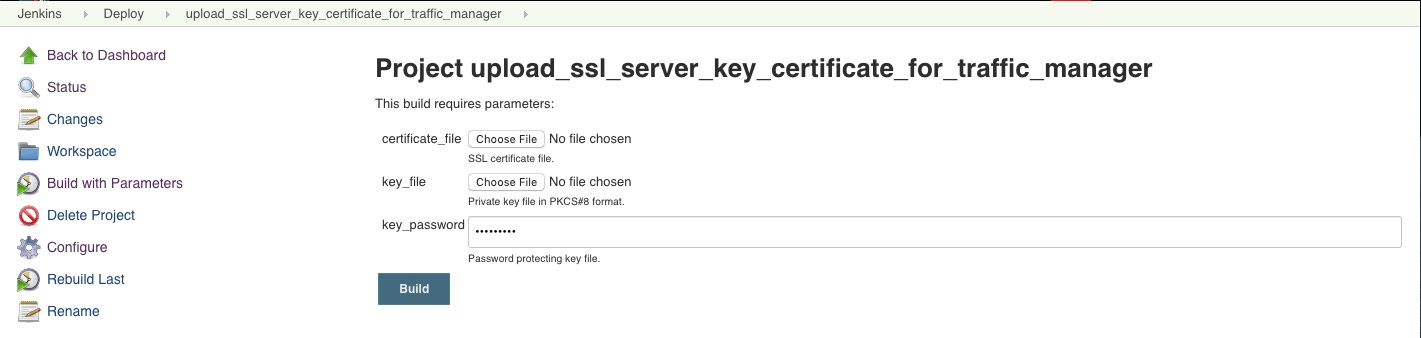
KeyStores for Traffic Manager can be customized using either the upload_ssl_server_keystore_for_traffic_manager or the upload_ssl_server_key_certificate_for_traffic_manager Jenkins job.
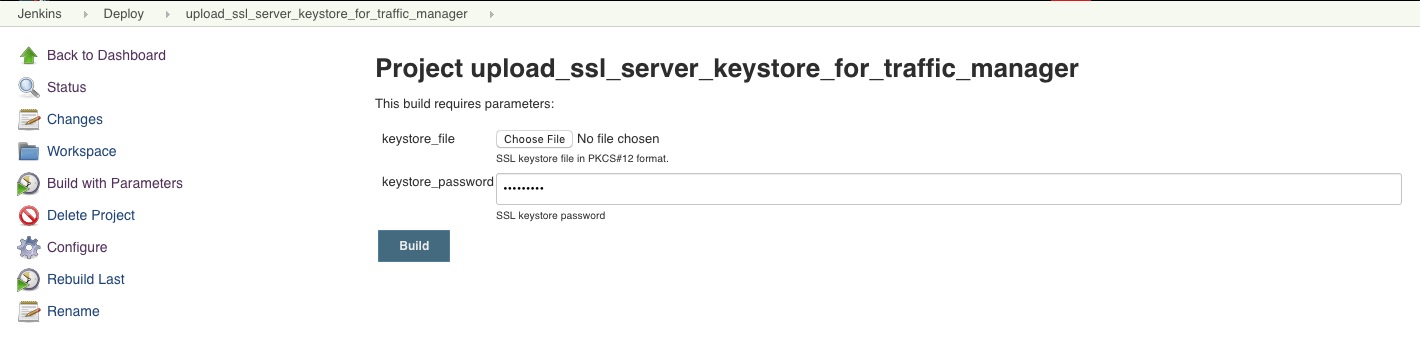
upload_ssl_server_keystore_for_traffic_manager
An Administrator must:
The upload_ssl_server_keystore_for_traffic_manager Jenkins job:
upload_ssl_server_key_certificate_for_traffic_manager
KeyStores for Config Manager Customization
KeyStores for Config Manager can be customized using either the upload_ssl_server_keystore_for_config_manager or the upload_ssl_server_key_certificate_for_config_manager Jenkins job.
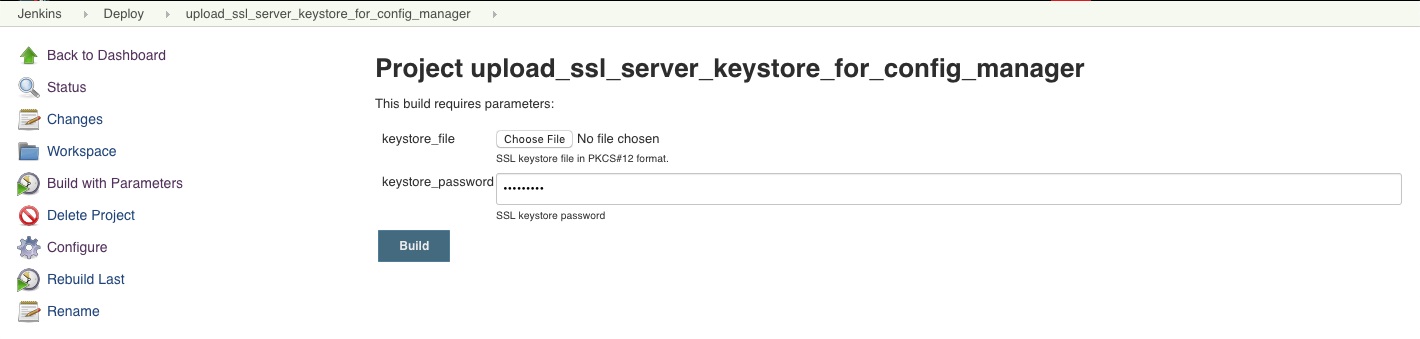
upload_ssl_server_keystore_for_config_manager
An Administrator must:
The upload_ssl_server_keystore_for_config_manager Jenkins job:
- converts the keyStore to JKS format from PKCS#12 format, then saves it as /var/jenkins_home/docker-deploy/properties/tml-cm.jks
- exports certificate as /var/jenkins_home/docker-deploy/properties/tml-cm-crt.pem
- exports the private key as /var/jenkins_home/docker-deploy/properties/tml-cm-key.pk8
- records the keyStore password in cm_keystore_password" of "/var/jenkins_home/docker-deploy/properties/tml_cm_properties.json
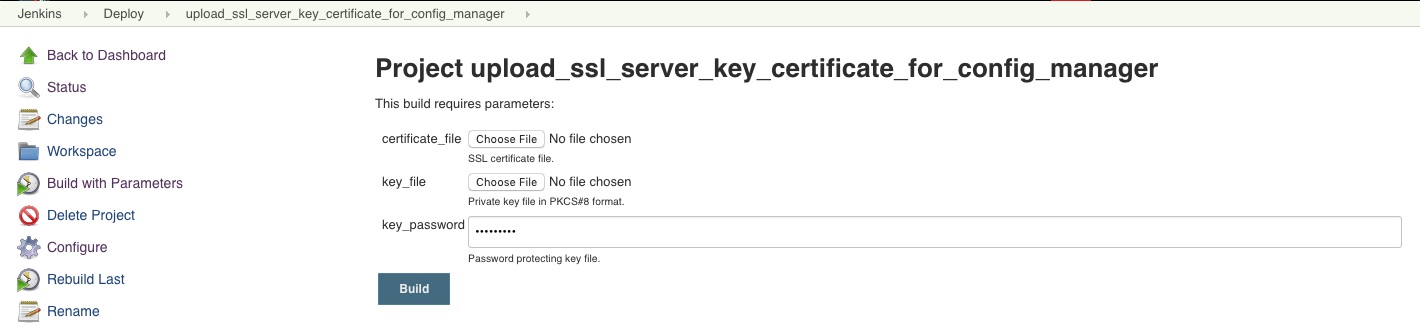
upload_ssl_server_key_certificate_for_config_manager
An Administrator must:
The upload_ssl_server_key_certificate_for_config_manager Jenkins job:
- saves the certificate as /var/jenkins_home/docker-deploy/properties/tml-cm-crt.pem
- saves the private key as /var/jenkins_home/docker-deploy/properties/tml-cm-key.pk8
- converts the certificate and private key to the keyStore to JKS format, then saves it as /var/jenkins_home/docker-deploy/properties/tml-cm.jks
- records the keyStore password in cm_keystore_password in /var/jenkins_home/docker-deploy/properties/tml_cm_properties.json
Build Deployment Package
You can either deploy the Mashery Local cluster inside the Mashery Local installer, or you can build and download the deployment package, then deploy the Mashery Local cluster from anther host.
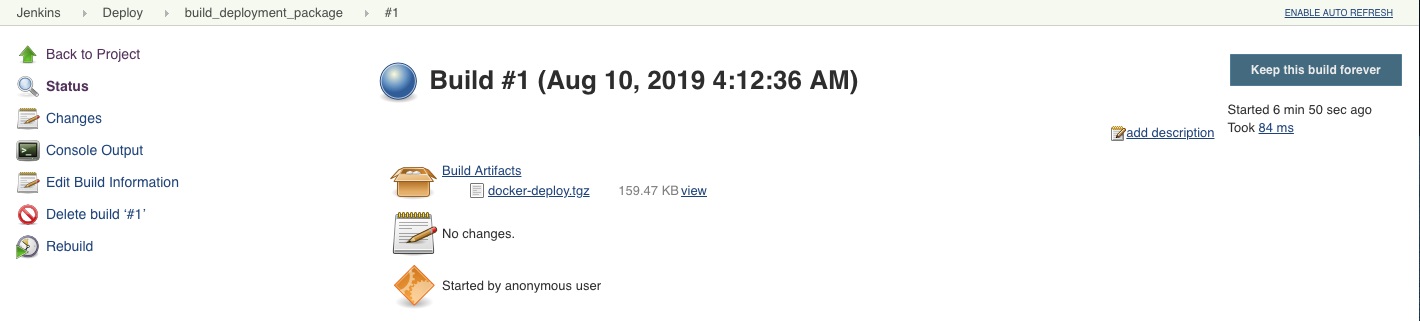
To build the deployment package, click Build Artifacts in the build_deployment_package Jenkins job:
The deployment package, docker-deploy.tgz, is available for download from the build archive. The package includes keyStores, keys, and certificates.
Mashery Local Properties Customization
From the host where Mashery Local installer is running, run the following to login to Mashery Local installer:
docker exec -it tml-installer /bin/bash sudo -s
or
docker exec -it -u root tml-installer /bin/bash
You can customize properties for the Mashery Local components as follows:
- Cluster-level properties - These are common properties that can apply throughout the entire cluster. for example. for MySQL and MoM sync credentials. These can be customized at
/var/jenkins_home/docker-deploy/properties/tml_cluster_properties.json.
MySQL passwords
"mysql_root_pwd": "changeme", "mysql_masheryonprem_pwd": "changeme", "mysql_mashonpremrepl_pwd": "changeme", "mysql_mashclient_pwd": "changeme", "mysql_masherybackup_pwd": "changeme",
MoM access
"mom_server": "https://api-mom.mashery.com", "mom_key": "", "mom_secret": ""
- Zone-level properties - These are common properties that can apply within a zone, but not necessarily throughout the entire cluster, for example, MOM credentials. These can be customized at
/var/jenkins_home/docker-deploy/properties/tml_zones_properties.json.
The following shows the default values for the zone-level properties:
[ { "zone_serial": "0", "mom_server_proxy_host": "", "mom_server_proxy_port": 3128, "mom_server_proxy_username": "", "mom_server_proxy_password": "", "target_server_proxy_host": "", "target_server_proxy_port": 3128, "no_proxy_pool": "" }, { "zone_serial": "1", "mom_server_proxy_host": "", "mom_server_proxy_port": 3128, "mom_server_proxy_username": "", "mom_server_proxy_password": "", "target_server_proxy_host": "", "target_server_proxy_port": 3128, "no_proxy_pool": "" }, { "zone_serial": "2", "mom_server_proxy_host": "", "mom_server_proxy_port": 3128, "mom_server_proxy_username": "", "mom_server_proxy_password": "", "target_server_proxy_host": "", "target_server_proxy_port": 3128, "no_proxy_pool": "" } ]You can set an HTTP Proxy for MoM access per zone using these properties:
"mom_server_proxy_host": "", "mom_server_proxy_port": 3128, "mom_server_proxy_username": "", "mom_server_proxy_password": "",
You can set an HTTP Proxy for accessing target servers per zone using these properties:
"target_server_proxy_host": "", "target_server_proxy_port": 3128, "no_proxy_pool": ""
Note that zone is identified by zone_serial. You can tailor the property JSON according to the number of zones to which the Mashery Local cluster will be deployed. Zone properties for zone whose zone_serial is above the actual number of deployed zones will not be used.