The MFT Server supports HTTPS certificate authentication.
Prerequisites
To enable HTTPS certificate authentication, you must create a private key and associate the private key with the browser. Each browser has a different way of handling private keys. This document does not describe how to associate a private key with a browser.
Procedure
-
Update
<MFT-Install>/server/conf/server.xml.
-
Locate the HTTPS connector.
-
Change parameter
clientAuth =
false to
clientAuth =
want. This allows certificate or password authentication to the server.
-
Restart the MFT Internet Server or MFT Command Center Server.
-
Log on to the Internet Server or Command Center Admin console.
-
Navigate to
.
-
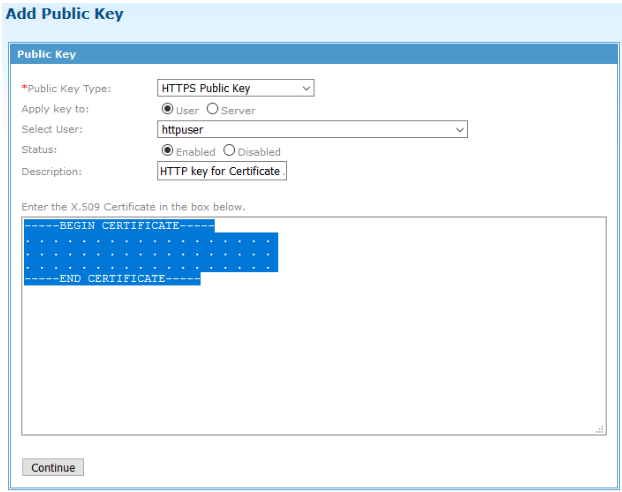
Set the
Public Key Type to
HTTPS Public Key.
-
Set
Apply Key to to
User.
-
Select the user to associate with the certificate.
-
Set
Status to
Enabled.
-
Set
Description to a unique descriptive value.
-
Copy/paste the certificate into the
Enter the X.509 Certificate in the box below input field.
-
Click
Continue.
The
Add Public Key Confirmation page is displayed.
-
Review the information and click
Continue.
The key is added to the server and associated with the defined user.
-
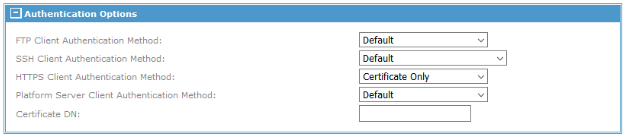
Navigate to
and select the user that requires certificate authentication.
-
Set
HTTPS Client Authentication Method to
Certificate Only.
-
Click
Update to save the changes.
-
Configure the browser to use certificate authentication.
When the browser connects to MFT, it displays a list of certificates that can be used.
-
Select the certificate to use and click
OK or
Continue.
Note: You should be logged onto the MFT Internet Server or Command Center.
Result
When a browser connects to Internet Server or Command Center, the server requests a certificate from the browser. It verifies the certificate against the HTTPS certificates added in prior steps. If a match is found, the logon request is successful. Otherwise, the logon request fails.
Copyright © 2021. Cloud Software Group, Inc. All Rights Reserved.