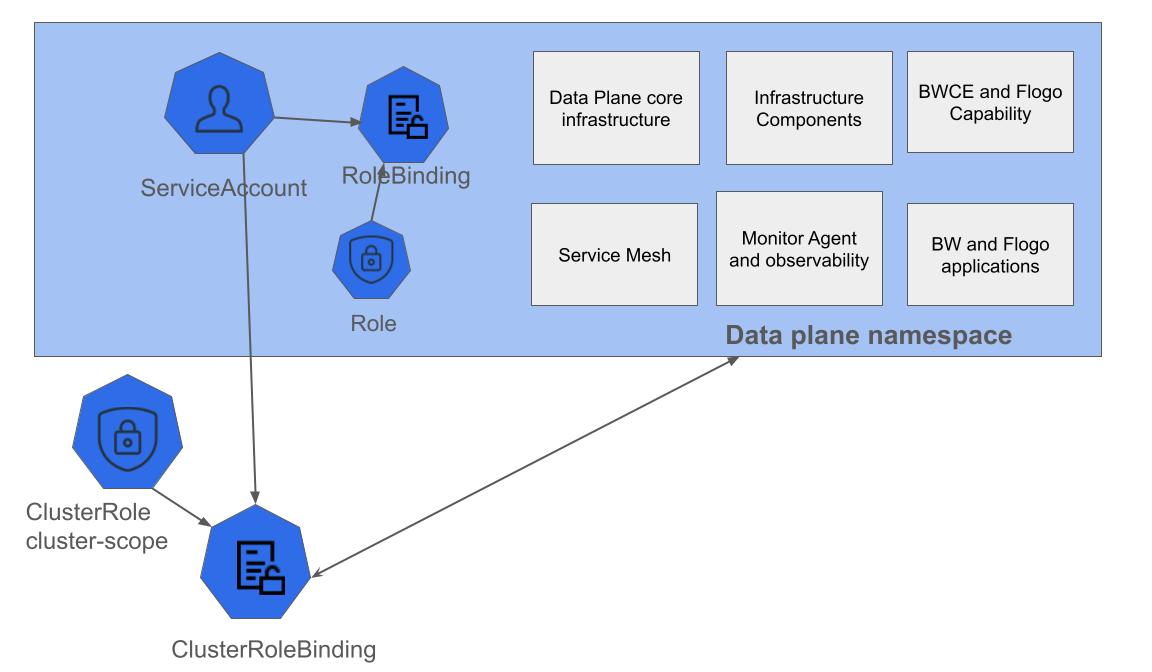
Data Plane RBACs
You can use Role Based Access Control (RBAC) to secure access to Kubernetes resources based on user roles. When you register a data plane, by default it creates ClusterRole, ClusterRoleBinding, Role, and RoleBinding for all capabilities as displayed in the following image. If you do not want to provision any capability, you can disable RBAC creation for that capability by using the parameters mentioned in the following table.
By default, service account has cluster-scope permissions. If you do not want to give cluster-scope permissions to service account, you can disable cluster-scope permissions when registering a data plane from TIBCO Control Plane UI. If you disable cluster-scoped permissions, cluster-scoped role-bindings are not created. It creates namespace-scoped Role and RoleBindings in the namespace where the dp-configure-namespace chart is deployed.
The following table describes the parameters you can specify in the service account creation command to enable or disable creation of RBAC for capabilities:
| Parameter | Description | Default |
|---|---|---|
rbac.bwce
|
Enables or disables creating RBAC for TIBCO BusinessWorks Container Edition capability | true |
rbac.flogo
|
Enables or disables creating RBAC for Integration - Flogo capability | true |
rbac.ems
|
Enables or disables creating RBAC for TIBCO Enterprise Message Service capability | true |
rbac.serviceMesh
|
Enables or disables creating RBAC for Service Mesh capability | true |
rbac.pulsar
|
Enables or disables creating RBAC for TIBCO Messaging Quasar capability | true |
rbac.devHub
|
Enables or disables creating RBAC for Developer Hub capability | true |
The following scenarios describe how you can configure RBAC per your needs:
If you want to provision all capabilities then there is no change in the Service Account creation command that is displayed on the last screen of data plane registration wizard.
To enable ClusterRole creation for a particular capability, you must disable creation of RBAC for other capabilities by setting the parameters specified in the preceding table.
For example, if you want to deploy TIBCO BusinessWorks Container Edition capability with ClusterRole, set the RBAC parameters for other capabilities as false in the service account creation command on the last screen of the data plane creation wizard.
Example service account creation command:
helm upgrade --install -n merci-01 dp-configure-namespace dp-configure-namespace --repo https://tibcosoftware.github.io/tp-helm-charts/gh-pages --set global.tibco.dataPlaneId=cnpatg4olrk2n9sq2jeg --set global.tibco.primaryNamespaceName=merci-01 --set global.tibco.serviceAccount=test-sa --set rbac.flogo=false --set rbac.ems=false --set rbac.serviceMesh=false --set rbac.pulsar=false --set rbac.devHub=false
To deploy a particular capability without ClusterRole, you must first disable the Allow cluster scoped permissions option in the data plane registration wizard. Then set the RBAC parameters for other capabilities as false in the service account creation command on the last screen of the data plane creation wizard.
For example, if you want to deploy TIBCO BusinessWorks Container Edition capability without cluster-scoped permissions then you can disable all the other RBACs in the Service Account creation command (this deploys TIBCO BusinessWorks Container Edition Role and RoleBinding only). As Allow cluster scoped permissions option is disabled in the data plane registration wizard, ClusterRole does not get created.
Example service account creation command:
helm upgrade --install -n test-ns dp-configure-namespace dp-configure-namespace --repo https://tibcosoftware.github.io/tp-helm-charts/gh-pages --set global.tibco.dataPlaneId=cnpatg4olrk2n9sq2jeg --set global.tibco.primaryNamespaceName=test-ns --set global.tibco.serviceAccount=test-sa --set rbac.flogo=false --set rbac.ems=false --set rbac.serviceMesh=false --set rbac.Pulsar=false --set rbac.devHub=false --set global.tibco.enableClusterScopedPerm=false
In this scenario, enable creation of RBAC for new capability by setting the capability RBAC parameter to true. Use --reset-then-reuse-values parameter to retain the RBACs of the already provisioned capability. For using --reset-then-reuse-values, Helm version 3.14 or later is required.
Example: Provision Service Mesh capability and retain RBACs of TIBCO BusinessWorks Container Edition which is already provisioned.
helm upgrade --install -n test-ns dp-configure-namespace dp-configure-namespace --repo https://tibcosoftware.github.io/tp-helm-charts/gh-pages --set global.tibco.dataPlaneId=cnpatg4olrk2n9sq2jeg --set global.tibco.primaryNamespaceName=test-ns --set global.tibco.serviceAccount=test-sa --set rbac.serviceMesh=true --reset-then-reuse-values
To upgrade a data plane registered in an earlier version to TIBCO® Control Plane 1.2.0, you must use --reset-then-reuse-values parameter in the upgrade command to to retain the RBACs of already provisioned capabilities.
Example service account creation command:
helm upgrade --install -n test-rbac dp-configure-namespace dp-configure-namespace --repo https://tibcosoftware.github.io/tp-helm-charts/gh-pages --set global.tibco.dataPlaneId=cnpcdu4olrk2n9sq2k30 --set global.tibco.primaryNamespaceName=test-rbac --set global.tibco.serviceAccount=test-rbac --reset-then-reuse-values
You can deploy apps in a different namespace than the data plane primary namespace. Primary namespace is used when registering a data plane.
Consider a scenario in which you have already deployed the data plane with TIBCO BusinessWorks Container Edition RBAC disabled in primary namespace. In this case, if you want to deploy TIBCO BusinessWorks Container Edition apps in another namespace, you must enable creation of TIBCO BusinessWorks Container Edition RBAC for the primary namespace.
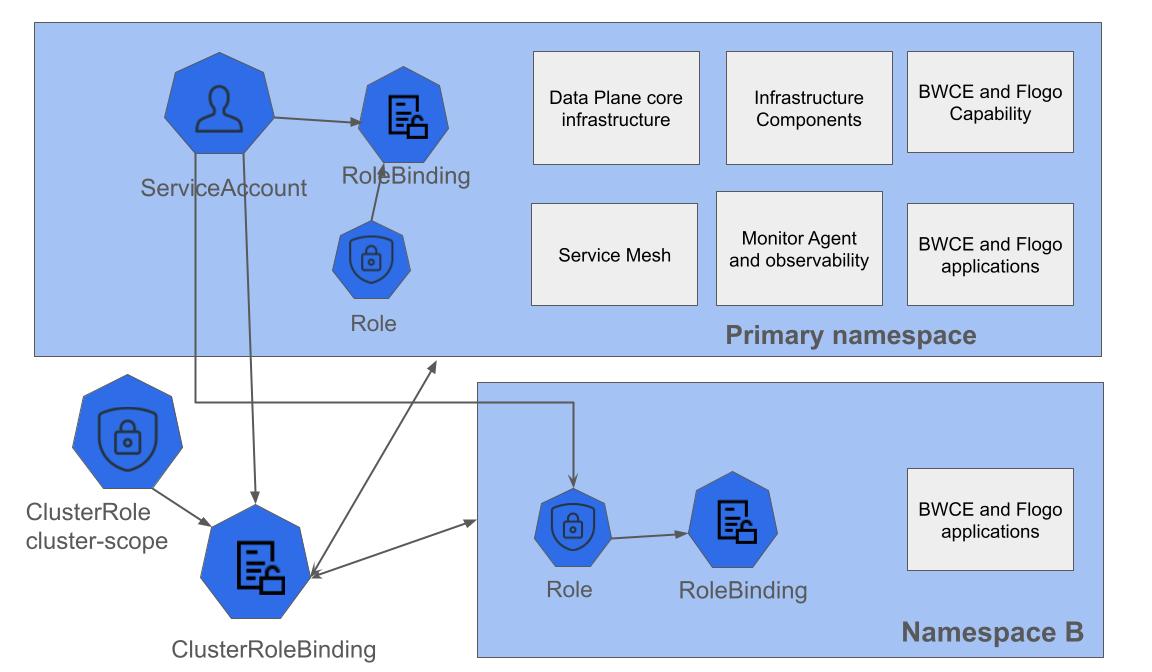
Example service account creation command:
helm upgrade --install -n test-rbac dp-configure-namespace dp-configure-namespace --repo https://tibcosoftware.github.io/tp-helm-charts/gh-pages --set global.tibco.dataPlaneId=cnpcdu4olrk2n9sq2k30 --set global.tibco.primaryNamespaceName=test-rbac --set global.tibco.serviceAccount=test-rbac --set rbac.bwce=true --set --reset-then-reuse-values
After the RBACs are enabled, you can deploy TIBCO BusinessWorks Container Edition app in a different namespace than the data plane namespace.