Concepts
In the context of border routing, the term first-tier router denotes the kind of router that is already familiar from the preceding sections of this chapter.
First-tier routers share a global routing table. Every first-tier router has its own copy of the entire routing table, spanning the entire routing network; any change in the routing network propagates to every router. In networks with many routers, the resulting overhead can be noticeable.
A border router or second-tier router is an rvrd process that can serve as a border, dividing a routing network into separate zones (see Zone, below).
You can configure a border router with neighbors and local networks (in the same way as you would configure a first-tier router). The border router connects these elements, and forwards messages among them.
A policy defines the set of subjects that a border router forwards from one of its neighbors or local networks (called the From interface) to another of its neighbors or local networks (the To interface). To configure policy, see Border Policy.
A border router can restrict a subject, forwarding only those messages that have not yet crossed a border; see First Border.
|
Note |
Adding an interface to a border router automatically creates a default policy for all pairings of existing interfaces with the new interface. The default policy allows forwarding of This behavior is automatic when you add a border router interface using either the browser administration interface, or these Java configuration API methods:
Nonetheless, you may explicitly remove this subject ( In contrast, specifying a new interface by editing an XML configuration overrides this default border policy. An XML document engenders a router configuration that matches the XML specification exactly; an interface will not have any border policy unless the XML document explicitly specifies one. |
A zone or first-tier routing network is a collection of routers and local networks, in which every pair in the collection is connected by a route that does not cross through a border router.
Administrators do not explicitly configure zones. Instead, border routers periodically examine the network, and dynamically partition it into zones based on network connectivity.
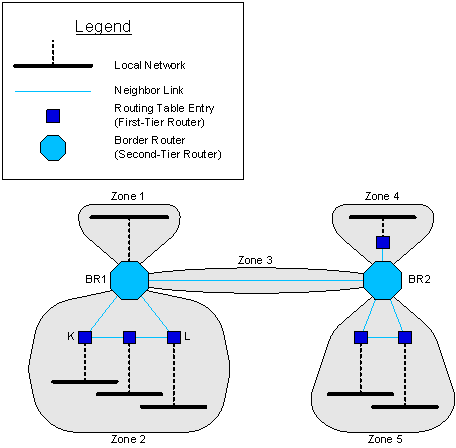
In Border Router: Concepts, border router BR1 has two first-tier neighbors (K and L), and a route connects those neighbors without crossing through BR1 nor any other border router; so K and L are in the same zone.
Figure 76: Border Router: Concepts
The effective policy of a zone is the union of the policies of all its constituents. In other words, a message that can enter or leave through any constituent can enter or leave the zone as a whole. For example, if BR1 allows foo.* to cross from K to BR2, then foo.* can cross from anywhere in zone 2 to anywhere in zone 3.
Each border router process embodies several implicit internal first-tier routers. When a border router automatically groups its neighbors and local networks into zones, it tacitly instantiates one first-tier router (within itself) for each zone that it serves.
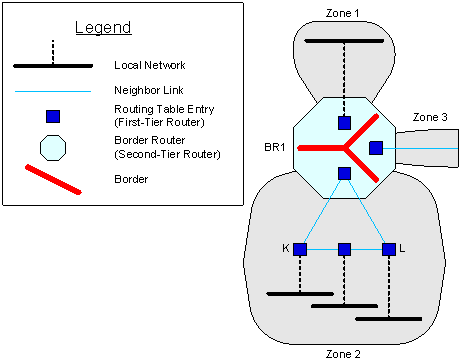
When we say that a border router participates in a zone, we really mean that one of the implicit first-tier routers within the border router participates in that zone. Border Router: Implicit Internal First-Tier Routers expands a portion of Border Router: Concepts; it illustrates that border router BR1 contains three implicit internal first-tier routers, which serve zones 1, 2 and 3. Each one participates in one zone, as a representative of BR1.
Figure 77: Border Router: Implicit Internal First-Tier Routers
Implicit first-tier routers are similar to the embodied routers described in Independent Routing Table Entries in One Process, except that you cannot configure them—the border router creates and configures them automatically. (Border routers can embody only implicit first-tier routers; they cannot configure explicit internal first-tier routers.)
Internal representatives of a border router are invisible to the external first-tier interfaces that they serve. All representatives of a border router present the same routing name, which is identical to the name of the border router (in our example, all three are named BR1). As a result, all external interfaces appear to communicate with BR1.
Within a border router, a border separates every pair of implicit internal first-tier routers (see Border Router: Implicit Internal First-Tier Routers). Border routers dynamically determine borders, just as they dynamically determine zones.
A message can cross a border when a policy allows the message subject.
First-tier routing table information cannot cross a border.
Borders are not directly accessible to administrators; they remain internal to border routers.
A second-tier routing network is a collection of border routers in which every pair in the collection is connected by a route.
First-tier routing information includes information about first-tier routers, local networks, and all the subjects that can flow among them (within a zone).
Second-tier-routing information includes information about border routers, zones, and all the subjects that can flow among them; it specifically excludes all first-tier routing information.
All border routers in a second-tier network share second-tier routing information, but not first-tier information. Conversely, first-tier constituents of zones cannot access second-tier information—except for information about subjects available through a participating border router.
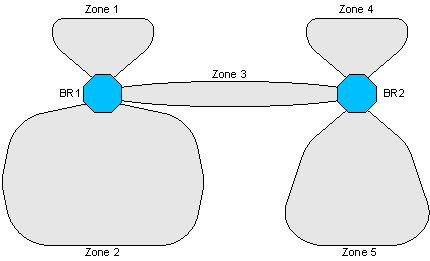
For example, Border Router: Second-Tier Routing Network illustrates the view of the second-tier network shared by BR1 and BR2 (based on the example of Border Router: Concepts). BR1 and BR2 share second-tier information so that both can create an internal routing table that includes both border routers, all five zones, and all the subjects that can flow among them. However, BR1 cannot access first-tier information about the constituents of zones 4 and 5, and BR2 cannot access first-tier information about the constituents of zones 1 and 2.