Certificates
This page lets you configure the X.509 certificates that a secure daemon uses to identify itself.
To display this page, click Certificates in the left margin of any page of the rvsd or rvsrd browser administration interface.
For background information, see Certificates and Security in .
Each daemon process keeps a list of certificates it can use to identify itself. These certificates are numbered for easy reference. The first panel on this page determines which of these certificates the daemon uses for particular tasks. The remainder of the page lets you enter the certificates.
Certificate Uses
Figure 135: rvsrd Certificate Uses Form
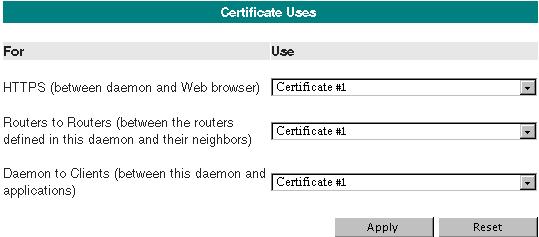
|
Item |
Description |
|
HTTPS |
Set the certificate for the secure browser administration interface. To avoid security warnings from the web browser, distribute the public portion of this certificate to authorized administrators. |
|
Routers to Routers |
Set the certificate for secure TLS neighbor connections. Distribute the public portion of this certificate to each applicable neighbor. (This item is included in routing daemons only; it is absent from |
|
Daemon to Clients |
Set the certificate for secure TLS client transport connections. Distribute the public portion of this certificate to each client program; see Secure Daemon in . |
Certificate List
Figure 136: rvsrd Certificate List

|
Item |
Description |
|
certificate number |
Use this number to refer to the certificate in the Certificate Uses panel. |
|
Add from File |
Enter a file name and a private key password. When you click Add from File, the daemon reads the certificate with private key from the file. The file may be in either PEM encoding, or PKCS #12 format. See also Security Factors. |
|
Add from Text |
Paste the text of a certificate with private key. Enter a private key password. The certificate must be in PEM encoding. See also Security Factors. |
When the daemon creates its store file (the first time it starts), it also creates a self-signed certificate, and registers it in the list as certificate #1. You may use that certificate as is, add other certificates to the list, or delete it and enter other certificates.
The self-signed certificate expires one year after creation.
You can also supply certificates signed by a certificate authority (CA). To use a CA-signed certificate, you must supply not only the certificate and private key, but also the CA’s public certificate (or a chain of such certificates). Concatenate these items in one file or string. For more details, see CA-Signed Certificates.
CA-signed certificates expire at dates recorded within the certificate data.