Developing Secure Applications
Security is everyone’s business, and everyone needs to collaborate and coordinate the requirements, tasks. This section can be used as a checklist for Application Developers, Database Administrator, and the office of CISO - Security Administrator.
Users may perform one or more roles (such as Application Developers, and Database Administrator).
Pre-requisites
The application developer, database administrator, security administrator have coordinated to exchange security-related information and artifacts. See Coordination. User can use this as a template checklist as a base form.
Checklists
- Coordinate security details with Security team with respect to the cipher suite, bit strength, algorithm to use, and other features.
- Secure the Database
- Securing the Server
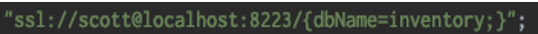
- Secure the Net Listener on Server to listen on Secured Sockets for sensitive and confidential transmission.
- Consider Multi-tenancy to isolate/partition data for different Entities, when data security is needed, and resources have to be utilized efficiently.
- Consider Containerization when utmost security is needed i.e. Data partitioning and resource isolation.
- Client Applications
Once Database security is defined, it cannot be changed for the lifetime of the database. If you need to change it, export the database, then re-initialize the database with new keys, and reimport the data from the exported files.
The appendix A, and B provides template checklist form for user’s convenience.