Configuring Secure Socket Layer (SSL) Encryption for the TCP/HTTP Listener
You can enable SSL for the TCP/HTTP Listener to encrypt all traffic between the server and any client application, such as the WebFOCUS Client, a remote server, or a cluster server.
To enable SSL, do the following:
- On the Workspace page, open the Special
Services and Listeners folder, right-click TCP/HTTP,
and select Properties of HTTP.
The Listener Configuration page opens.
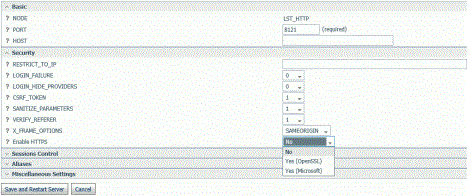
- In the Security section,
select Yes (OpenSSL) or Yes (Microsoft) from
the Enable HTTPS drop-down list.
Additional fields needed for SSL configuration appear.
Note:- Open SSL libraries v1.1.1 and v1.0.2 are supported.
The current run-time version depends on the following configuration keyword in the edaserve.cfg file.
ssl_lib_vendor = {sslv11|sslv10}The default value for ssl_lib_vendor is sslv11.
You should also set the environment variable IBI_LOAD_SSL_FROM or IBI_LIBPATH to point to the appropriate openSSL library.
For example:
ssl_lib_vendor = sslv11 IBI_LIBPATH=/usr/local/ssl64/1.1.1/lib
or:
ssl_lib_vendor = sslv10 IBI_LIBPATH=/usr/local/ssl64/1.0.2/lib
- OpenSSL libraries libeay32.dll and ssleay32.dll must be in the path to enable SSL.
- Open SSL libraries v1.1.1 and v1.0.2 are supported.
- Enter the
following values:SSL_CERTIFICATE
Contains the certificate chain in order, starting with the certificate for the listener and ending with the root CA certificate. Each of these entries must be in PEM format.
Note that the administrator at the installation site must acquire valid security certificates (self-signed or commercial).
SSL_PRIVATE_KEYDefines the file that contains the private key of the listener. It must correspond to the public key embedded within the certificate and must be in PEM format.
SSL_PASSPHRASE_EIf the file defined in SSL_PRIVATE_KEY is encrypted, a passphrase must be provided here to decrypt the private key.
SSL_CA_CERTIFICATEDefines the name of a file containing a trusted CA certificate in PEM format. It is used to verify the client certificate. If the client fails to send a certificate or verification fails, connections are rejected. More than one CA certificate may be present in the file.
SSL_LABELSpecifies a descriptive comment used to identify the key and certificate in the certificate database. (IBM GSK Only).
For z/OS only, is a certificate LABEL in the RACF database. Must be connected to the RACF Keyring pointed by the parameter SSL_CERTIFICATE. Server system ID (default ISERVER) must be the certificate owner in the case when a personal certificate is used. When a SITE certificate is used as a server certificate, it has to be connected to a Keyring with the parameter USAGE(PERSONAL). Otherwise, the private key is unaccessible.
SSL_FRIENDLY_NAMESpecifies a name used to identify the certificate in the PKCS#12 file, if the file contains more than one certificate.
SSL_AUTH_CLIENTDefines whether client authentication should be enabled. Select one of the following values from the drop-down list.
- 0. The client is not asked for a certificate. There is no client authentication.
- 1. The server requests the client to send a certificate. All received certificates are validated. If the client fails to send a certificate or verification fails, connections will be rejected.
- Click Save and Restart Server.