Working With the Authentication Page
|
In this section: |
|
How to: |
The Authentication page defines the methods of authentication available within a security zone. The default settings for each zone identify the most commonly used authentication methods for users in that zone, but Administrators can replace or supplement them with any of the other methods on the Authentication page.
Each available authentication method requires a unique configuration and works in different ways to authenticate users. Authentication methods that are available to users within a specific zone are identified with a check mark and a status of Enabled. Methods that are not available are marked with a status of Disabled.
The Actions section of the Authentication page contains links to the dialog boxes and activities that affect all Authentication methods in a particular zone. The Security Zones section contains links that save, the Authentication page settings, export them to or re-import them from the securitysettings.xml file.
The Options link opens the Authentication Options dialog box where administrators can identify a customized URL to which WebFOCUS can direct users after their logout.
The Key Management link opens the Key Management dialog box where administrators can configure the location of the Keystore file that identifies the secure keys that support certificate-based methods of authentication, such as SAML and Trusted Ticket.
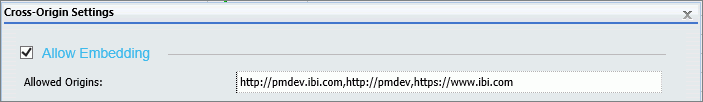
The Cross-Origin Settings link opens the Cross-Origin Settings dialog box, where administrators can configure WebFOCUS to allow the use of its resources in external applications that take advantage of WebFOCUS business intelligence by embedding WebFOCUS content and resources into their webpages. Within this dialog box, the Allow Embedding check box supports the embedding of WebFOCUS resources in the webpages of comma-delimited whitelisted URLs. The Allow Cross-Origin Resources Sharing (CORS) check box supports the use of Ajax request and response messages that enable users of comma-delimited whitelisted URLs to interact with embedded WebFOCUS resources. Each zone maintains its own configuration of cross-origin settings.
The Enable/Disable link enables previously disabled authentication methods, and disables previously enabled methods. This link becomes available only after an authentication method is selected.
The Edit link opens the dialog box that supports a selected Authentication Method. In that dialog box, you can create or update the configuration settings required by that method. This link becomes available only after an authentication method is selected.
Procedure: How to Enable an Authentication Method
- On the Authentication Page, right-click
the Name or Status section
of an Authentication Method entry marked Disabled, and then click Enable.
or
- Click anywhere in an Authentication Method entry marked
Disabled, and then, in the Actions section, click Enable.
The status changes from Disabled to Enabled with a check mark, and the method of authentication represented by that entry is available for use within the Security Zone.
Procedure: How to Disable an Authentication Method
- On the Authentication Page, right-click
the Name or Status section
of an Authentication Method entry marked Enabled, and then click Disable.
or
- Click anywhere in an Authentication Method entry marked
Enabled, and then, in the Actions section, click Disable.
The status changes from Enabled to Disabled, the check mark clears, and the method of Authentication represented by that entry is no longer available for use within the Security Zone.
Procedure: How to Save Changes to the Authentication Page
- On the Authentication Page, in the Actions section, under Security Zones, click Save.
- When you receive a confirmation message, click OK.
- When you receive a message to reload the web application, click OK.
- Close the Administration Console, and sign out of WebFOCUS.
- Sign in to WebFOCUS as an administrator, and open the Administration Console.
- Click the Security Tab, and under
the Security Zone Folder, click the Authentication Page for the
zone that you recently configured.
Your new or updated settings appear as configured.
Procedure: How to Configure a Custom Logout Address
Security Zones are configured to use form-based authentication, by default. When users in a form-based authentication security zone sign out, the sign-out page that opens links users to the sign-in page. However, in zones that use an external authentication method or a pre-authentication method, there is no need to link users to the sign-in page after they sign out. For these zones, the Custom Logout Address substitutes the URL of an alternative sign-out page that overrides the display of the default sign-out page.
- On the Authentication page, in the Actions section, click Options.
- In the Authentication Options dialog box, select the Enable custom logout target URL check box.
- Type the custom logout target URL.
- If the Security Zone is configured for Integrated Windows Authentication (IWA), accept the default sign-out URL, /signout.
- If the Security Zone is configured for another third party pre-authentication provider,
type the sign-out URL that ends the SSO product session for that
provider, if one exists. For example, the sign-out URL for WebSEAL
may be:
http://webseal.domain.com/pkmslogout
The sign-out URL for Siteminder may be:
http://siteminder.domain.com/logout.html
To return a user working in a single sign on environment to his or her original portal automatically, leave the final term blank. For example, the sign-out URL for WebSEAL would then be:
http://webseal.domain.com
- Click OK.
Configuring Cross-Origin Settings
External applications can take advantage of WebFOCUS business intelligence by embedding WebFOCUS content and resources into their webpages. For example, an external application designed to provide customer service can embed portals designed and built within WebFOCUS that add reporting, charting, and analytic resources to the customer service metrics or account service history information they display.
However, to protect WebFOCUS from requests to embed its resources or content from unknown and unauthorized external applications, WebFOCUS does not allow embedding, by default. By selecting the Allow Embedding check box in the Cross-Origin Settings dialog box, an administrator can override this default configuration, and allow WebFOCUS to accept requests to embed portals, pages, or other resources into a frame or iframe within the webpage of a trusted external application.
External applications can also take advantage of WebFOCUS business intelligence by making embedded WebFOCUS content and resources interactive. Asynchronous Ajax requests issued from the browsers of users of the embedded application retrieve or update WebFOCUS resources and content dynamically, keeping information current and allowing for user interaction with embedded content.
Cross-origin resource sharing (CORS) allows a web page to request restricted resources from another domain outside of the domain from which the first resource was served. Using a cross-origin resource sharing policy configuration, a web page may be permitted to embed cross-origin images, stylesheets, scripts, iframes, and videos from separate domains, but forbid more sensitive cross-domain requests, such as Ajax requests. Because it allows a resource to limit cross-origin requests to a specific set of domains and messages, the CORS standard defines a way in which a browser and server can interact to determine whether or not it is safe to allow a cross-origin request. It allows for more freedom and functionality than purely same-origin requests, but is more secure than simply allowing all cross-origin requests. It is a recommended standard of the W3C consortium. For more information see, https://en.wikipedia.org/wiki/cross-origin_resource_sharing and the Cross-Origin Resource Sharing Recommendation from the W3C consortium http://www.w3.org/TR/cors/.
The Cross-Origin Settings dialog box activates the use of Embedding and Cross-Origin Resource sharing within WebFOCUS, as shown in the following image. The Allow Embedding check box supports the basic request to embed content within a frame or iframe of an external webpage. The Allow Cross-Origin Resources Sharing (CORS) check box supports the use of Ajax cross-origin sharing requests.

Note: Even though the Allow Embedding and Allow Cross-Origin Resources Sharing (CORS) check boxes appear together in the Cross-Origin Settings dialog box and work together to support the full requirements of Embedded BI Applications, these two settings are not dependent on each other. For example, an installation of WebFOCUS can be configured to support an external application that uses cross-origin resource sharing but does not require the use of embedded WebFOCUS content in a frame or iframe. Another installation of WebFOCUS could be configured to support an simple application that embeds a portal in a frame or iframe, but does not support cross-origin Ajax requests.