Procedure: How to View the Effective Policy for a User on a Resource
The Effective Policy dialog box indicates why a user does or does not have a certain capability. To view the effective policy of other users, you must be permitted the following privileges:
- View Rules on a Resource (opViewRulesOn), which enables the Rules on this Resource and Effective Policy options on the Security shortcut menu.
- Manage Rules on Resources (opManageRulesOn), which enables the Rules option on the Security shortcut menu.
Users with only the View Rules on a Resource privilege may view the effective policy only for themselves, on particular resources. If a user does not have the appropriate privileges, the options to view or manage rules and effective policy will not appear in the shortcut menus.
- Right-click
a resource and click Security, then Effective
Policy.
The Effective Policy dialog box appears, listing the effective policy calculated for each privilege appearing in a rule on this resource.
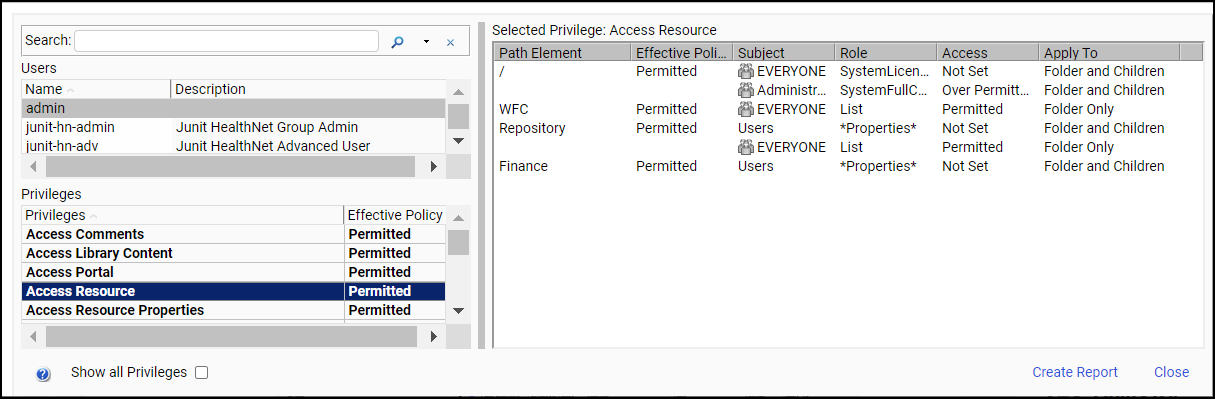
If you have the appropriate privileges, you can select other users from the User drop-down list to see their effective policies.
- To show the effective policy for all privileges for this user on this resource, including those not applied to the resource in any rules, select Show all Privileges.
- To see how
the effective policy for a privilege is evaluated, select the privilege
in the Privileges box.
The Effective Policy dialog box displays the policy evaluation for all the groups to which the user belongs at every level of the hierarchy above the resource, displaying the following information for each level:
- Path Element.
- Effective Policy. The access set on this folder by the combination of all applicable rules.
- Subject.
- Role.
- Access. The access set on this folder by rules applying directly to this level of the hierarchy.
- Apply To. Whether the policy applies to the folder for the path element only, the folder and its children, or only the children of the folder for the path element.
- To produce a rich text version of the information produced in the dialog box, select a privilege and click Create Report.