As of Release 8.2 Version 01, the WebFOCUS Server installation automatically creates an administration configuration file, identified as admin.cfg.
The following sample of the text in the admin.cfg file, located in drive:\ibi\profiles, includes the default configuration, with an operating system userid, and the default
PTH<internal> security provider.
Sample default admin.cfg
admin_id = OPSYS\DOMAIN\operatingsystemuserid
BEGIN
admin_level = SRV
END
admin_id = PTH\srvadmin
BEGIN
admin_password = {AES}encrytpedpassword
admin_level = SRV
END
admin_level = APP
BEGIN
admin_privilege = NODPT,NOSYS,METAP,DATMG,PRSAV,PRDFR,PRRPT,
PROUT,MONIT,CHGPW,MONUS,MONGR,KILT3,KILGR,
APATH,DBMSC,UPROF,APROF
admin_privilege = *;ANONE
admin_privilege = (APPROOT);AREAD,ARWRT,PRRUN,ALIST
END
admin_level = USR
BEGIN
admin_privilege = NODPT,NOSYS,PROUT,CHGPW,MONUS,KILT3,APATH,
DBMSC,UPROF
admin_privilege = *;ANONE
admin_privilege = (APPROOT);AREAD,ARWRT,PRRUN,ALIST
END
admin_level = OPR
BEGIN
admin_privilege = NODPT,NOSYS,MONIT,KILAL,STPSV,CHGPW,MONUS,
MONGR,KILT3,KILGR
admin_privilege = *;ANONE
admin_privilege = (APPROOT);AREAD,ARWRT,ALIST
END
>>>Replace this line with all lines from the WebFOCUS
Access Control Template Text.<<<
[Access Control]
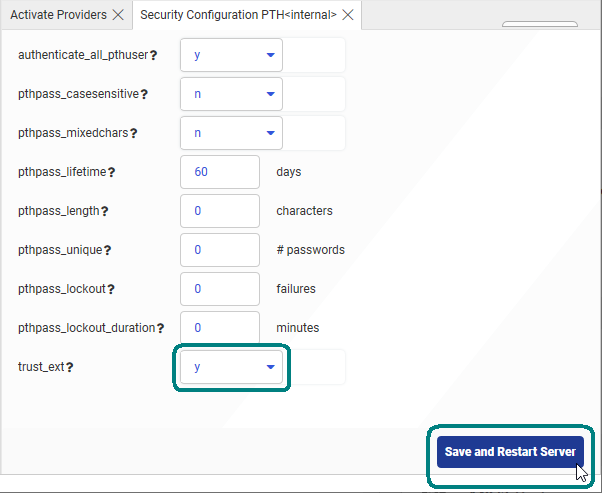
authenticate_all_pthuser = y
prepend_provider_name = n
where:
- operatingsystemuserid
-
Is the actual operating system user ID.
- encrytpedpassword
-
Is the userid password that is encrypted by the WebFOCUS Server using the key specified in the cfgfile_cipher.
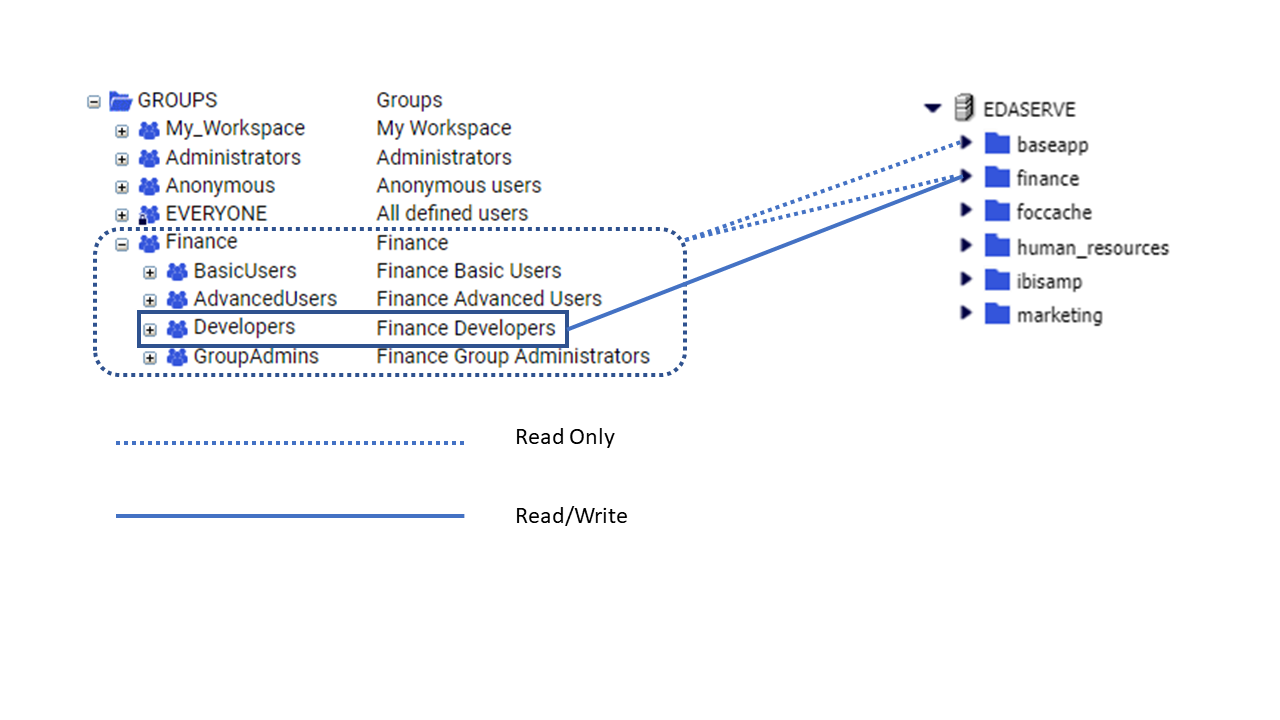
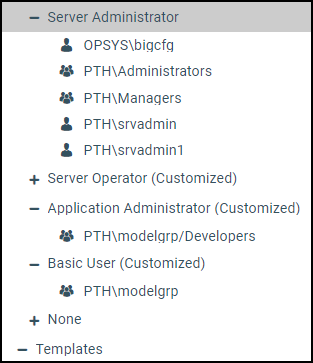
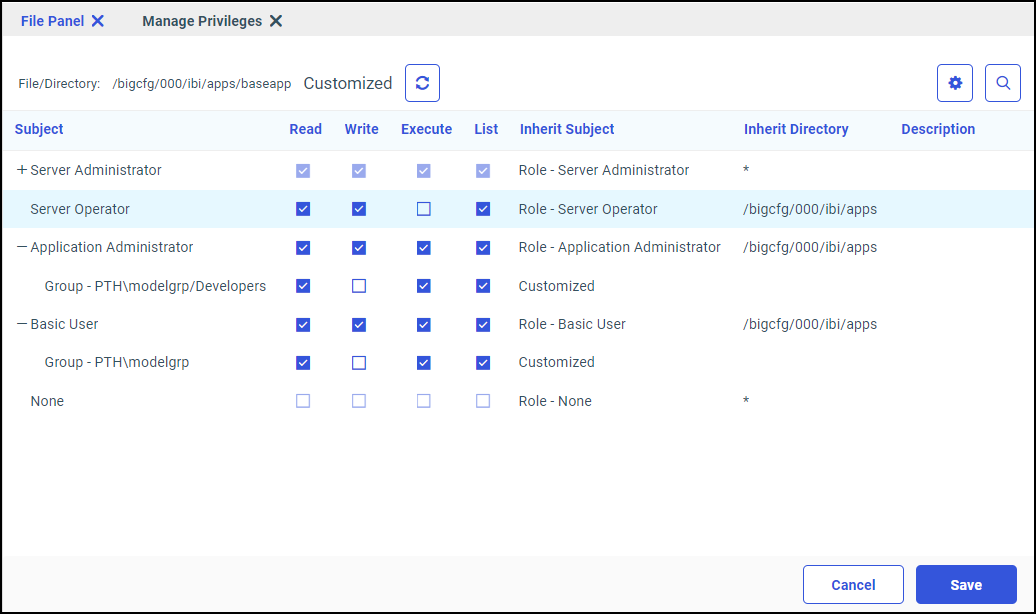
By default, the template assigns the USR role to all users assigned to the BasicUsers, AdvancedUsers, and GroupAdmins groups
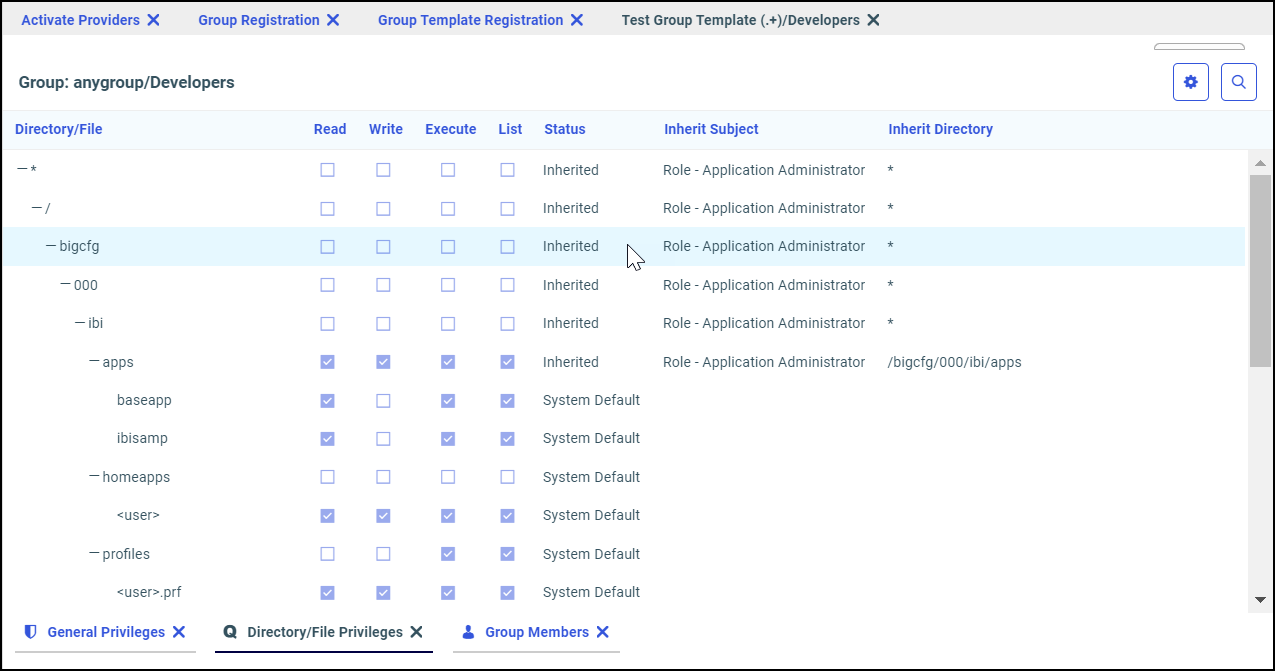
of individual workspaces. These groups are usually referred to as Workspace\BasicUsers, Workspace\AdvancedUsers, and Workspace\GroupAdmins, where Workspace is the name of the individual workspace to which they are assigned. For example, Finance\BasicUsers. When users from those groups connect to the WebFOCUS Server, they have Read, Execute, and List privileges to resources within their workspace application folder.
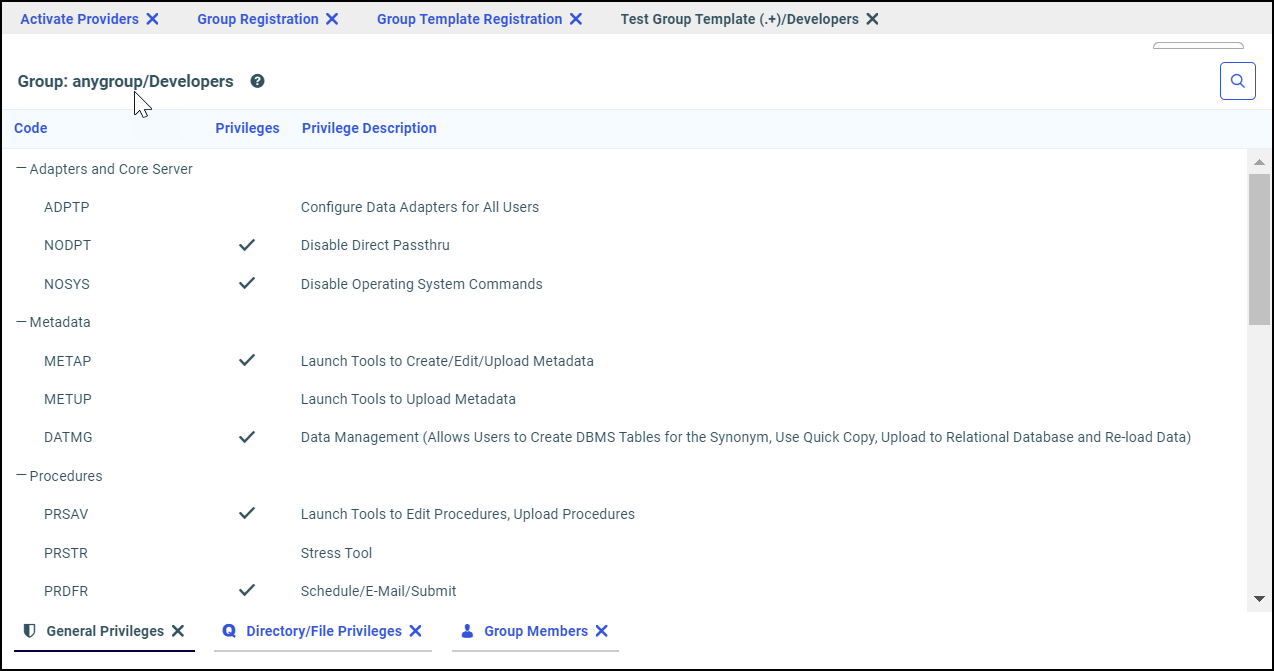
The template also assigns the APP role to the Workspace\Developers group. When users from this group connect to the WebFOCUS Server, they have Read, Write, List, and Run privileges for resources within their workspace application folder, as well as additional privileges that support their role as developers.
To replace this generalized configuration of access control settings with an access control template, copy the text from
the following section, Access Control Template Text, and
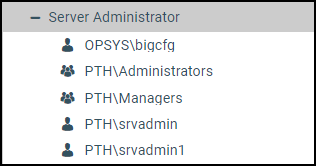
paste it into an existing admin.cfg file. This addition creates an access control template that grants proper authorization
to the Administrators group, Managers
group, and any workspace group that connects to the WebFOCUS
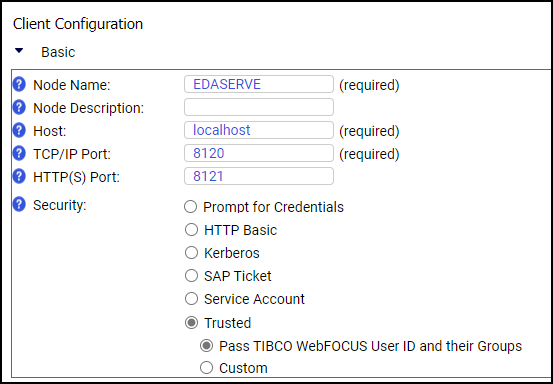
Server through the trusted connection defined in How to Establish a Trusted Connection to the WebFOCUS Server From the WebFOCUS Client.
Access Control Template Text
The access control template that appears in this section applies to all trusted users and groups that connect to the WebFOCUS Server to which this template is assigned. It uses Group ID patterns and regular expressions to establish a configuration that serves
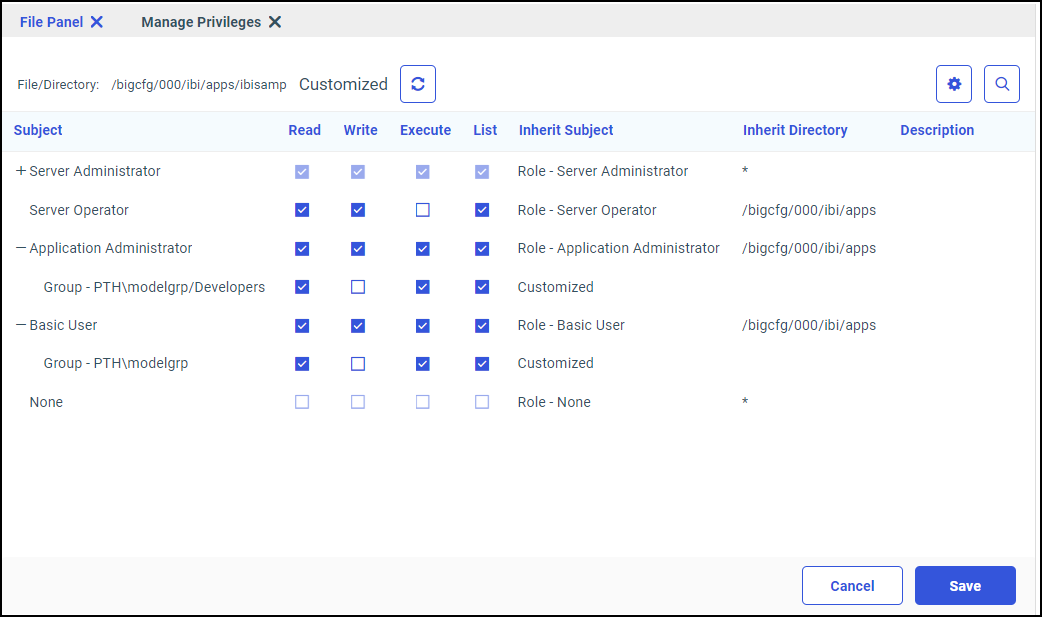
most installations effectively. This template is based on an access model that grants all users Read, List, and Run privileges
in the ibisamp and baseapp directories.
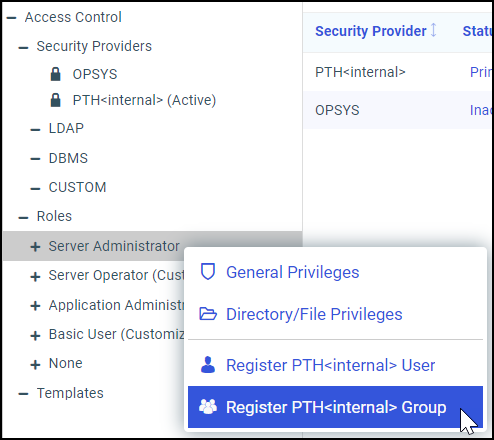
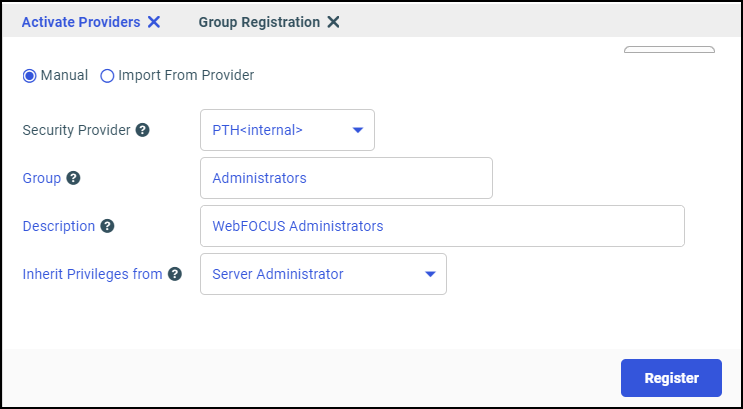
admin_group = Administrators
BEGIN
admin_level = SRV
admin_description = WebFOCUS Administrators
END
admin_group = Managers
BEGIN
admin_level = SRV
admin_description = WebFOCUS Managers
END
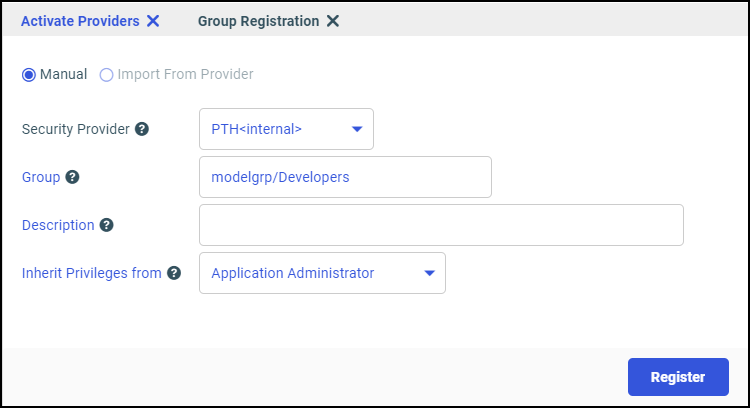
admin_group = modelgrp/Developers
BEGIN
admin_level = APP
admin_privilege = *;ANONE
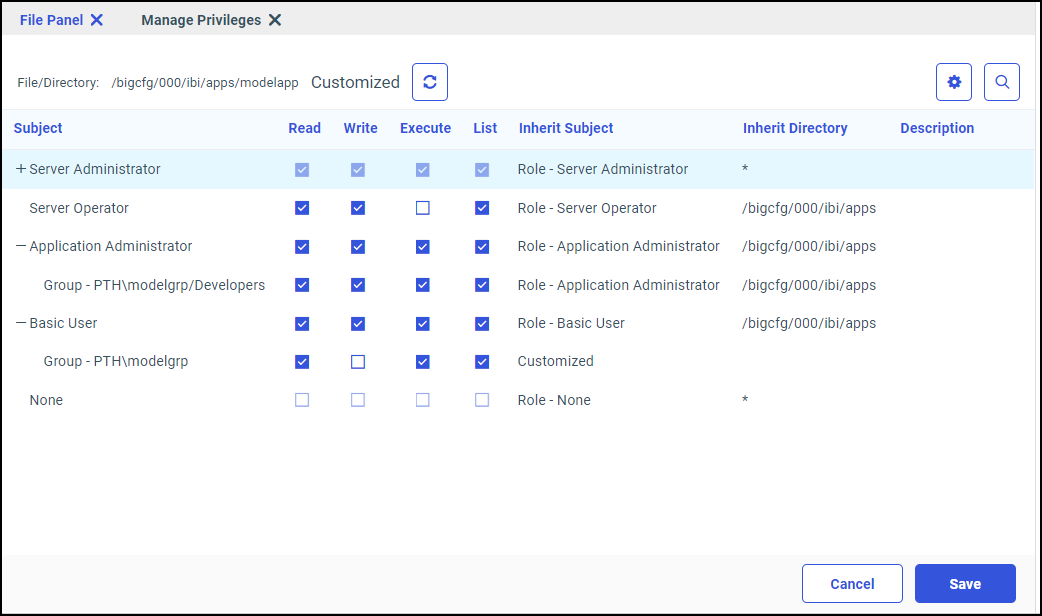
admin_privilege = (APPROOT)/baseapp;AREAD,PRRUN,ALIST
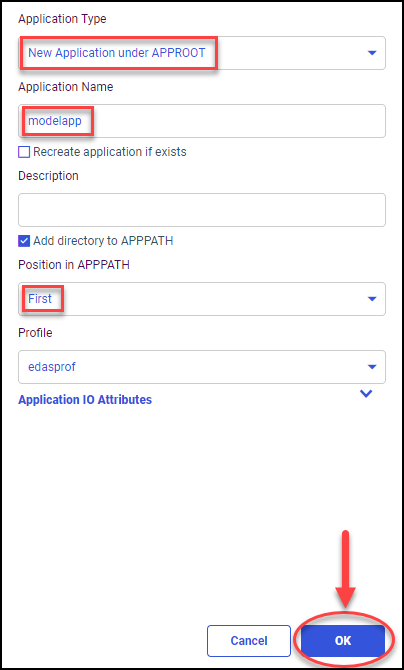
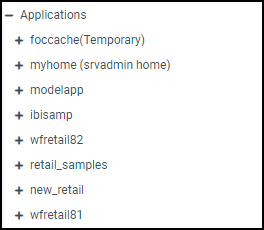
admin_privilege = (APPROOT)/modelapp;AREAD,ARWRT,PRRUN,ALIST
admin_privilege = (APPROOT);ANONE
admin_privilege = ADPTP,NODPT,NOSYS,METAP,DATMG,PRSAV,PRDFR,
PRRPT,PROUT,MONIT,SRVLG,KILT3,APATH
admin_privilege = (APPROOT)/ibisamp;AREAD,PRRUN,ALIST
END
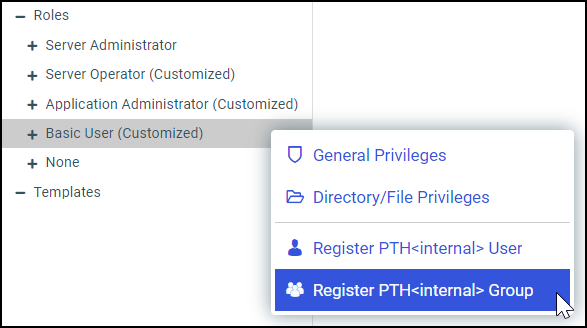
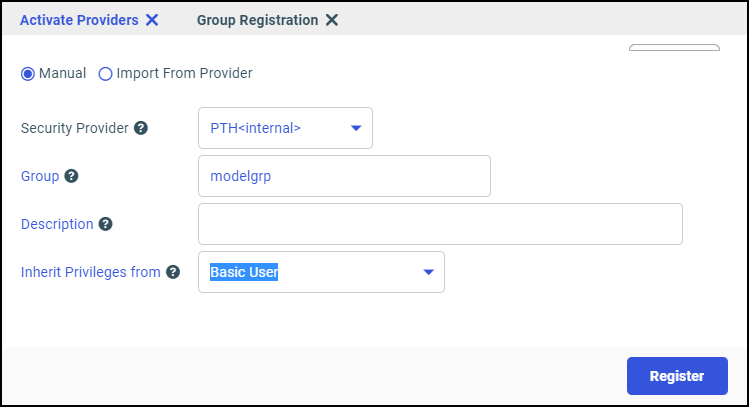
admin_group = modelgrp
BEGIN
admin_level = USR
admin_privilege = NODPT,NOSYS,PRDFR,PRRPT,PROUT,KILT3,APATH
admin_privilege = *;ANONE
admin_privilege = (APPROOT)/baseapp;AREAD,PRRUN,ALIST
admin_privilege = (APPROOT)/modelapp;AREAD,PRRUN,ALIST
admin_privilege = (APPROOT);ANONE
admin_privilege = (APPROOT)/ibisamp;AREAD,PRRUN,ALIST
END
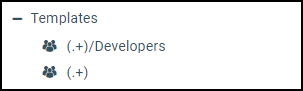
admin_group_template = (.+)/Developers
BEGIN
model_group = modelgrp/Developers
file_replace_pattern = (modelapp)
END
admin_group_template = (.+)
BEGIN
model_group = modelgrp
file_replace_pattern = (modelapp)
exclude_groups = (/)
END
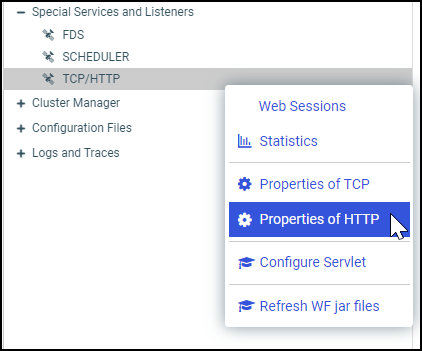
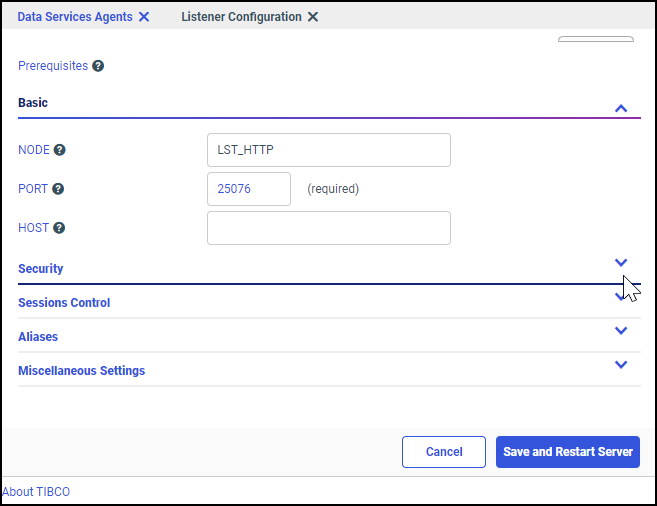
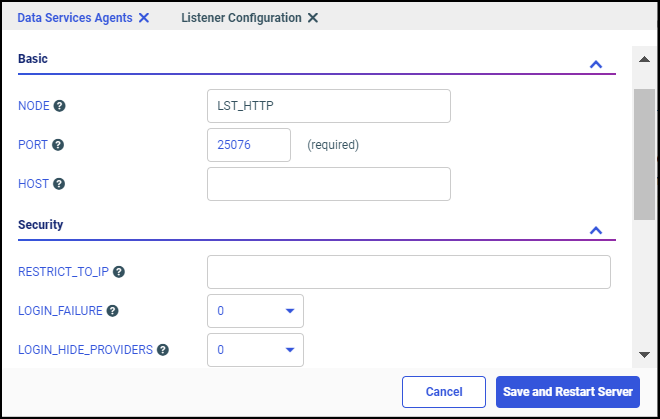
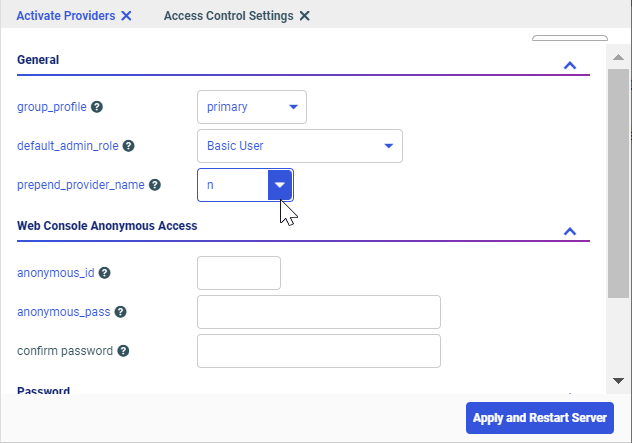
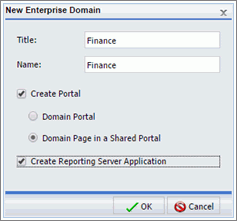
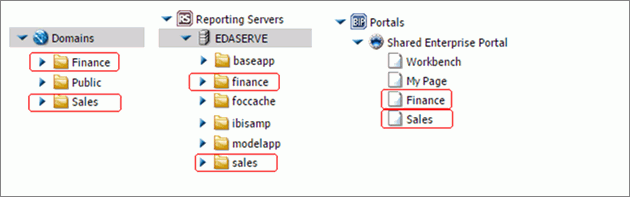
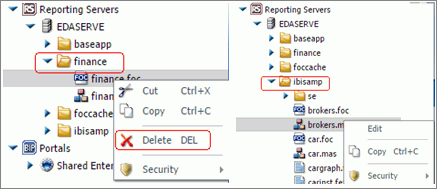
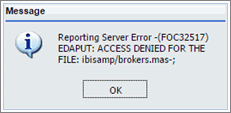
 to close the Open dialog box without creating a report.
to close the Open dialog box without creating a report.