Authentication Policies
This section describes the configuration to apply authentication policies.
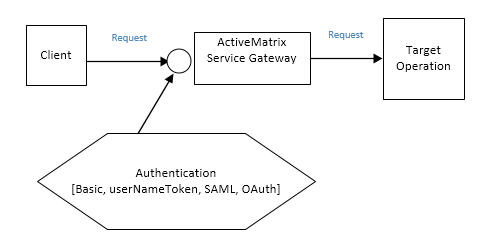
Figure Authentication Policies illustrates how to apply the authentication policies for an incoming request.
- Configuring Authentication Policies
- Authentication Policies Types
- Authentication Using Custom Shared Resource
You may use a custom shared resource in an authentication policy to authenticate a request.
Copyright © Cloud Software Group, Inc. All rights reserved.