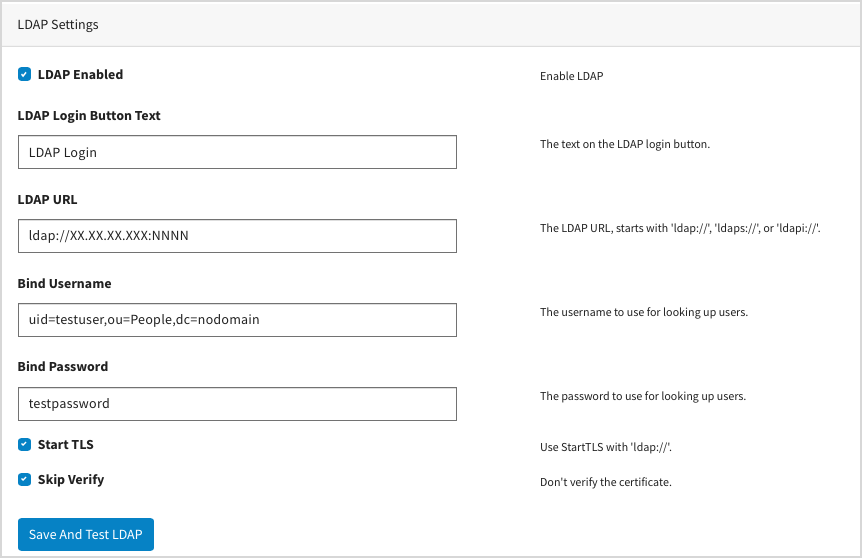
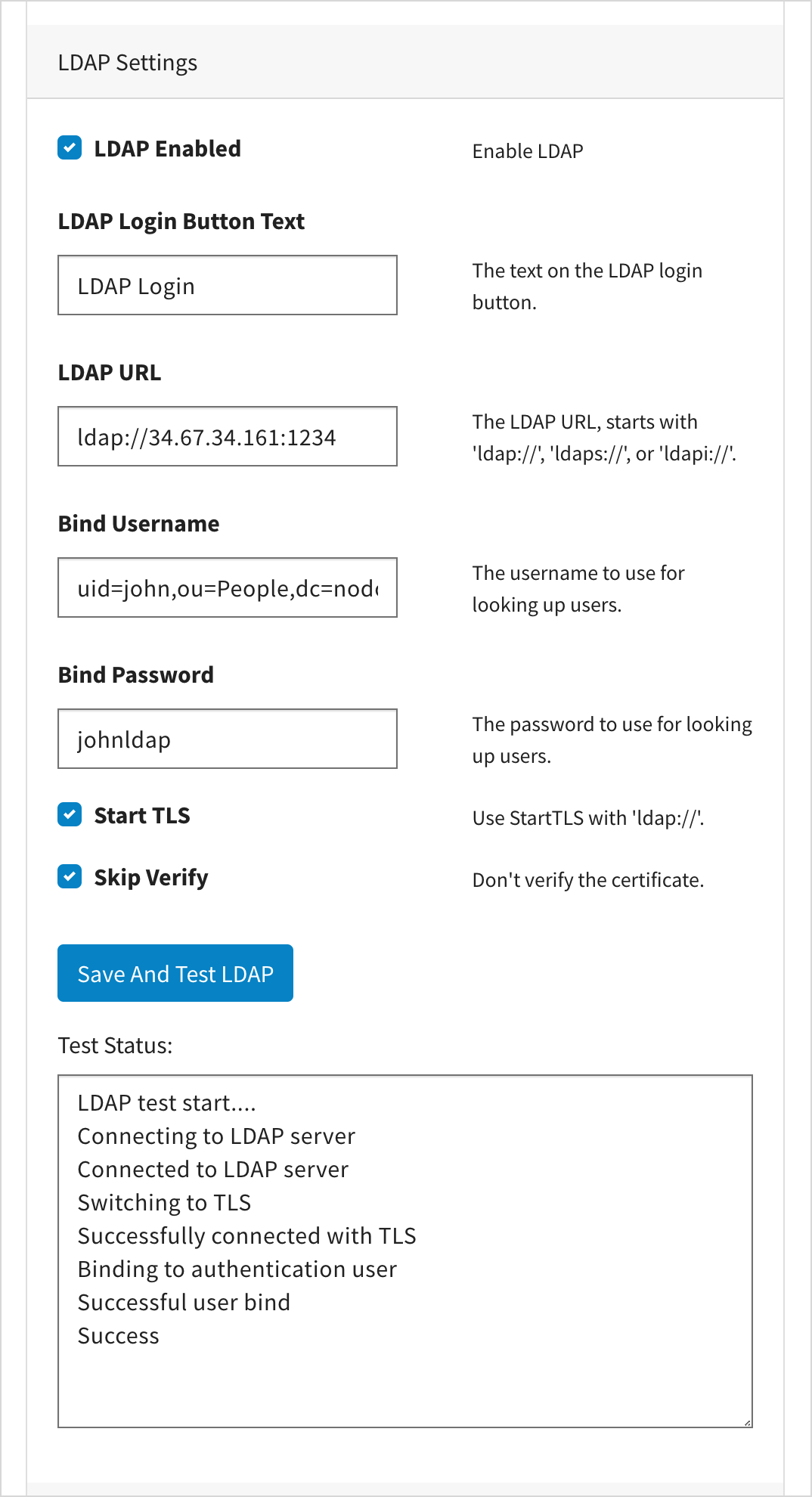
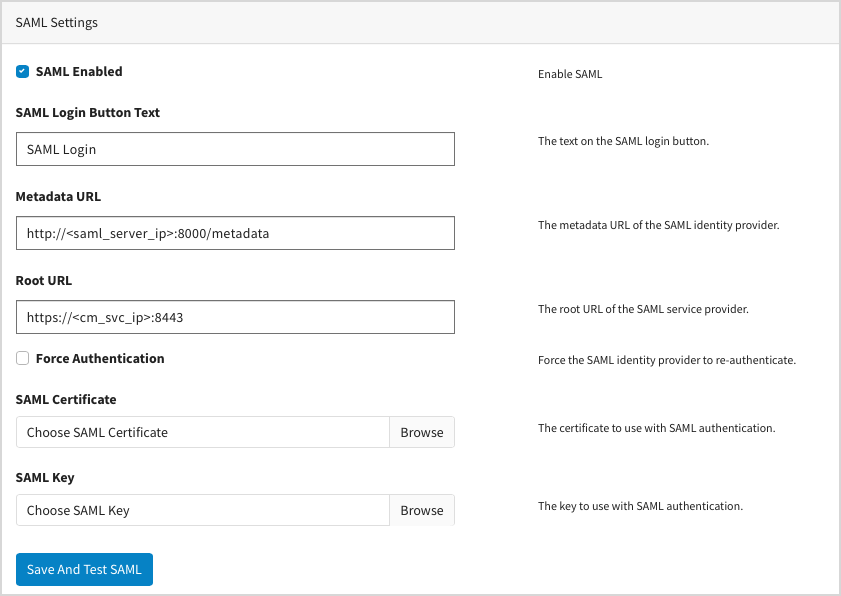
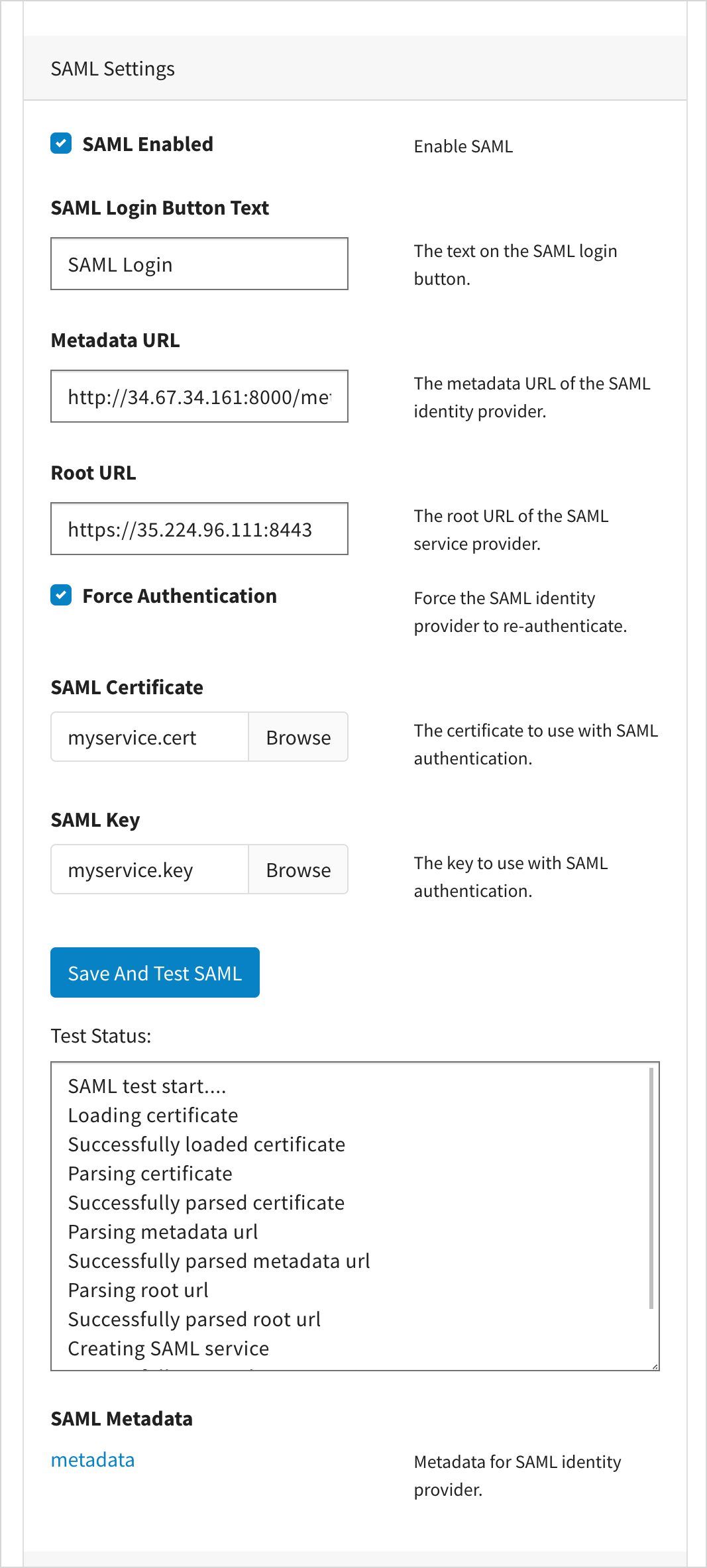
Configuring LDAP and SAML with Local Edition
Configuring SAML with Local Edition
Procedure
What to do next
Load the metadata file to SAML server.
curl -v -T metadata.xml http://<saml_server_ip>:8000/services/test
curl -v -T /Users/<user_name>/Downloads/metadata.xml http://xx.xx.xx.xxx:8000/services/test * Trying xx.xx.xx.xxx... * TCP_NODELAY set * Connected to xx.xx.xx.xxx (xx.xx.xx.xxx) port 8000 (#0) > PUT /services/test HTTP/1.1 > Host: xx.xx.xx.xxx:8000 > User-Agent: curl/7.54.0 > Accept: */* > Content-Length: 3795 > Expect: 100-continue > < HTTP/1.1 100 Continue * We are completely uploaded and fine < HTTP/1.1 204 No Content < Date: Thu, 10 Dec 2020 23:49:21 GMT < * Connection #0 to host xx.xx.xx.xxx left intact
Copyright © 2022. Cloud Software Group, Inc. All Rights Reserved.