Add Authenticator
Click to add LDAP authenticators on the Add Authenticator page.
To synchronize the MFT database through LDAP, you must configure an LDAP authenticator. On the Add Authenticator page, you will see the Authenticator Properties section with the following subsections:
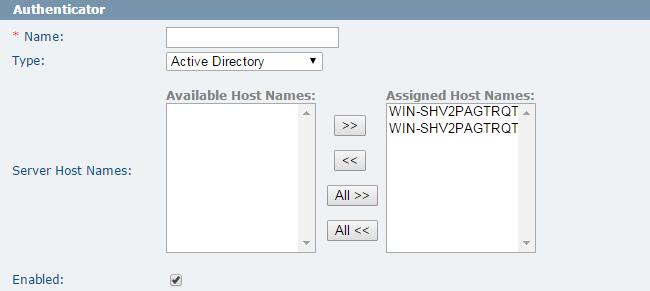
Authenticator
| Field | Description |
|---|---|
| Name | The unique name of the LDAP authenticator in MFT and is used as the prefix to the user ID followed by a dash when it is pulled in from the LDAP server. For example, LDAPServer-john.doe. |
| Type | The type of directory where LDAP is pulling the user and role credentials from, such as Active Directory, eDirectory, Sun Directory Server, Tivoli, and others. |
| Server Host Name | The hosts that will use this authenticator. If no specific host name is assigned, all the hosts will be set to use this authenticator. |
| Enabled | This parameter defines whether to enable this LDAP authenticator. If selecting this check box, all users connected to this LDAP server will no longer be able to connect to the MFT server. Disabled users will lose TransferRight and show LDAP status as “Inactive” on the Update User page in TIBCO MFT Command Center or TIBCO MFT Internet Server. |
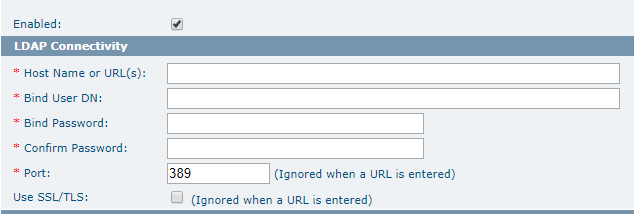
LDAP Connectivity
This section defines the parameters are required to connect to the directory server and pull in the user and role information for synchronizing.
The following table lists the fields in the LDAP Connectivity section:
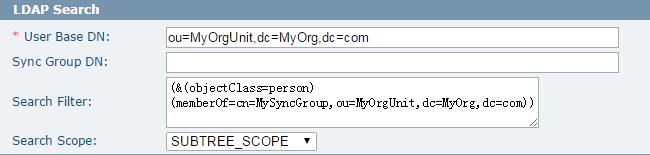
LDAP Search
The LDAP Search section defines the location of the sync group and the users which will be synced into the MFT database.
The following table lists the fields in the LDAP Search section:
| Field | Description |
|---|---|
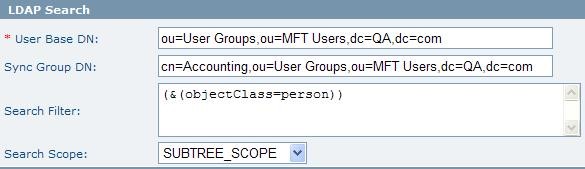
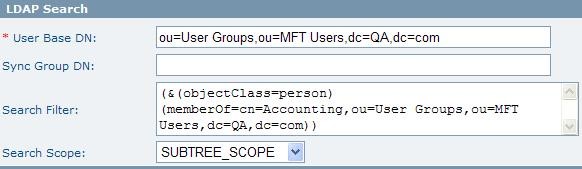
| User Base DN | The base in the directory tree where users are defined. The levels searched below this base depend on the Search Scope parameter |
| Sync Group DN | The fully qualified name of the container on the directory server which will be used to associate the users with MFT. Only users who are inside this container will be synchronized with the Database. |
| Search Filter | The LDAP Search Filter allows you to be more selective of the user objects returned during an LDAP search; it can be used instead of, or in addition to the Sync Group DN. Syncing unnecessary LDAP objects with the MFT server can be avoided when using an appropriate search filter.
For example to sync all users from Active Directory with mail accounts the filter string would be: (&(objectclass=user)(mail=*)) If you do not wish to use a specified filter to search for users you should change the value to read (objectClass=user) Contact your directory server administrator for more details on constructing LDAP Search Filters. |
| Search Scope | The directory levels below the Base DN that LDAP will search. SUBTREE_SCOPE - defines that all levels below the Base DN will be searched.
This is the default value and should be used by most users. ONELEVEL_SCOPE - defines that only the level defined by the Base DN will be searched. OBJECT_SCOPE - defines that only the object defined by the Base DN and the Search Filter will be searched. |
The following examples show different configurations that an administrator can set up to search for LDAP users:
Example 1: The following example will result in 10 Active Directory users being added to the MFT database:
Example 2: The following example will result in 2 Active Directory users being added to the MFT database:
Example 3: If you would prefer to use search filters we can accomplish the same results as in the above example using this setup:
Below are some examples of search filters that could be used when searching for users becomes more detailed:
Filter to sync multiple Security Groups in a single authenticator:
(|(&(objectClass=user)(memberOf=cn=Accounting,ou=User Groups,ou=MFT Users,dc=QA,dc=com))(&(objectClass=user)(memberOf=cn=Finance,ou=User Groups,ou=MFT Users,dc=QA,dc=com)))
Filter to sync all users with mail accounts:
(&(objectclass=user)(mail=*))
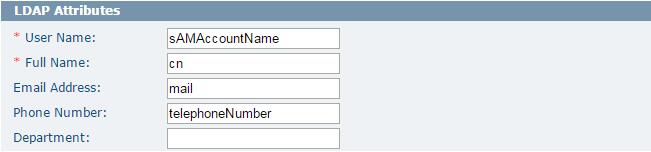
LDAP Attributes
This section defines the parameters that LDAP reads from the directory datastore server to pull in the correct information. The predefined values in this section should be confirmed with the directory server administrator. In most cases, no changes are necessary.
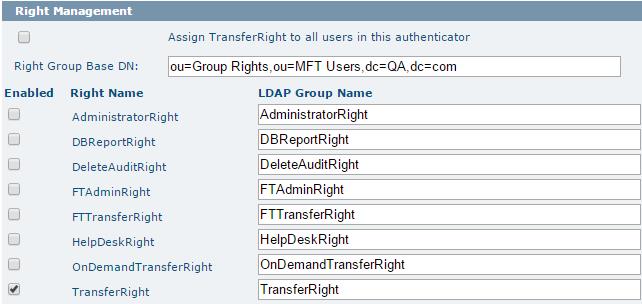
Right Management
This section defines the rights you want to be managed using the LDAP server.
TIBCO MFT Command Center or TIBCO MFT Internet Server users can be assigned various rights which allow them different capabilities. The most popular of these rights is the Transfer right right; without this right assigned to a user, they cannot perform file transfers. After selecting the Assign TransferRight to all users in this authenticator check box, all users in this authenticator will be assigned with TransferRight when they are synced. When this check box is selected, you should not enable Right Synchronization for TransferRight. Some LDAP environments can want to control which users are assigned this right and other rights from the LDAP server. When the right is enabled for management through the LDAP server, it cannot be granted or un-granted from TIBCO MFT Command Center or TIBCO MFT Internet Server. A group with the name which is specified in the LDAP Group Name field must exist on the directory server and the users granted this right must be members of the group.
The following table lists the fields in the Right Management section:
| Field | Description |
|---|---|
| Right Group Base DN | The location in the directory tree of the OU which contains the MFT rights. |
| Enable | This parameter defines whether to enable the right be managed on the defined LDAP server. |
| Right Name | The right as it is recognized by MFT. |
| LDAP Group Name | The name of the group in the LDAP server that will be associated with the right in MFT. This name can be the same as the right name or be specified as a different group name. The LDAP group name specified in the field should match the group name on the directory server. |
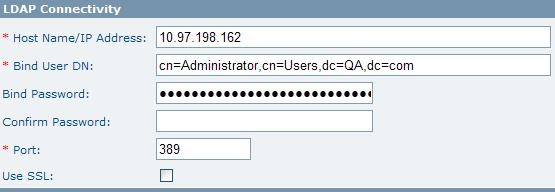
The following example will result in 2 Active Directory users being added to the MFT database: