User Access Control
This topic explains how to configure users, user roles, and user access to the Artifact Management Server.
User Authentication and Authorization
AMS users are assigned to roles based on the operations they are permitted to perform. For example, a business user might be tasked with modifying an artifact, a manager assigned the reviewer role to approve the change, and an IT department member assigned to the administrator role to maintain AMS.
Due to this partitioning of responsibility, each user must authenticate to the AMS web client so AMS can determine the set of operations available to the user. The web client login method passes a user name and password to the AMS and, assuming the credentials are valid, returns a token that identifies the user in subsequent requests, which must include the token. AMS uses a security framework to authenticate and authorize users.
Users are assigned one or more roles, and roles are granted one or more permissions. Each permission specifies an object type, an action that can be performed on that object, and, optionally, a specific instance of the object. For example, the artifact:checkout permission would allow a user with that permission to check out any artifact, while the artifact:checkout:foo permission would allow a user to check out only the foo artifact. The security framework supports multiple security realms (repositories of security information).
Additional permission scenarios:
Grant read access to all artifacts in project P1:
privilege = "artifact:read" resource = "P1/*"
Grant write access to all artifacts whose names start with A in projects whose names start with P:
privilege = "artifact:write" resource = "P*/A*"
Grant deploy access to all artifacts whose names end with A in all projects:
privilege = "artifact:deploy" resource = "*/*A"
User Access Control Workflow
The following applies when configuring AMS to use local or LDAP authentication realms.
-
Defining users
-
Defining roles
-
Defining permissions per role
-
Assigning users to roles
Apple Text Editor Advisory when Editing Configuration Files
Ensure that all configuration file values requiring quotes use straight quotes ("...") and not smart quotes (“...”). Smart quotes are treated as data and not as a means to identify AMS user names or passwords.
AMS configuration files use straight quotes to encapsulate values. Apple's TextEdit application is a rich text editor that uses smart quotes by default. If using TextEdit or any rich text editor, ensure the editor is set to use straight quotes.
User Roles
As AMS administrator, you define the users who are permitted to log into the AMS web client, as well was what role or roles they play with the projects and artifacts contained therein. Role permissions are configurable.
The following example is a role-to-privilege mappings configuration file with four roles defined:
-
Administrator, which has privileges to do everything that AMS supports. This is the default-provided role in the supplied
AMS.confconfiguration file. -
Business User, which can import projects and perform all artifact-level operations.
-
Reviewer, Reviewer, which can approve or reject committed artifact modifications.
-
AMSDeploy, which can deploy an artifact,
MyArtifact, from projectMyProject. To deploy an artifact, a user must have the deploy privilege on the artifact being deployed. Note that if MyArtifact is replaced with * or is absent in the example below, then the user is permitted to deploy any artifact from projectMyProject.
![[Note]](images/note_826758100.png) | Note |
|---|---|
|
AMS 1.1.0 replaced the privilege |
// RoleToPrivilegeMappings-AMS-example.conf
//
// File that contains the privileges for each AMS role.
RoleToPrivilegeMappings = {
// Map of roles to permissions
privileges = {
Administrator = [
{
privilege = "*"
}
]
Business User = [
{
privilege = "project:import"
}
{
privilege = "artifact:*"
}
]
Reviewer = [
{
privilege = "project:approve"
}
]
AMSDeploy = [
{
privilege = "artifact:deploy"
resource = "MyProject/MyArtifact"
}
]
}
}
User Role Privileges
The following are the configurable privileges supported for each user role.
| Privilege | Description |
|---|---|
| * | Allows full access to all AMS resources. |
| privilege: project[:<operation>] resource: [<project-name>] | This hierarchical permission controls access to AMS projects. It contains between one and three elements delimited with colons. The second element specifies the project operation as follows:
|
| privilege: artifact[:<operation>] resource: [<project-name>/<artifact-name>]] | This hierarchical permission controls access to artifacts. It contains between one and three elements delimited with colons. The second element specifies the artifact operation as follows:
|
| manage_permissions | Users with this top-level permission are allowed to manage users, roles, and permissions. There is no action or object instance associated with this permission; users with this permission can manage all users, roles, and permissions, while users without it are not permitted to manage users, roles, or permissions. |
| manage_server | Users with this top-level permission are allowed to manage the AMS server, including creating and deleting deployment descriptors, viewing active login sessions, releasing locks held by other users, and shutting down the server. There is no action or object instance associated with this permission. |
Local Authentication Realm Configuration Example
The following example shows a configuration file in HOCON format that defines four users: the default admin user name and its assigned AMSAdmin role, and three users and their assigned roles.
// LocalAuthenticationRealm.conf
//
// File the defines users and their roles
LocalAuthenticationRealm = {
// Users and their passwords and roles. Passwords can be enciphered with the
sbcipher utility for additional security.
principals = [
{
userName = "admin"
password = "admin"
roles = ["AMSAdmin"]
}
{
userName = "Amy"
password = "Amy"
roles = ["Administrator"]
}
{
userName = "Bill"
password = "Bill"
roles = ["Business User"]
}
{
userName = "Rob"
password = "Rob"
roles = ["Reviewer"]
}
]
}
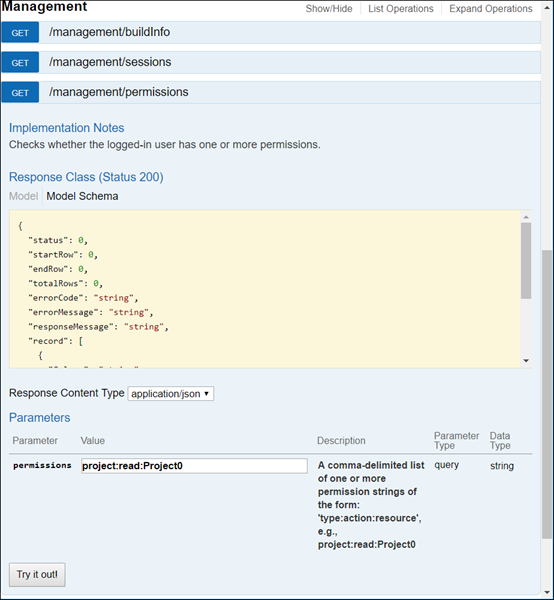
Querying the AMS API for User Permissions
The AMS REST API supports queries and returns a set of records, one for each permission string in the query, which indicates whether the logged-in user has the requested permission.
Consult your AMS administrator for the site-specific URL to access the API.
-
From the API, log in with your AMS username and password.
-
Select the Management API and expand to /Management/Permissions.
-
Enter a value in the
permissionsfield and click the button to determine the permission present.
 |