This chapter describes the architecture and management of the TIBCO Streaming security model. See the overview discussions of this model in the StreamBase Security Model section of the StreamBase Admin Guide.
Access control is done with users, which are formally known as principals. A principal has a credential (password) and they are granted one or more roles. Principals are managed using administration commands.
A user who installs a node is automatically granted administrative access to the node. This user is defined as a valid principal for the node. There is no password associated with this user and they can only access the node using the trusted host mechanism (see Trusted Hosts). To use the standard user name and password authentication mechanism this user must be updated to have a password.
This user has full administrative control of the installed node when logged in from a trusted host.
It is also possible to specify a different user at node installation. This user must specify a password at node installation since the user name is different than the operating system user that is installing the node. This user is also granted full administrative access to the installed node. See Default Security for details.
Apart from the user that installed the node, other users may administer the node only if they are granted administration privileges using a role. See Roles for complete details on the default security roles.
Every node has a node administration realm. This realm is used to perform all authentication related to node administration.
You can use administration clients without authentication to view some public properties for each node on the network. These are the properties published by the discovery service.
Access to all other node details — and to the managed elements contained within the node — is controlled via the security service. To access these elements, you need to be authenticated. Authentication is performed for each command executed using the command line client. JMX authentication is specific to the JMX tool.
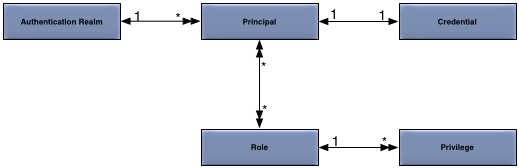
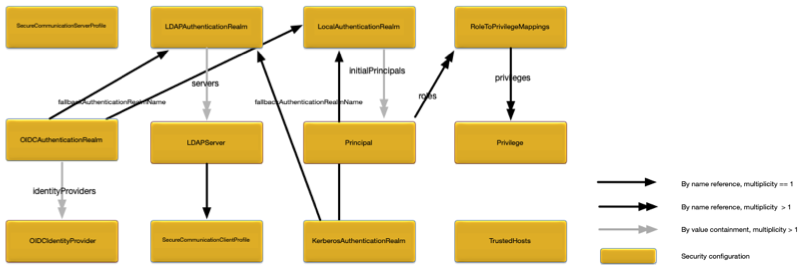
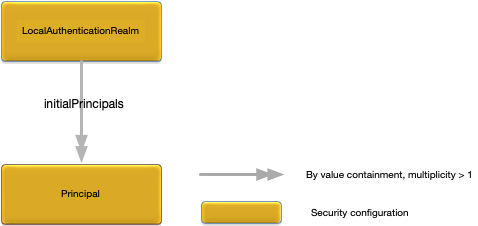
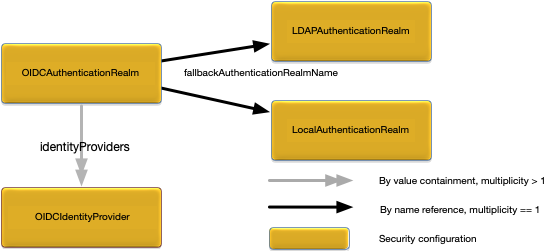
The security model is defined more formally in Figure 1, “Security Model”.
The concepts in the security model are:
-
Principal — an entity (a user) that can be positively identified and verified via a technique known as authentication.
-
Credential — password used to control access to information or other resources.
-
Authentication Realm — defines the authentication scheme for principals. All principals in the same authentication realm use a common authorization and credential management mechanism.
-
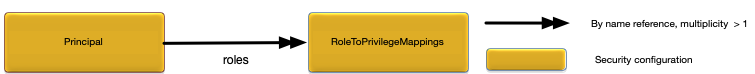
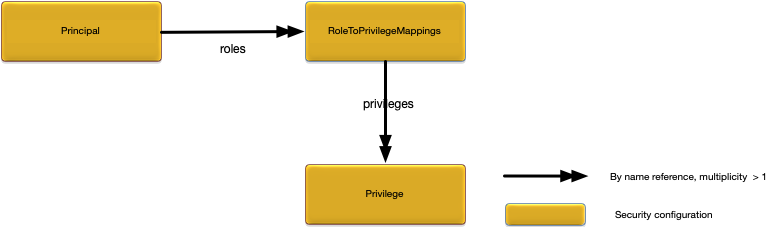
Privilege — grant access to a resource, for example an administration command.
A principal definition contains one or more role names that define the privileges granted to the principal.
Administrative commands issued to multiple nodes using a partially qualified service name must use one of these authentication mechanisms:
-
the principal and credential provided to the administrative command must be defined on all targeted nodes when using a local authentication realm (see Local Authentication Realm).
-
all target nodes must use the same external authentication mechanism, for example LDAP or an OpenId Connect identity provider (see Authentication Realms).
-
the target nodes for the administrative command must have the client host on which the administration command is being executed defined as a trusted host (see Trusted Hosts).
The choice of authentication mechanism is dependent on local security polices and whether the application is deployed into a trusted network. For example, the use of trusted host authentication would not be appropriate on an untrusted network.
Note
It is recommend that security policy be consistent across all nodes in a cluster. Mixing different authentication realms, or inconsistent user definitions, can easily lead to security vulnerabilities.
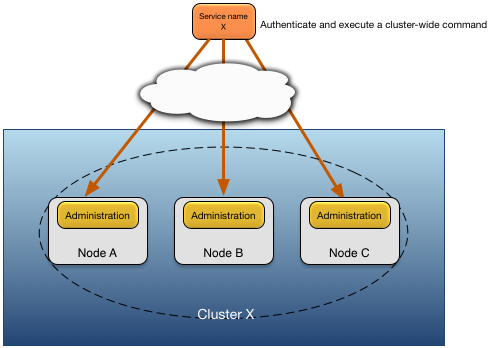
Figure 2, “Cluster authentication model” shows the use of common principal and credential information in a cluster.
Sensitive data stored in configuration files is encrypted using a
master secret cryptographic key. A master secret is
created using the create secret administration command
(see epadmin-secret(1)). This command generates a random
cryptographic shared secret and stores it in a user-specified key store file which is
encrypted with a user-specified password.
Once a master secret key store has been created it can be used to encrypt sensitive
data using the encrypt secret administration command.
The generated encrypted data can then be pasted into configuration files that store
sensitive data, for example passwords.
The master secret must be installed on a node to enable that node to decrypt sensitive data. This is done:
-
when a node is installed using
install node. -
using the
load secretadministration command if a node is already running.
Once a master secret has been installed on a node, the node will use it to decrypt any encrypted data. Until a master secret has been provided to the node, any attempt to activate node configurations containing encrypted data will fail. A master secret cannot be changed after it has been installed on a node.
Secure network connectivity is defined using secure communication profiles. These profiles define characteristics such as:
-
key stores.
-
trust stores.
-
the secure transport protocols to use, or not use.
-
the cipher suites to use or not use.
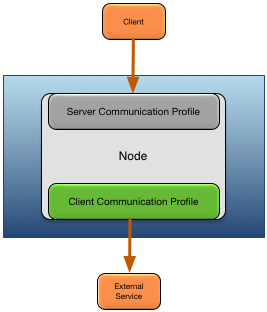
There are both client and server profiles. Client profiles define the security characteristics for outbound connections to external systems and nodes. Server profiles define the security characteristics for network listeners started by nodes and engines. This is shown in Figure 3, “Secure communication profiles”.
Secure client communication profiles are configured using the SecureCommunicationClientProfile root configuration object described
in Kerberos Authentication Realm.
Secure server communication profiles are configured using the SecureCommunicationServerProfile root configuration object described
in Secure Communication Server
Profile.
A secure server communication profile is used to control the security characteristics of these listeners:
-
data transport listener
-
administration (
epadmin) listener -
web server listener
See Communication for details on configuring a SecureCommunicationServerProfile for these listeners. See [Accessing a node section to be ported] for details on specifying credentials when using epadmin.
Key and trust stores are supported both for node security and epadmin client security.
-
Trust stores are used to validate a node's or client's certificates.
-
Key stores contain certificates and private keys when using client authentication.
These key and trust store encoding types are supported on nodes and can be specified in secure communication profiles:
-
all Java key and trust store types, for example Java Key Store (JKS) and Java Cryptography Extension Key Store (JCEKS). Actual supported types are dependent on the installed JRE being used by a node.
-
Public-Key Cryptography Standards #12 (PKCS12)
These key and trust store encoding types are supported by the epadmin client:
-
Public-Key Cryptography Standards #12 (PKCS12)
-
Privacy Enhanced Mail (PEM) format
Authentication is based on authentication realms associated with users. A user is uniquely identified by a user name, and has a set of attributes. These attributes include:
-
Authentication Realm — Authentication realm in which user is defined.
-
Password Expiration — The duration in days that the password is valid.
-
Trusted Hosts Only — Allow access only from trusted hosts, or from any host (defined by authentication realm).
-
Password Required — Define whether a password is always required, or only from untrusted hosts (defined by authentication realm).
-
Automatic Secure Communication Authentication — Define whether a user is automatically authenticated without a password when connecting over a secure (e.g. TLS) communication channel (defined by authentication realm).
These attributes are defined using administrative commands, or loading and activating configuration files.
See epadmin add user for details on how a user is defined.
Authentication verifies that a given user is valid and that the presented password matches the password defined for the user. The presented password is validated using the mechanism defined by the authentication realm. Once authentication succeeds, all work done in the context of the current administration command will be done in an authenticated session for that user. Any access to secured resources during that session will require that the user was granted a role which has access privileges for the resource. User definitions may be updated, for example to change the password, or the set of granted roles. See epadmin update user for details on how to update an existing user definition.
All authentication realms support configuration of trusted hosts, which allows authentication to occur without providing a user name and password. If the authentication request originates from a trusted host, the security service trusts the host-based authentication mechanism (e.g. UNIX login) on that host to have verified the identity of the user.
Warning
As implied by the name, the trusted hosts mechanism should only be used on tightly controlled private operational networks. The integrity of the trusted host mechanism relies on the access control and auditing of the host operating system. The trusted hosts mechanism is not appropriate for public networks, or general company wide private networks, and it should be disabled.
Trusted hosts can be specified using:
-
IPv4 network addresses, for example
127.0.0.1. -
IPv6 network addresses, for example
::1. -
Simple host name, for example
myhost. -
Fully Qualified Domain Names (FQDN), for example
myhost.acme.com. -
Partially Qualified Domain Names (PQDN), for example
*.acme.com. -
IPv4 Classless Inter-Domain Routing (CIDR) blocks, for example
192.168.2.0/24.
When a node is installed all network interfaces are automatically added as trusted hosts. For example, a node may automatically have these network addresses added as trusted hosts:
epadmin --servicename=A.X display security --type=hosts [A.X] Network Address = 0:0:0:0:0:0:0:1%lo0 [A.X] Host Name = localhost [A.X] Source = default [A.X] Network Address = fe80:0:0:0:0:0:0:1%lo0 [A.X] Host Name = localhost [A.X] Source = default [A.X] Network Address = 127.0.0.1 [A.X] Host Name = localhost [A.X] Source = default ...
An example of using trusted hosts with epadmin is below. In this example host1 is a trusted host for the node running on host2. The username and password global parameters cannot be specified when using trusted
hosts. Specifying the username and password parameters disables the trusted host mechanism and causes
the epadmin command to use the
standard authentication mechanism defined by the authentication realm.
// // Command executed on host1 and accessing a node on host2 // epadmin --hostname=host2 --adminport=1234 display node // // Command executed on host1 and accessing a node on host2 // epadmin --servicename=A.X display node
When the display node command is executed on
host1, the name of the user that executed the command
is determined from the operating system. The user name is sent to the node on which
the command is being executed (host2) and if the
command came from a trusted host (host1),
authentication succeeds.
Trusted hosts are defined using configuration (see epadmin-trusted(1) for details), as illustrated in the following example:
name = "trusted-hosts"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
TrustedHosts =
{
hosts =
[
"host1",
"host2",
"*.some.domain.org",
"host4.tibco.com",
"189.4.5.6",
"192.168.2.0/24",
"2601:646:4102:9184:d56c:b9bc:f9ed:1ee4%en1"
]
}
}
The example configuration defines these trusted hosts:
As mentioned above, the test for a trusted host is performed when an epadmin client connects to a node. The IP address of the client machine on which epadmin is executed is compared to the trusted host IP addresses. It is important to realize that the trusted host check is always done using IP addresses, not DNS names. The implications of this are as follows for each of the trusted host configuration types:
-
IPv4 and IPv6 network addresses are compared directly.
-
Simple host names, and fully qualified domain names, are resolved to an IP address when a configuration is activated. If the IP address of this simple host, or fully qualified domain name, changes after the configuration has been activated, the host is no longer trusted.
-
Partially qualified domain names are not resolved to an IP address when a configuration is activated. As clients connect to a node, if there is a configured partially qualified domain name, a reverse DNS lookup is done using their IP address to determine if the client is connecting from a host in the partially qualified domain name.
-
CIDR blocks configure a range of IP addresses to be trusted. As clients connect to a node, if there is a configured CIDR block, their IP address is algorithmically compared to the configured CIDR block.
Trusted hosts can be defined when a node is installed by specifying the trusted host configuration to install node as described in Overriding Default Configuration.
All access through a web service endpoint must be
authenticated using HTTP basic access authentication.
This requires the HTTP user agent, for example a web browser, to provide a user
name and password. The user name and password is authenticated by the
authentication realm associated with the web service. By default, web service
authentication uses the node administration realm. The authentication realm to use
can be changed per web service using the WebServiceBinding configuration object (see WebServiceBinding) in a node deploy configuration. It is also possible
to disable authentication for a web service using the WebServiceBinding configuration object.
Warning
In general, disabling authentication is not recommended. Only disable authentication after a full evaluation of the security implications.
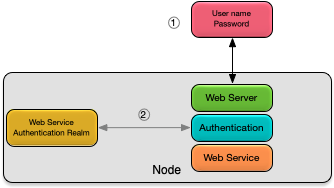
As shown in Figure 4, “Web services authentication” web services authentication consists of these steps:
-
a username and password are sent from the client user agent.
-
the username and password are authenticated using the web service authentication realm.
Web services support the local (see Local Authentication Realm) and LDAP (see LDAP Authentication Realm) authentication realms with no support for trusted hosts. This implies that a valid username and password must always be provided when accessing a web service endpoint. The default user created when a node is installed (see Default Security) is not typically useful for accessing web service endpoints because the password is not known. Additional users should be added as required to support access to web service endpoints, for example, if a local authentication realm is being used, users should be added to the realm as described in epadmin add user.
There may be additional authentication required by the endpoint implementation. See Supported Web Services for details.
The epadmin command-line tool provides administrative access to nodes running on both local and remote hosts. Some commands sent to nodes running on remote hosts are executed using Secure Shell (SSH) connections. SSH is a tool which provides authentication and confidentiality for network connections to remote hosts.
SSH is used when there is not a node coordinator running on the remote node. Specifically these epadmin commands use SSH when the global hostname parameter specifies a non-local host.
-
install node
-
start node --installpath=
<path> -
remove node --installpath=
<path> -
getadminport node --installpath=
<path>
SSH requires configuration of authentication keys for the operating system user who executes the remote command. Authentication keys for SSH are generated using the ssh-keygen command-line tool. See the ssh-keygen manual page (run man ssh-keygen from a terminal) for further information on how to generate authentication keys, and where the keys must be stored for SSH to make use of them.
TIBCO Streaming uses authentication realms to define authentication mechanisms and common principal and credential management. Multiple authentication realms can be active at the same time. These authentication realms are supported:
-
Kerberos
-
LDAP
-
Local
-
OpenId Connect
Realm management is provided by the realm administration
target. See epadmin-realm(1).
Node administration can use either a local (the default) or an LDAP authentication realm.
A Kerberos authentication realm supports Kerberos single signon authentication using one or more Kerberos Key Distribution Centers (KDC). Kerberos is only supported via the HTTP Simple and Protected [GSSAPI] NEGOtiation (SPNEGO) protocol; non-HTTP communication is not supported.
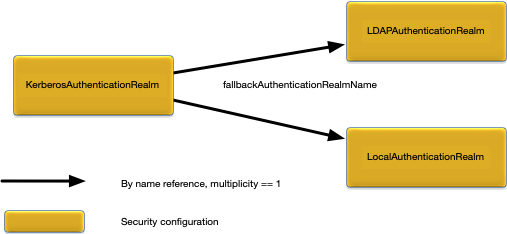
The Kerberos authentication realm only supports authentication, there is no support for authorization. To support authorization a fallback realm must be specified to provide authorization services.
A Kerberos authentication realm is configured using the KerberosAuthenticationRealm root configuration object. See
Kerberos Authentication Realm.
An LDAP authentication realm performs authentication against a set of LDAP servers with potentially disjoint user populations. The realm supports any number of LDAP servers, each with different search properties, authentication mechanisms, and secure communication profiles. Multiple LDAP servers can be used for high availability (replicas of the same server), for unifying disjoint user communities, or both. When multiple LDAP servers are configured in a realm, they are tried in turn, always starting with the first server configured in the realm configuration, until a server responds with a positive authentication, or the request fails on all servers.
These mechanism are supported for authentication:
-
Local password verification: the user's password is queried from the LDAP server over a connection authenticated with system credentials, and sent to the realm LDAP client, which compares it with the password provided by the user being authenticated. If the provided user password is encrypted, it is decrypted using the master secret (see Sensitive Data Encryption) before comparing with the password returned by the LDAP server. This mechanism is used in cases where the LDAP server does not support remote password verification.
-
Remote password verification: the user's password is sent to the LDAP server over a connection authenticated with system credentials, and the LDAP server compares it with the user's LDAP password. If the password sent to the server for comparison is encrypted, it is decrypted by the master secret manager (see Sensitive Data Encryption) before sending to the LDAP server. This mechanism is preferred to local verification, even when using a secure LDAP connection, because the user's actual password never leaves the LDAP server.
-
Bind: the realm attempts to connect to the LDAP server using the user's name and password, and authentication succeeds if the connect attempt succeeds.
Support is also provided for:
-
not requiring a password when connecting over a secure communication channel, like TLS, and that connection uses client (mutual) authentication. The authenticated user is provided by the server network listener, which is responsible for mapping the client X.509 certificate's subject Distinguished Name (DN) to a user name. See Secure Communications Server for more details on how this is accomplished.
-
require a password even when connecting from a trusted host.
An LDAP authentication realm is configured using the LDAPAuthenticationRealm root configuration object. See LDAP Authentication Realm.
The LDAP authentication realm can be used as the authentication realm for node administration. It can also function as a fallback realm.
All nodes support a native local authentication realm. This realm provides both authorization and authentication on a per-node basis. Users and their associated attributes are stored locally in a node's transactional memory. A cluster must have the same local authentication realm configuration and users defined to ensure a consistent security policy. Also all user level enforcement, for example password expiration and account locking, are done per node. So it is possible that a user may be locked out on one node, but can still can access other nodes in the cluster.
The local authentication realm supports these features:
-
password validation.
-
access control via one or more roles.
-
password expiration.
-
account locking.
-
automatic account locking after a number of failed login attempts.
-
requiring a password even when connecting from a trusted host.
-
not requiring a password when connecting over a secure communication channel
There is also support for configuring a set of initial users that should be defined on the node allowing administrators to bulk-load users rather than creating them individually.
User administration is provided by the user
administration target (see epadmin-user(1)) and password management is provided by
the password target (see epadmin-password(1)). Support for backing up and
restoring the local realm is provided by the realm
administration target (see epadmin-realm(1)).
A local authentication realm is configured using the LocalAuthenticationRealm root configuration object. See Local Authentication Realm.
The local authentication realm can be used as the authentication realm for node administration. It can also function as a fallback realm.
An OpenId Connect (OIDC) realm uses a list of OIDC identity providers to perform single sign-on authentication. OIDC is only supported via the HTTP protocol; non-HTTP communication is not supported.
The OIDC authentication realm only supports authentication, there is no support for authorization. To support authorization a fallback realm must be specified to provide authorization services.
An OIDC authentication realm is configured using the OIDCAuthenticationRealm root configuration object. See OIDC Authentication Realm.
Privileges are used to control access to specific resources, for example administrative commands.
Privileges are granted to roles. Each role defines a set of privileges associated with a
specific resource. The only valid privilege for administration commands is
AdminRunCommand. The AdminRunCommand privilege indicates that the command specified as a
resource can be executed by the associated role. Administrative command resource
names are specified as <target>.<command>. Other
resource types support different privileges and resource naming conventions.
Roles and their associated privileges are defined using configuration. For example,
the following configuration file allows the administrator role to run the start
mytarget and stop mytarget administrative
commands, and the monitor role to run the display mytarget command.
name = "my-target-role-mappings"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
RoleToPrivilegeMappings =
{
privileges =
{
administrator =
[
{
resource = "mytarget.start"
privilege = "AdminRunCommand"
},
{
resource = "mytarget.stop"
privilege = "AdminRunCommand"
}
]
monitor =
[
{
resource = "mytarget.display"
privilege = "AdminRunCommand"
}
]
}
}
}
Once the above configuration is activated, the security service will enforce that
only principals who have been assigned the administrator
role are allowed to run the start mytarget and
stop mytarget commands and those who have been assigned
the monitor role are allowed to run the display mytarget command.
Warning
Failing to grant privileges to an administration command will prevent those commands from being run by any principal.
The security service supports a set of predefined roles that are used to grant privileges to principals.
The predefined roles are:
-
administrator— allows modification of the operational state of a node. This includes control of a node's lifecycle, e.g. Installation, starting, stopping, and removal. -
monitor— allows monitoring of the operational state of a node.
Each of these roles is described in more detail below.
The administrator role
assigns administrative privileges to principals. The administrator role is automatically granted to the user who
installed the node. That user always has full administrative control of the node
when logged in on the same host. All operations which modify the operational
behavior of a node may only be executed by principals which have administrator role privileges. Operational control of a node
occurs via epadmin and JMX. This role should be
granted to principals that can perform operations that modify the node state.
The monitor role assigns
system monitoring privileges to principals. This role is granted execute
permission to all display-type administrative operations. Consequently, this role
should be granted to principals who can monitor node status. Such principals will
be able to display the state of a node, but will be unable to execute
administrative operations which change the operational state of the node.
Security monitoring and
administration is done from the node Security tab. The
following commands are accessed from the Security tab.
-
AddLocalauthentication source. See epadmin add user. -
Export— export the node'slocalauthentication realm's user configuration. See epadmin export configuration. -
Remove— remove a user definition from the node'slocalauthentication realm. See epadmin remove user. -
Reset— change a password in the node'slocalauthentication realm. See epadmin-password(1). -
Update— update a user definition, other than password, in the node'slocalauthentication realm. See epadmin update user.
Figure old-and-gone shows the security information displayed from the Security tab.
This screen consists of these sections:
-
Principals — all principals defined in the
localauthentication realm for this node. -
Authentication Sources — all realms being used by this node.
-
Trusted Hosts — the trusted hosts used by this node.
The Principals section shows this information for each
principal defined in the node's local authentication
source:
-
Realm Name — realm in which user is defined.
-
User Name — principal name.
-
Password Expiration (Days) — the password expiration time in days. A value of zero indicates that the password does not expire.
-
Account Locked —
trueif the user account is locked,falseif the account can still be accessed. -
Lock Reason — reason account is locked.
-
Time Remaining Before Auto-Unlock (minutes) — time remaining before a locked user is automatically unlocked, or
disabled, if auto-unlock is disabled. -
Failed Login Lockout Threshold —
enabledif failed login lockout is enabled,disabledif lockout is disabled. -
Failed Login Lockout Duration (minutes) — failed login attempt lockout duration in minutes.
-
Roles — roles granted to this principal.
-
Authentication via Secure Communication Allowed — is a password required when connecting over a secure communication channel?
-
Password Always Required — is a password required even when connecting from a trusted host?
-
Trusted Host Membership Required of Client — is user only allowed to connect from a trusted host?
This information can also be displayed using:
epadmin --servicename=<node-service-name> display user
The Authentication Sources section shows this
information for each configured authentication realm:
-
Realm Name — Authentication realm name.
-
Realm Type — Authentication realm type description.
-
Referenced By — List of entities using this realm.
This information can also be displayed using:
epadmin --servicename=<node-service-name> display realm
The Trusted Hosts section shows this information for
each trusted host:
-
Network Address — IP address for a trusted host.
-
Host Name — the host name for a trusted host. This field may be empty if a trusted network address cannot be resolved to a host name using a reverse Domain Name Service (DNS) lookup.
-
Source — the source of the trusted host. This field may contain one of:
-
default— this host was discovered using the local machine's network interfaces (see Trusted Hosts), for example::1. -
configured— this trusted host was an explicitly configured IPv4, IPv6, or FQDN network address (see Trusted Hosts), for examplemyhost.acme.com. -
a PQDN — this host is trusted because of a configured PQDN. The network address was resolved to a FQDN using a reverse DNS lookup and then matched to a PQDN, for example
*.acme.com. -
a CIDR block — this host is trusted because of a configured CIDR block. The network address is within the configured CIDR block, for example
192.168.2.0/24.
-
This information can also be displayed using:
epadmin --servicename=<node-service-name> display trusted
Users are added to a node's local authentication realm using the Add
Principal dialog accessed from the Add button.
The fields in the Add Principal dialog are:
-
User Name — A unique name for this user.
-
Password — Initial password for this user.
-
Confirm Password — Password confirmation.
-
Roles — A space separated list of roles to assign to this user.
-
Password Expiration (Days) — Password expiration in days. A value of zero indicates that the password does not expire.
-
Locked — Locked account setting.
Clicking on the Submit button will add the new user to
the node after validating that the password values match.
Added users are never removed unless explicitly removed as described in epadmin remove user.
Users can also be added using:
epadmin --servicename=<node-service-name> add user \ --username=admin --password=supersecret --roles=administrator
All principals defined in a local authentication realm
on a node can be backed up using the Export Users
dialog. This dialog is accessed from the Export
button. The realm backup can be reloaded on a node using the restore realm
administration command (see epadmin remove
user).
The fields in the Export Users dialog are:
-
Name — Local authentication realm to backup.
-
File — Backup to this file.
When the Submit button is clicked, the realm is backed
up to the specified file. No sensitive information, such as passwords is visible in
the exported file.
Local authentication realms can also be backed up using this command:
epadmin --servicename=<node-service-name> backup realm --name=default-realm > default-realm.backup
Local authentication realms can be restored using this command:
epadmin --servicename=<node-service-name> restore realm --name=default-realm \
--file=/opt/backups/default-realm.backup
Passwords are changed in a local authentication realm
using the Reset Password dialog accessed from the
Reset button.
The fields in the Reset Password dialog are:
-
User Name — User name of password being changed. This field is read-only. It is set to the user selected in the
Principalstable. -
Password — New password.
-
Confirm Password — Confirm password.
When the Submit button is clicked the password has
been changed.
Passwords can also be changed using this command:
epadmin --servicename=<node-service-name> change password --realm=default-realm --username=admin
Users defined in a local authentication realm are
removed from a node by selecting a principal in the Principals table and clicking on the Remove button.
When the Submit button is clicked the user has been
removed.
Principals can also be removed using this command:
epadmin --servicename=<node-service-name> remove user --realm=default-realm --username=admin
User defined in a local authentication realm are updated
using the Update Principal dialog accessed from the
Update button.
The fields in the Update Principal dialog are:
-
User Name — User name being updated. This field is read-only. It is set to the user selected in the
Principalstable. -
Roles — A space separated list of roles for this principal.
-
Password Expiration (Days) — Password expiration in days. A value of zero indicates that the password does not expire.
-
Locked — Optionally lock the user account.
The fields contain the current values for the user when the dialog is initially
displayed. When the Submit button is clicked any
changed values are updated for the user.
Users can also be updated using this command:
epadmin --servicename=<node-service-name> update user \
--username=admin --roles=administrator
The authentication realm associated with node administration is set by default to a local authentication realm when a node is installed (see Default Security). The default node administration authentication realm cannot be changed using configuration. For example the following fails:
//
// New configuration using an
// authentication realm name of default-realm
// (the default authentication realm name)
//
name = "my-local-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LocalAuthenticationRealm =
{
name = "default-realm"
requirePassword = false
initialPrincipals =
[
{
userName = "guest"
password = ""
roles =
[
"administrator"
]
}
]
}
}
//
// Load configuration
//
epadmin --servicename=A.X load configuration --source=realm.conf
[A.X] type = com.tibco.ep.dtm.configuration.security
[A.X] name = my-local-authentication-realm
[A.X] version = 1.0.0
//
// Activation fails because default local authentication realm
// cannot be changed
//
epadmin --servicename=A.X activate configuration \
--type=com.tibco.ep.dtm.configuration.security \
--name=my-local-authentication-realm --version=1.0.0
[A.X] Audit failed: TIBCO-EP-DTM-00277: configuration (my-local-authentication-realm,
com.tibco.ep.dtm.configuration.security, 1.0.0) contains an authentication realm with
name "default-realm", which already exists in
(default-realm-config, com.tibco.ep.dtm.configuration.security, 1.0.0)
However, it is possible to change the authentication realm associated with node administration to either a different local authentication realm or an LDAP authentication realm. Here are the required steps to change the node administration realm:
-
Load and activate a local (see Local Authentication Realm) or LDAP (see LDAP Authentication Realm) realm configuration using the configuration administration target (see epadmin-configuration(1)), or as default configuration deployed with an application (see Overriding Default Configuration).
-
Use the setadmin realm administration command to change to the new realm (see epadmin setadmin realm).
This example defines a single administration user named admin in a new local authentication realm and then updates node
administration to use this new realm.
name = "my-local-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LocalAuthenticationRealm =
{
name = "my-local-authentication-realm"
requirePassword = false
initialPrincipals =
[
{
userName = "admin"
password = "admin"
roles =
[
"administrator"
]
}
]
}
}
//
// Display the current node administration realm
// This command is using the operating system
// user that installed the node so no
// user name or password is required from a trusted host
//
epadmin --servicename=A.X getadmin realm
[A.X] Realm Name = default-realm
//
// Load the realm configuration
//
epadmin --servicename=A.X load configuration --source=realm.conf
[A.X] type = com.tibco.ep.dtm.configuration.security
[A.X] name = my-local-authentication-realm
[A.X] version = 1.0.0
//
// Activate the new realm configuration
//
epadmin --servicename=A.X activate configuration --type=com.tibco.ep.dtm.configuration.security \
--name=my-local-authentication-realm --version=1.0.0
//
// Set node administration to use this realm
//
epadmin --servicename=A.X setadmin realm --name=my-local-authentication-realm \
--newrealmuser=admin --newrealmpassword=admin
//
// Display the updated node administration realm
// The new administrator user name and password must be
// specified since admin is not the operating system user
// that installed the node.
//
epadmin --servicename=A.X --username=admin --password=admin getadmin realm
[A.X] Realm Name = my-local-authentication-realm
When changing the node administration realm the new realm must have at least one
user defined with the administrator role to ensure
that the node can be managed in the new realm. This is verified by the setadmin realm
command by requiring the username and password of an administration user in the new
realm.
Attempting to remove the last administration user in a local authentication realm is also prevented to ensure that a node can always by administered.
epadmin --servicename=A.X --username=admin --password=admin remove user \
--realm=my-local-authentication-realm --username=admin
[A.X] Error: TIBCO-EP-DTM-00481: "admin" is the last remaining user in the realm and cannot be removed.
Warning
There is no audit preventing the last administration user from being removed when using an LDAP authentication realm. If the last administration user is removed from the LDAP server, the node can no longer be accessed for management and must be forcefully removed using operating system facilities.
There are cases where administrators can unintentionally lock out all node administration users. Examples are:
-
Remove the last user with administration privileges.
-
Password expires for administration user.
-
Explicitly lock the administration user's account.
-
Switch to a realm that has no administration users defined.
-
etc.
There are two choices at this point:
-
Remove the node directory and processes using operating system specific mechanisms. This causes an application outage and loss of any data stored on the node.
-
Use the reset authentication command to restore the default authentication set up when a node was installed (see Default Security Configuration).
To reset node authentication, the reset authentication command is executed on the same machine on which the node is installed. Operating system write access privileges to the node installation directory must be available to the user executing the command.
epadmin reset authentication --installpath=A.X
See epadmin-authentication(1) for more details.
Every administrative command is recorded in an audit log (see Logging). For each command executed the audit log reports on:
-
the command and target executed.
-
the principal that executed the command.
-
whether the command succeeded or failed.
-
the failure cause, if the command failed.
This section provides a detailed description of all security configuration. A snippet is provided for each configuration object showing the syntax for specifying all of the configuration values.
Security configuration has a
configuration type of com.tibco.ep.dtm.configuration.security.
The KerberosAuthenticationRealm root configuration object defines
Kerberos authentication for a node. There can only be a single KerberosAuthenticationRealm defined on a node.
Warning
Kerberos requires the local machine to be identified by a fully qualified domain
name (FQDN). Ensure that the local machine is set up to use a FQDN, instead of a
simple host name, by default. If that is not possible, ensure that the FQDN of
the local machine is configured in the Administration.address property of the node deployment
configuration (see Administration). For example:
name = "my.application"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.node"
configuration =
{
NodeDeploy =
{
nodes =
{
"A.X" =
{
communication =
{
administration =
{
address = "myhost.com" // FQDN
webServiceBindings =
{
admin =
{
authenticationRealmName = "kerberos-realm"
}
}
}
}
}
}
}
}
Figure 6, “KerberosAuthenticationRealm relationships” shows the relationships to other configuration objects.
A detailed description of the configuration object properties is in KerberosAuthenticationRealm object properties and a snippet for these properties is in Example 1, “KerberosAuthenticationRealm object snippet”.
KerberosAuthenticationRealm object properties
Example 1. KerberosAuthenticationRealm object snippet
name = "kerberos-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
KerberosAuthenticationRealm =
{
name = "my-kerberos-authentication-realm"
requireTrustedHostMembership = false
fallbackAuthenticationRealmName = "my-local-realm"
internalClientLoginConfigurationFile = "/opt/kerberos/client-configuration"
internalClientKeytabFile = "/opt/kerberos/keytab/client"
internalClientPrincipalName = "client-principal@ACME.COM"
jaasDebug = false
kerberosConfigurationFile = "/opt/kerberos/kerberos-configuration"
serverKeytabFile = "/opt/kerberos/keytab/server"
serverPrincipalName = "HTTP/my.host.com@ACME.COM"
ticketCacheFile = "/opt/kerberos/ticket/cache/file"
}
}
The LDAPAuthenticationRealm
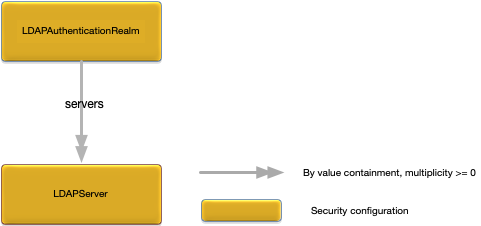
root configuration object defines LDAP integration for a node. Figure 7, “LDAPAuthenticationRealm
relationships” shows the relationships to other configuration objects.
A detailed description of the configuration object properties is in LDAPAuthenticationRealm object properties and a snippet for these properties is in Example 2, “LDAPAuthenticationRealm object snippet”.
LDAPAuthenticationRealm object properties
| Name | Type | Description |
|---|---|---|
|
Boolean |
Automatically authenticate if user is connecting over a secure
communication channel. A value of true
allows automatic authentication, a value of false disables automatic authentication. Optional.
Default value is false.
|
|
|
LDAP server configuration (see LDAP Server). Multiple LDAP servers can be configured. Authentication is attempted to each server in the order they are defined in this configuration property until authentication is successful, or there are no more servers configured. Required. |
|
String | Name of the authentication realm. This name must be unique across all authentication realms. Required. |
|
Boolean |
Require a password if user is connecting from a trusted host unless
automatically authenticated because of a secure communication channel. A
value of true requires a password when
connecting from a trusted host, a value of false allows connection from a trusted host without a
password. Optional. Default value is |
|
Boolean |
A value of true only allows user to connect
from a trusted host, a value of false allows
user to connect from any host. Optional. Default value is |
Example 2. LDAPAuthenticationRealm object snippet
name = "ldap-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LDAPAuthenticationRealm =
{
name = "my-ldap-authentication-realm"
requireTrustedHostMembership = true
allowSecureCommunicationClientAuthentication = true
requirePassword = false
servers =
[
{ ... }
{ ... }
]
}
}
The LDAPServer
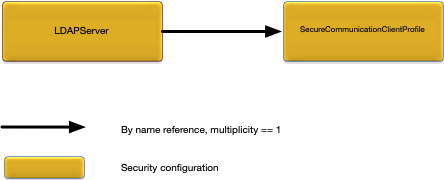
configuration object defines LDAP server configuration. Figure 8, “LDAPServer relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in LDAPServer object properties and a snippet for these properties is in Example 3, “LDAPServer object snippet”.
LDAPServer object properties
| Name | Type | Description |
|---|---|---|
|
String |
LDAP server host name. Optional. Default value is localhost.
|
|
Short |
LDAP server port number. Optional. Default value is 389.
|
|
Enumeration with these valid values, BIND,
LOCAL_PASSWORD_COMPARE, and REMOTE_PASSWORD_COMPARE.
|
The type of authentication to perform. BIND
authenticates principals by connecting to the LDAP server using the
principal name and credentials. LOCAL_PASSWORD_COMPARE authenticates principals by
connecting to the LDAP server using the system principal, searching for
the user, retrieving its password attribute, and comparing the values
locally with the principal's credentials. REMOTE_PASSWORD_COMPARE is the same as LOCAL_PASSWORD_COMPARE except that the comparison is
performed by the LDAP server. Optional. Default value is BIND.
|
|
String |
The password attribute for this LDAP server's principals. Optional.
Default value is userPassword.
|
|
String [ ] | A list of Distinguished Names under which principals are searched for during search-based authentication operations or user name to Distinguished Name conversions. Required. Must contain at least on element. |
|
String |
The LDAP filter expression used when searching for principals. The filter
permits Java pattern substitution expressions. {0} is bound to the input principal and {1} is bound to its corresponding distinguished name.
Optional. Default value is CN={0}.
|
|
String [ ] |
A list of Distinguished Names under which roles are searched for.
Optional. Default value is the principalSearchRoots value.
|
|
String |
The LDAP filter expression used when searching for roles of which a
principal is a member. The filter permits Java pattern substitution
expressions. {0} is bound to the input
principal and {1} is bound to its
corresponding Distinguished Name. Optional. Default value is roleOccupant={1}.
|
|
String |
Attribute of a role entry that is used to map to privileges. Optional.
Default value is CN.
|
|
String | Name of a secure communication client profile to use when configuring secure communications with an LDAP server. Optional. No default value. If not set LDAP server connections are not secure. |
|
String | The system principal password to log in to the LDAP server to perform authentication operations. Opaque passwords are generated using the epadmin secret target. See epadmin-secret(1). Required. |
|
String | The system principal to log in to the LDAP server to perform authentication operations. Required. |
Example 3. LDAPServer object snippet
name = "ldap-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LDAPAuthenticationRealm =
{
servers =
[
{
host = "ldap.primary.acme.com"
portNumber = 390
principalAuthenticationAlgorithm = LOCAL_PASSWORD_COMPARE
principalPasswordAttribute = "password"
principalSearchRoots = [ "ou=users,dc=example.dc=com" ]
principalSearchFilter = "cn={0}"
roleSearchRoots = [ "ou=roles,dc=example.dc=com" ]
roleSearchFilter = "membership={1}"
roleNameAttribute = "roleID"
secureCommunicationProfileName = "secure-ldap-client-profile"
systemPassword = "secret"
systemPrincipal = "cn=SBLDAPUser,cn=Users,dc=ldap,dc=example,dc=com"
}
{
host = "ldap.backup.acme.com"
portNumber = 390
principalAuthenticationAlgorithm = LOCAL_PASSWORD_COMPARE
principalPasswordAttribute = "password"
principalSearchRoots = [ "ou=users,dc=example.dc=com" ]
principalSearchFilter = "cn={0}"
roleSearchRoots = [ "ou=roles,dc=example.dc=com" ]
roleSearchFilter = "membership={1}"
roleNameAttribute = "roleID"
secureCommunicationProfileName = "secure-ldap-client-profile"
systemPassword = "secret"
systemPrincipal = "cn=SBLDAPUser,cn=Users,dc=ldap,dc=example,dc=com"
}
]
}
}
The LocalAuthenticationRealm root configuration object defines the
characteristics and initial principals in the local authentication realm for a
node. Figure 9, “LocalAuthenticationRealm
relationships” shows the relationships to other configuration objects.
Changing the failedLoginLockoutDurationMinutes or
failedLoginLockoutThreshold configuration properties
by activating a new version of this configuration causes this behavior:
-
increasing
failedLoginLockoutThreshold: any users already locked for exceeding the old value remain locked until their durations expire or they are manually unlocked. -
decreasing
failedLoginLockoutThreshold: any users with login fail counts that did not exceed the old value remain unlocked until they fail again and then they are compared with the new value. -
changing
failedLoginLockoutThresholdfrom zero to non-zero (enabling lockout): behaves the same as decreasing the value. -
changing
failedLoginLockoutThresholdfrom non-zero to zero (disabling lockout): behaves the same as increasing the value. -
increasing
failedLoginLockoutDurationMinutes: the next login attempt will use the new duration and will unlock only when it is exceeded. -
decreasing
failedLoginLockoutDurationMinutes: the next login attempt will use the new duration and will unlock only when it is exceeded. -
changing
failedLoginLockoutDurationMinutesfrom non-zero to zero (disabling auto-unlock): users formerly on timed unlock will now remain locked until explicitly unlocked by an administrator. -
changing
failedLoginLockoutDurationMinutesfrom zero to non-zero (enabling auto-unlock): behaves the same increasing the value.
A detailed description of the configuration object properties is in LocalAuthenticationRealm object properties and a snippet for these properties is in Example 4, “LocalAuthenticationRealm object snippet”.
LocalAuthenticationRealm object properties
| Name | Type | Description |
|---|---|---|
|
Boolean |
Automatically authenticate if user connecting over a secure communication
channel. A value of true allows automatic
authentication, a value of false disables
automatic authentication. Optional. Default value is false.
|
failedLoginLockoutDurationMinutes
|
Integer | The number of minutes a user's account will remain locked after being locked for exceeding the lockout threshold. A value of 0 means the account remains locked until it is manually unlocked by an administrator (see epadmin-user(1)). Optional. Default value is 0. |
failedLoginLockoutThreshold
|
Integer | The number of consecutive failed login attempts required before a user's account is locked. A value of 0 disables account locking for failed login attempts. Optional. Default value is 0. |
|
|
Initial set of principals (see Principal) in this realm. The values in this field cannot change when this configuration is updated. If the values do change, configuration audit will fail. Optional. No default value. |
|
String | Name of the authentication realm. This name must be unique across all authentication realms. Required. |
|
Boolean |
Require a password if user is connecting from a trusted host unless
automatically authenticated because of a secure communication channel. A
value of true requires a password when
connecting from a trusted host, a value of false allows connection from a trusted host without a
password. Optional. Default value is |
|
Boolean |
A value of true only allows users to connect
from a trusted host, a value of false allows
users to connect from any host. Optional. Default value is |
Example 4. LocalAuthenticationRealm object snippet
name = "local-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LocalAuthenticationRealm =
{
name = "my-local-authentication-realm"
requireTrustedHostMembership = true
allowSecureCommunicationClientAuthentication = true
requirePassword = false
failedLoginLockoutDurationMinutes = 5
failedLoginLockoutThreshold = 3
initialPrincipals =
[
{ ... }
{ ... }
]
}
}
The OIDCAuthenticationRealm
root configuration object defines OpenId Connect authentication for a node.
Figure 10, “OIDCAuthenticationRealm
relationships” shows the relationships to other configuration objects.
A detailed description of the configuration object properties is in OIDCAuthenticationRealm object properties and a snippet for these properties is in Example 5, “OIDCAuthenticationRealm object snippet”.
OIDCAuthenticationRealm object properties
| Name | Type | Description |
|---|---|---|
|
String | The default address to redirect a user to after authentication if no redirect URL was provided in the authentication request. Optional. Default value is null. |
|
Associative array of OIDCIdentityProvider
configuration objects keyed by identity provider names.
|
An associative array of OIDCIdentityProvider
(see OIDCIdentityProvider object
properties) configuration objects indexed by provider names. Provider
names must be URL safe and non-empty. Required.
|
|
String |
The name of the realm used for all authorization. This must be the name
of an active LDAPAuthenticationRealm or
LocalAuthenticationRealm. If the fallback
realm is not defined, configuration activation will fail. Required.
|
|
String | Name of the authentication realm. This name must be unique across all authentication realms. Required. |
|
Integer | The amount of time to wait for a provider's response in seconds before timing out. Optional. Default is 300 seconds. |
|
Boolean |
A value of true only allows users to connect
from a trusted host, a value of false allows
users to connect from any host. Optional. Default value is |
Example 5. OIDCAuthenticationRealm object snippet
name = "oidc-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
OIDCAuthenticationRealm =
{
name = "my-oidc-authentication-realm"
requireTrustedHostMembership = false
defaultRedirectURL = "http://redirect.acme.com"
fallbackAuthenticationRealmName = "my-ldap-realm"
pendingAuthenticationTimeoutSeconds = 600
identityProviders =
{
"Google" = { ... }
"Auth0" = { ... }
}
}
}
The OIDCIdentityProvider object defines the configuration for OpenId Connect providers.
Support is provided for federated identity providers like Auth0. Federated
providers use subject prefixes to map to the actual provider defined in this
configuration. This mapping is configured using the subjectProviderMappings configuration property. For example:
//
// Subject provider mappings in Auth0 configuration
// A subject prefix of google-oauth2 maps to the
// configured "Google" identity provider
//
subjectProviderMappings =
{
"google-oauth2" = "Google"
}
//
// Auth0 identity contains "sub" claims
//
// The "|" is the delimiter, so "google-oauth2" is the prefix that
// identifies the actual provider providing the identity information.
// 105569619522230371597 is the subject for the principal from the identity
// provider represented by google-oauth2
//
sub: 'google-oauth2|105569619522230371597'
//
// The same principal authenticated directly against "Google"
// would have the same identity information in the "sub" field.
//
sub: '105569619522230371597'
Figure 11, “OIDCIdentityProvider relationships” shows the relationships to other configuration objects.
A detailed description of the configuration object properties is in OIDCIdentityProvider object properties and a snippet for these properties is in Example 6, “OIDCIdentityProvider object snippet”.
OIDCIdentityProvider object properties
| Name | Type | Description |
|---|---|---|
|
String | The client's authentication identifier. Required |
|
String |
The client's authentication secret key. Opaque passwords are generated
using the epadmin secret target. See
epadmin-secret(1). Required.
|
|
String | The identity provider's Document Discovery URL for obtaining discovery information. Required. |
|
String | The attribute in a given principal's ID Token to be used as the identity for this principal. Required. |
|
Associative array of subject prefixes to identity provider names. |
Map federated identity provider subject prefixes to configured identity
provider names. The provider names must be configured in this
configuration. This field is only valid for federated identity providers
like Auth0. Optional. Default is null (no
mappings).
|
Example 6. OIDCIdentityProvider object snippet
name = "oidc-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
OIDCAuthenticationRealm =
{
identityProviders =
{
"Google" =
{
documentDiscoveryURL = "https://accounts.google.com/.well-known/openid-configuration"
clientID = "my-google-client-identifier"
clientSecret = "my-google-client-secret"
identityAttributeName = "email"
}
"Auth0" =
{
documentDiscoveryURL = "https://tibco.auth0.com/.well-known/openid-configuration"
clientID = "my-auth0-client-identifier"
clientSecret = "my-auth0-client-secret"
identityAttributeName = "email"
subjectProviderMappings =
{
"google-oauth2" = "Google"
}
}
}
}
}
The Principal configuration
object defines a principal managed by the local authentication realm. Figure 12, “Principal relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in Principal object properties and a snippet for these properties is in Example 7, “Principal object snippet”.
Principal object properties
| Name | Type | Description |
|---|---|---|
|
Boolean |
Control whether the user account is locked. If true the user account is locked and cannot be accessed,
if false the account is enabled and can be
accessed. Optional. Default value is false.
|
password
|
String | Opaque credential. Opaque text credentials are generated using the epadmin secret target. See epadmin-secret(1). Required. |
|
Integer | An optional expiration time for the password in days. Default value is 0 (no expiration). |
roles
|
String [ ] | An array of role names. Optional. No default. |
userName
|
String | Principal name. Required. |
Example 7. Principal object snippet
name = "local-authentication-realm"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
LocalAuthenticationRealm =
{
initialPrincipals =
[
{
userName = "FredTheAdministrator"
password = "LKJALISJDOIQUWEOIAJSLKDJALSJDL"
roles =
[
"administrator"
]
passwordExpirationPeriodDays = 12
locked = true
}
]
}
}
The RoleToPrivilegeMappings
object defines the roles and their associated privileges. Figure 13, “RoleToPrivilegeMappings
relationships” shows the relationships to other configuration objects.
A detailed description of the configuration object properties is in RoleToPrivilegeMappings object properties and a snippet for these properties is in Example 8, “RoleToPrivilegeMappings object snippet”.
RoleToPrivilegeMappings object properties
| Name | Type | Description |
|---|---|---|
privileges
|
Associative array of Privilege objects keyed
by role name.
|
Role definitions with associated privileges (see Privilege). Required. |
Example 8. RoleToPrivilegeMappings object snippet
name = "my-target-role-mappings"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
RoleToPrivilegeMappings =
{
privileges =
{
administrator = [ ... ]
monitor = [ ...]
}
}
}
The Privilege object
defines permissions for a resource. Figure 14, “Privilege relationships” shows the
relationships to other configuration objects.
A detailed description of the configuration object properties is in Privilege object properties and a snippet for these properties is in Example 9, “Privilege object snippet”.
Example 9. Privilege object snippet
name = "my-target-role-mappings"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
RoleToPrivilegeMappings =
{
privileges =
{
administrator =
[
{
resource = "mytarget.start"
privilege = "AdminRunCommand"
},
{
resource = "mytarget.stop"
privilege = "AdminRunCommand"
}
]
monitor =
[
{
resource = "mytarget.display"
privilege = "AdminRunCommand"
}
]
}
}
}
The SecureCommunicationClientProfile root configuration object defines
a secure communication profile for client connectivity. Figure 15,
“SecureCommunicationClientProfile relationships” shows the relationships to
other configuration objects.
A detailed description of the configuration object properties is in SecureCommunicationClientProfile object properties and a snippet for these properties is in Example 10, “SecureCommunicationClientProfile object snippet”.
SecureCommunicationClientProfile object properties
| Name | Type | Description |
|---|---|---|
excludedCipherSuitePatterns
|
String [ ] |
A list of Java regular expression patterns for excluded cipher suites.
This value is exclusive of the includedCipherSuites property. Optional. Default is
^.*_(MD5|(?<!TLS_DHE_RSA_WITH_AES_\\d\\d\\d_CBC_)SHA|SHA1)$
if no includedCipherSuites are specified.
|
includedCipherSuites
|
String [ ] |
A list of allowed cipher suites. This value is exclusive of the
excludedCipherSuitePatterns property.
Optional. Default is the JRE's full set of supported cipher suites.
|
includedProtocols
|
String [ ] |
A list of allowed protocols. Optional. Default is TLSv1.1 and TLSv1.2. An
empty array uses the JRE's full set of supported protocols.
|
keyPassword
|
String |
The password to access the key within the keystore. Opaque text
credentials are generated using the epadmin
secret target. See epadmin-secret(1). Optional. Default is
keyStorePassword.
|
keyStorePassword
|
String |
Key store password, used to access the key store contents. Opaque text
credentials are generated using the epadmin
secret target. See epadmin-secret(1). Required if keyStore specified.
|
keyStore
|
String | Absolute path to a key store file that contains the client's certificate as well as optional trust store information, depending on key store format. If the key store contains multiple private key entries (aliases), the first is used. This file must be valid on the machine where the client is running. If provided, clients can perform mutual authentication with a server. Optional. No default. |
keyStoreType
|
String |
Key store type (see Key and Trust Stores). Optional. Default is
JKS.
|
name
|
String | The name of the profile. This name must be unique across all secure communication profiles — both client and server. Required. |
requireClientAuthentication
|
Boolean |
Enable (true) or disable (false) required client authentication. If enabled a
keyStore must be configured to sign the
secure communication protocol handshake. Optional. Default is
false.
|
trustStore
|
String | An absolute file path to the trust store used to verify client trust. This file must be valid on the machine where the client is running. Required. |
trustStorePassword
|
String |
The password to access the trust store. Opaque text credentials are
generated using the epadmin secret target.
See epadmin-secret(1). Required if trustStore specified.
|
trustStoreType
|
Enumeration. Valid values are JCEKS,
JKS, or PKCS12.
|
Trust store type (see Key and Trust Stores). Optional. Default is
JKS.
|
Example 10. SecureCommunicationClientProfile object snippet
name = "my-secure-client-settings"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
SecureCommunicationClientProfile =
{
name = "my-secure-client-profile"
keyStore = "/absolute/path/myKeyStore.jks"
keyStorePassword = "secret"
keyPassword = "anothersecret"
keyStoreType = "jceks"
trustStore = "/absolute/path/myTrustStore.jks"
trustStorePassword = "athirdsecret"
trustStoreType = "JCEKS"
requireClientAuthentication = true
excludedCipherSuitePatterns = [ "^.*_(MD5|SHA|SHA1)$" ]
includedProtocols = [ ] // use JRE's supported protocols
}
}
The SecureCommunicationServerProfile root configuration object defines
a secure communication profile for listeners. Figure 16,
“SecureCommunicationServerProfile relationships” shows the relationships to
other configuration objects.
A detailed description of the configuration object properties is in SecureCommunicationServerProfile object properties and a snippet for these properties is in Example 11, “SecureCommunicationServerProfile object snippet”.
SecureCommunicationServerProfile object properties
| Name | Type | Description |
|---|---|---|
excludedCipherSuitePatterns
|
String [ ] |
A list of Java regular expression patterns for excluded cipher suites.
This value is exclusive of the includedCipherSuites property. Optional. Default is
^.*_(MD5|(?<!TLS_DHE_RSA_WITH_AES_\\d\\d\\d_CBC_)SHA|SHA1)$
if no includedCipherSuites are specified.
|
includedCipherSuites
|
String [ ] |
A list of allowed cipher suites. This value is exclusive of the
excludedCipherSuitePatterns property.
Optional. Default is the JRE's full set of supported cipher suites.
|
includedProtocols
|
String [ ] |
A list of allowed protocols. Optional. Default is TLSv1.1 and TLSv1.2. An
empty array uses the JRE's full set of supported protocols.
|
keyPassword
|
String |
The password to access the key within the keystore. Opaque text
credentials are generated using the epadmin
secret target. See epadmin-secret(1). Optional. Default is
keyStorePassword.
|
keyStorePassword
|
String |
Key store password, used to access the key store contents. Opaque text
credentials are generated using the epadmin
secret target. See epadmin-secret(1). Required.
|
keyStore
|
String | Absolute path to a key store file that contains the server's certificate as well as optional trust store information, depending on key store format. If the key store contains multiple private key entries (aliases), the first is used. This file must be valid on the machine where the node is running. Required. |
keyStoreType
|
String |
Key store type (see Key and Trust Stores). Optional. Default is
JKS.
|
name
|
String | The name of the profile. This name must be unique across all secure communication profiles — both client and server. Required. |
requireClientAuthentication
|
Boolean |
Enable (true) or disable (false) required client authentication. If enabled a
trustStore must be configured to verify
client trust. Optional. Default is false.
|
subjectNameElementToUserNameMappings
|
Associative array of certificate based principal names to authorization user names. |
A map whose keys are certificate-based principal names and whose values
are authorization user names. Used in cases where an incoming client
certificate is used for authentication, but none of the elements of its
subject name are suitable for mapping to roles during authorization.
Optional. No default, subject name element extracted with the
userNameObjectIdentifierSearchPath must
yield a valid user name for authorization purposes.
|
trustStore
|
String | An absolute file path to the trust store used to verify client trust. This file must be valid on the machine where the node is running. If provided, servers can perform mutual authentication with clients. Optional. |
trustStorePassword
|
String |
The password to access the trust store. Opaque text credentials are
generated using the epadmin secret target.
See epadmin-secret(1). Required if trustStore specified.
|
trustStoreType
|
Enumeration. Valid values are JCEKS,
JKS, or PKCS12.
|
Trust store type (see Key and Trust Stores). Optional. Default is
JKS.
|
userNameObjectIdentifierSearchPath
|
String [ ] |
An array of attribute keywords, or X.509 object identifiers (OIDs),
indicating the order in which the client's X.509 certificate subject
Distinguished Name attributes are searched to find a user name for
authorization purposes. This key is only relevant if requireClientAuthentication is enabled and a trust store
is present. Supported attribute keywords are userID, CN, emailAddress, and DN.
Optional. Default is the search order emailAddress, CN,
DN.
|
Example 11. SecureCommunicationServerProfile object snippet
name = "my-secure-server-settings"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
SecureCommunicationServerProfile =
{
name = "my-secure-server-profile"
excludedCipherSuitePatterns = [ "^.*_(MD5|SHA|SHA1)$" ]
includedProtocols = [ ] // use JRE's supported protocols
keyPassword = "anothersecret"
keyStorePassword = "secret"
keyStore = "/absolute/path/myKeyStore.jks"
keyStoreType = "jceks"
requireClientAuthentication = true
subjectNameElementToUserNameMappings =
{
"subjectNameElementFoo" = "userNameFoo"
"subjectNameElementBar" = "userNameBar"
}
trustStore = "/absolute/path/myTrustStore.jks"
trustStorePassword = "athirdsecret"
trustStoreType = "JCEKS"
userNameObjectIdentifierSearchPath = [ "userID", "CN", "1.2.3.4", "DN" ]
}
}
The TrustedHosts object
defines trusted hosts. Figure 17, “TrustedHosts relationships” shows
the relationships to other configuration objects.
Multiple TrustedHosts configuration objects with
different configuration names can be active at the same time. When a configuration
is activated, all hosts in the new configuration are added to the trusted hosts for
a node. When a configuration is deactivated, all hosts in the configuration being
deactivated are removed from the trusted hosts for a node unless another active
TrustedHosts configuration also defined the host as
trusted.
A detailed description of the configuration object properties is in TrustedHosts object properties and a snippet for these properties is in Example 12, “TrustedHosts object snippet”.
Warning
IP addresses specified in the hosts configuration
property must be quoted. See Example 12,
“TrustedHosts object snippet”.
Example 12. TrustedHosts object snippet
name = "trusted-hosts"
version = "1.0.0"
type = "com.tibco.ep.dtm.configuration.security"
configuration =
{
TrustedHosts =
{
hosts =
[
"host1",
"host2",
"*.some.domain.org",
"host4.tibco.com",
"189.4.5.6",
"192.168.2.0/24",
"2601:646:4102:9184:d56c:b9bc:f9ed:1ee4%en1"
]
}
}