Configuring Pre-Authentication With OpenID Connect
Identity providers, such as Google or Keycloak, deliver authentication services that conform to the specifications of the OpenID Connect protocol.
When Open ID Connect pre-authentication has been enabled, users navigating to the \ibi_apps context are presented with the sign-in screen of their identity provider instead of the WebFOCUS sign-in screen. Users type their credentials on that screen and send them to the OpenID Connect identity provider. When the identity provider determines that the credentials presented by WebFOCUS and the end user are authenticated, the user is redirected to WebFOCUS.
WebFOCUS prepares a client authentication message that returns its own Client ID to the identity provider and can also include scope identifiers that request additional information about the end user.
When the identity provider authenticates the credentials presented by WebFOCUS, it returns the requested user information, and the authenticated user can begin a session.
When users end their session, they must be directed to the sign-out page used by the identity provider instead of the standard WebFOCUS sign-out page. From the identity provider sign-out page they can choose to sign in to their OpenID Connect identity provider again or move on to other web sites or applications.
Configuring OpenID Connect Authentication Settings at an Identity Provider
As an application that accepts OpenID Connect user authentication, your installation of WebFOCUS functions as a client or relying party in the OpenID Connect Authentication process, and an administrator must create an account for this party with an OpenID Connect identity provider.
Even though each OpenID Connect identity provider maintains slightly different configurations and requirements, all providers must conform to the OpenID Connect standard.
Administrators must expect to provide a Client Name and additional information that uniquely identifies their installation of WebFOCUS to the identity provider. This additional information can include the Root URL for their installation of WebFOCUS, and one or more Valid Redirect URIs that identify the location of the resources that process responses delivered from the identity provider during the sign-in process.
The identity provider creates and provides administrators with a Client ID and a Client Secret that is unique to each installation of WebFOCUS. The identity provider also identifies its Custom Logout Target URL. When users end their WebFOCUS session, they are directed to this URL, where they are free to sign in again to the identity provider or move on to other tasks. Administrators include all of these values in their configuration of the Open ID Connect configuration.
Configuring OpenID Connect Authentication Settings Within TIBCO WebFOCUS
The Edit OpenID Connect Authentication Settings dialog box contains the credentials and endpoint URIs that must be delivered to the OpenID Connect identity provider within client authentication messages, as shown in the following image.
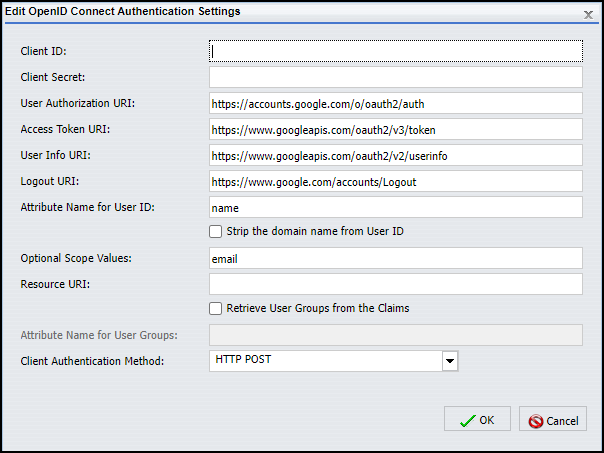
In order to communicate with an OpenID Connect identity provider, credentials that identify WebFOCUS as a valid relying party, which is a web site or application that needs to authenticate the identity of an end user, must be established with the identity provider. These values must be included in responses from that relying party to requests to grant access to authenticated users.
- Client ID. Is the unique ID of your installation of WebFOCUS that identifies it to the OpenID Connect identity provider. This value must be unique for every application supported by the identity provider.
- Client Secret. Is a value shared between WebFOCUS and the identity provider that enables both parties to authenticate messages from each
other. It must be delivered with each request to the OpenID Connect identity provider. The value assigned to the client secret must be sufficiently random as to be unguessable.
For example:
sGBAyfVL7YWtP6gudLIjbRZV_N0dW4f3xETiIxqtokEAZ6FAsBtgyIq0MpU1uQ7J08xOTO2zwP0OuO3pMVAUTid
Identity providers may require a separate sign in before allowing administrators to review and extract this value.
In order to ensure that OpenID authentication requests are directed to the appropriate endpoints, the following URI information must also be included in the Open ID Connect Authentication Settings dialog box.
- User Authorization URI. Identifies the HTTP endpoint at the identity provider authorization server that can authenticate the end user. Requests for user authentication must be directed to this endpoint.
- Access Token URI. Identifies the HTTP endpoint at the identity provider authorization server that can issue access tokens. Requests for tokens for authenticated users must be directed to this endpoint.
- User Info URI. Identifies the protected resource at the identity provider that maintains user information and can return authorized information about the current user when presented with an access token by the client.
- Logout URI. Identifies the HTTP endpoint at the identity provider to which users must be directed when they choose to sign out of all of their sessions authenticated by the OpenID identity provider. Typically, this is the Sign in page for the OpenID identity provider. At this page, users can sign in again to open another OpenID Connect identity provider session or remain signed out. Note that because the logout redirect URI is defined in this field, there is no need to define a logout URL in the Custom logout target URL field of the Authentication Options dialog box.
- Attribute Name for User Id. Identifies the specific attribute that maps to the WebFOCUS User ID. The default value in this field is name. You will most likely replace it with email, which indicates that email addresses using the format, local_part@domain_name, serve as user IDs. Other attribute name values
can be used in this field. For more information about the value to use, consult your identity provider. Values assigned to
this attribute must be unique.
- Strip the Domain Name from User ID. When this check box is selected, the domain name prefix is automatically cleared from a user ID submitted to the identity provider during the sign-in process. This check box is relevant only to customers who use the domain name\user ID format for their user names and work with an OpenID Connect identity provider that does not accept user IDs with a domain name prefix.
- Optional Scope Values. Identifies the names of the optional scope identifiers that can be sent to the identity provider in addition to the required scope identifier, openid. Scope identifiers are requests for specific types of information about the end user who is requesting access to the client. Valid scope identifier values include those defined by the Open ID Connect standard such as, email, address, phone, or profile. The email scope identifier appears in this field, by default, but you can delete it if you and your identity provider do not use it.
- Client Authentication Method. Identifies the HTTP request method that the client authentication message uses to contact the server at the identity provider. The HTTP POST request method is selected, by default. When using this method, client credentials are included in the body of the message. You can also select the HTTP Basic Authentication Scheme request method, in which client credentials are included in the HTTP Authorization Header. We do not recommend that you select the option None, unless your identity provider has advised you to use a different request method not defined in this list.
Configuring OpenID Connect Pre-Authentication with Google
|
How to: |
The Edit OpenID Connect Authentication Settings dialog box is configured with the information required to support pre-authenticated user sign-in requests from Google, by default. Administrators need only add the Client ID and Client Secret, which are provided by Google, and the Attribute Name.
For more information about the Google OpenID Connect API, see https://developers.google.com/identity/protocols/OpenIDConnect
Procedure: How to Configure OpenID Connect Authentication Settings for Google
Before you begin, complete the prerequisites for Pre-Authentication. For more information, see Configuring Pre-Authentication, External Authentication or External Authorization.
We recommend that you use the Export command to back up the Security Settings configuration files before making changes to the Authentication page. For more information, see How to Export Security Configuration Files.
- In the Administration Console, click the Security tab.
- Under the Security Zones folder, expand the Default Security Zone folder and then click Authentication.
- Double-click the OpenID Connect Authentication entry to open the Edit OpenID Connect Authentication Settings dialog box.
- Type the name that identifies WebFOCUS as a valid client of the OpenID Connect provider in the Client ID field.
For example:
292085223830.apps.googleusercontent.com
- Type or copy and paste the Client Secret value provided by Google.
For example:
GBAyfVL7YWtP6gudLIjbRZV_N0dW4f3xETiIxqtokEAZ6FAsBtgyIq0MpU1uQ7J08xOTO2zwP0OuO3pMVAUTid
- To establish Google as your OpenID provider, accept the default values in the following fields:
- User Authorization URI. https://accounts.google.com/o/oauth2/auth
- Access Token URI. https://www.googleapis.com/oauth2/v3/token
- User Info URI. https://www.googleapis.com/oauth2/v2/userinfo
- Logout URI. https://www.google.com/accounts/Logout
- Type a valid attribute name in the Attribute Name for User ID field.
Note: You will most likely replace the default value, name, with the value, email. However, other attribute names can be used in this field. For more information about the value to use, consult your identity provider.
- If you must ensure that any user ID submitted to the identity provider excludes a domain name prefix, select the Strip the Domain Name from User ID check box. Otherwise, leave this check box clear.
Note: This check box is relevant only to customers who use the domain name\user ID format for their user names and work with an OpenID Connect identity provider that does not accept user IDs with a domain name prefix.
- Accept the default value, email, displayed in the Optional Scope Values field.
- Accept the default selection, HTTP POST, displayed in the Client Authentication Method list.
- When your configuration is complete, click OK.
- Enable the new configuration as described in How to Enable OpenID Connect Authentication in a Security Zone.
- Save the new configuration as described in How to Save an OpenID Connect Configuration.
Configuring OpenID Connect Pre-Authentication with Keycloak
|
How to: |
Keycloak is an open source Identity and access management solution that works with WebFOCUS to provide single-sign-on pre-authentication using the OpenID Connect standard. For more information about Keycloak and its features, see https://www.keycloak.org/about.html
For more information and instructions about how to configure an installation of WebFOCUS as a Keycloak client for OpenID Authentication, see the Keycloak Getting Started Guide, located at https://www.keycloak.org/docs/latest/getting_started/index.html
Procedure: How to Configure OpenID Connect Authentication Settings for Keycloak
Before you begin, complete the prerequisites for Pre-Authentication. For more information, see Configuring Pre-Authentication, External Authentication or External Authorization.
We recommend that you use the Export command to back up the Security Settings configuration files before making changes to the Authentication page. For more information, see How to Export Security Configuration Files.
- In the Administration Console, click the Security tab.
- Under the Security Zones folder, expand the Default Security Zone folder, and then click Authentication.
- Double-click the OpenID Connect Authentication entry to open the Edit OpenID Connect Authentication Settings dialog box.
- Type the Client ID for WebFOCUS that is identified in the Client ID field of the Settings tab of the Client page for WebFOCUS
in Keycloak.
For example: WebFOCUS-HEAD.
- Type or copy and paste the Client Secret value provided by Keycloak. Typically this is a hexadecimal representation of a randomly-generated
value.
For example:
43b89579-ea9c-4101-b321-56b9dc6ae0f8
- In the User Authorization URI field, type:
http://host:port/auth/realms/realm-name/protocol/openid-connect/auth
where:
- host
-
Is the name or IP address of the host used by Keycloak.
- port
-
Is the number of the port on which the Keycloak identity provider listens.
This value is optional, and it should be excluded if the URL uses the default port for the protocol it uses in the scheme, which is port 80 for URLs using the http protocol or port 443 for URLs using the https protocol.
- realm-name
-
Is the name of the realm you identified for WebFOCUS in Keycloak. For example, WebFOCUSRealm.
For example:
http://server01.ibi.com:8080/auth/realms/WebFOCUSRealm/protocol/openid-connect/auth
- In the Access Token URI field, type:
http://host:port/auth/realms/realm-name/protocol/openid-connect/tokenWhere host, port, and realm-name identify the host used by Keycloak as described in step 6.
For example:
http://server01.ibi.com:8080/auth/realms/WebFOCUSRealm/protocol/openid-connect/token
- In the User Info URI field, type:
http://host:port/auth/realms/realm-name/protocol/openid-connect/userinfo
Where host, port, and realm-name identify the host used by Keycloak as described in step 6.
For example:
http://server01.ibi.com:8080/auth/realms/WebFOCUSRealm/protocol/openid-connect/userinfo
- In the Logout URI field, type:
http://host:port/auth/realms/realm-name/protocol/openid-connect/logout?redirect_uri=https://wfhost.ibi.com/context/service/wf_security_logout.jsp
Where host, port, and realm-name identify the host used by Keycloak as described in step 6, wfhost identifies the name or IP address of the host used by WebFOCUS, and context identifies the context used for your installation of WebFOCUS, typically, \ibi_apps.
For example:
http://server01.ibi.com:8080/auth/realms/WebFOCUSRealm/protocol/openid-connect/logout?redirect_uri=https://wfserver01.ibi.com/ibi_apps/service/ wf_security_logout.jsp
- Type a valid attribute name in the Attribute Name for User ID field.
Note: You will most likely replace the default value, name, with the value, email. However, other attribute names can be used in this field. For more information about the value to use, consult your identity provider.
- If you must ensure that any user ID submitted to the identity provider excludes a domain name prefix, select the Strip the Domain Name from User ID check box. Otherwise, leave this check box clear.
Note: This check box is relevant only to customers who use the domain name\user ID format for their user names and work with an OpenID Connect identity provider that does not accept user IDs with a domain name prefix.
- Accept the default value, email, displayed in the Optional Scope Values field.
- Accept the default selection, HTTP POST, displayed in the Client Authentication Method list.
- When your configuration is complete, click OK.
- Enable the new configuration as described in How to Enable OpenID Connect Authentication in a Security Zone.
- Save the new configuration as described in How to Save an OpenID Connect Configuration.
Configuring Pre-Authentication With Other OpenID Connect Identity Providers
|
How to: |
Other third-party OpenID Connect providers can pre-authenticate users for WebFOCUS. Even though the information that must be configured in WebFOCUS and at the identity provider must conform to the OpenID Connect standard, the specific configuration requirements for individual identity providers can vary. For more information, see documentation from your OpenID identity provider.
Procedure: How to Configure OpenID Connect Authentication Settings for Other OpenID Connect Identity Providers
Before you begin, complete the prerequisites for Pre-Authentication. For more information, see Configuring Pre-Authentication, External Authentication or External Authorization.
We recommend that you use the Export command to back up the Security Settings configuration files before making changes to the Authentication page. For more information, see How to Export Security Configuration Files.
- In the Administration Console, click the Security tab.
- Under the Security Zones folder, expand the Default Security Zone folder, and then click Authentication.
- Double-click the OpenID Connect Authentication entry to open the Edit OpenID Connect Authentication Settings dialog box.
- If your OpenID Connect identity provider assigned you a Client ID, copy and paste that value in the Client ID field.
Or
If you assigned a Client ID to your configuration within the OpenID Connect identity provider, type or copy and paste the value in the Client ID field.
- Copy and paste the Client Secret value provided by the identity provider in the Client Secret field.
- Type or copy and paste the following URLs in the fields listed below. All of these values must be provided to you by the identity
provider.
- User Authorization URI. The URL for the http endpoint where the identity provider conducts end user authentication.
- Access Token URI. The URL for the http endpoint where the identity provider issues access tokens.
- User Info URI. The URL for the http endpoint where the identity provider maintains user information. Requests from the client application for additional information about the current user that also include a valid access token are directed to this endpoint.
- Logout URI. The URL for the http endpoint to which users must be directed when they choose to sign out of their session.
- Type a valid attribute name in the Attribute Name for User ID field.
Note: You will most likely replace the default value, name, with the value, email. However, other attribute names can be used in this field. For more information about the value to use, consult your identity provider.
- If you must ensure that any user ID submitted to the identity provider excludes a domain name prefix, select the Strip the Domain Name from User ID check box. Otherwise, leave this check box clear.
Note: This check box is relevant only to customers who use the domain name\user ID format for their user names and work with an OpenID Connect identity provider that does not accept user IDs with a domain name prefix.
- Enter the names of the optional scope identifiers that you and your identity provider have agreed to use in the Optional Scope
Values field. Separate each value with a single space.
Note: You can clear the value email that appears in this field, by default, if you and your identity provider do not support it.
- Accept the default selection of HTTP POST in the Client Authentication Method list or select HTTP Basic Authentication Scheme to identify the HTTP communication method required by your identity provider for end user authentication messages.
Note: We do not recommend that you select None unless required to do so by your identity provider.
- When your configuration is complete, click OK.
- Enable the new configuration as described in How to Enable OpenID Connect Authentication in a Security Zone.
- Save the new configuration as described in How to Save an OpenID Connect Configuration.
Procedure: How to Enable OpenID Connect Authentication in a Security Zone
Only one OpenID Connect provider can be supported per installation.
When OpenID Connect Authentication is enabled in a security zone, all other methods of authentication in that zone must be disabled.
As with other methods of pre-authentication, we recommend using this method in the Default Security Zone while allowing the Alternate Zone to support Form-Based Authentication for administration activities.
- In the Administration Console, on the Security tab, under the Security Zones folder, expand the Default Security Zone folder, and then click Authentication.
- On the Authentication page:
- Click the Form Based Authentication entry and then click Disable.
- Click the Anonymous Authentication entry and then click Disable.
- Click the OpenID Connect Authentication entry and then click Enable.
- Save the Authentication page with the OpenID Connect configuration as described in How to Save an OpenID Connect Configuration.
Procedure: How to Save an OpenID Connect Configuration
- In the Actions section of the Authentication page, click Save.
- When you receive a confirmation message, click OK.
- When you receive a message advising you to reload the web application, click OK.
- Sign out of your current session.
- Stop and restart the WebFOCUS Server.
- Sign in using a valid ID from your OpenID Connect identity provider to test the new configuration.