Special Considerations When Using User Profile Attributes for Authorization
To authorize users based on groups, roles, or user profile attribute values retrieved from an LDAP directory or Microsoft Active Directory, configure an LDAP security provider on the WebFOCUS Server. The WebFOCUS Server then retrieves information about users, groups, roles, or user profile attributes from the external user directory and passes it on to the WebFOCUS Client. This LDAP security provider can also be used to authenticate user credentials for the WebFOCUS Client.
Typically, LDAP and AD user directories maintain group membership information, which is made available to other applications to authorize users. However, some organizations rely on other information stored in the directory, such as roles or user profile attributes, to populate the attribute with the necessary authorization information. These attributes may be single-valued or multi-valued and are not required to have any relationship to other objects in the external directory. Each of these methods of authorization is supported.
Note: Depending on the vendor and version, the LDAP directory may require a user membership plug-in to support the full set of external authorization features in WebFOCUS. Active Directory supports user membership natively. For more information, contact your LDAP administrator.
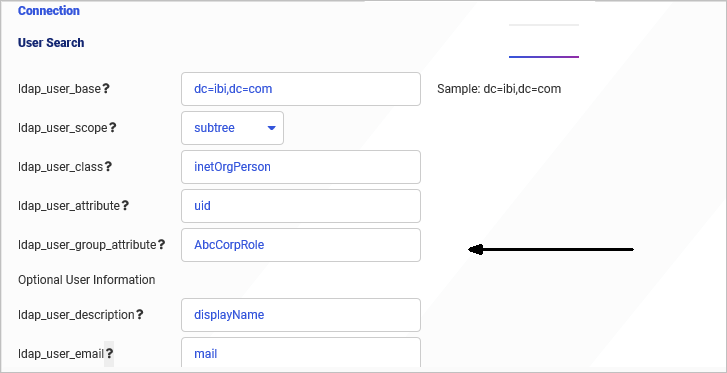
The LDAP provider can be configured to retrieve the authorization data from a user profile attribute and pass it back to WebFOCUS for authorization, as shown in the following image, where the ldap_user_group_attribute AbcCorpRole is used to authorize users.
-
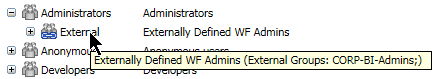
The WebFOCUS Security Center will not show which users belong to WebFOCUS groups mapped to custom attributes.
-
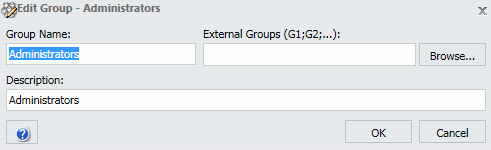
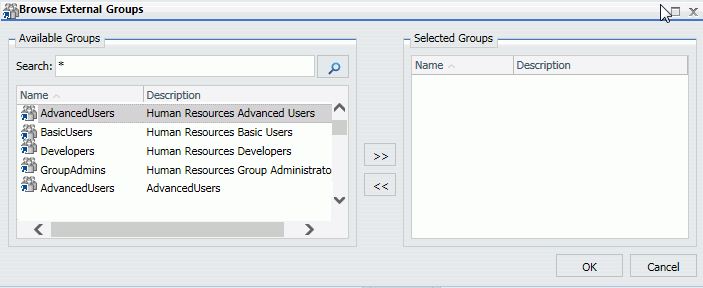
In the Security Center, the Browse button in the Edit Group dialog box does not allow you to search for custom attribute values. However, you can manually enter the attribute values.