Changing the Security Provider Configuration
|
How to: |
A Server security provider can be assigned a primary, secondary, or inactive status. Only one security provider can be identified as a primary security provider. All other active security providers are identified as secondary. Any other security providers that are configured but not in use are inactive. When you do not specify a security provider for a user account, it is treated as an account from the primary provider.
When you change the status of the primary security provider, one of the other secondary security providers must be identified as the new primary security provider. If you do not select a new security provider to replace the existing primary provider the WebFOCUS Server identifies a new primary security provider automatically.
When changing security providers, we recommend that you always retain PTH<Internal> as a secondary security provider. This practice ensures that administrators can obtain access to the WebFOCUS Server, even if the primary security provider becomes unavailable.
We also recommend that you maintain a backup copy of the current version of the admin.cfg file, located in drive:\ibi\profiles\. This file contains PTH user information. You can use the backup copy to restore the PTH security provider if the main admin.cfg file becomes corrupted.
Procedure: How to Register a User Account as a Server Administrator
WebFOCUS registers a Server Administrator account for the PTH (Internal) security provider during installation. You may wish to register additional users or groups as Server Administrators, either for those providers or for other providers you add later.
At least one of the active security providers in your configuration must have a registered Server Administrator account. However, you can designate any security provider to be the primary security provider even if no Server Administrator account is registered to it.
- Open the Access Control page of the Server browser interface. If prompted, sign in with a valid Server Administrator User ID, Password. and select a Security Provider, if the Security Provider list appears on the Sign in page.
- On the Access Control page, select Register and Register
User to open the User Registration tab, as shown in the
following image.
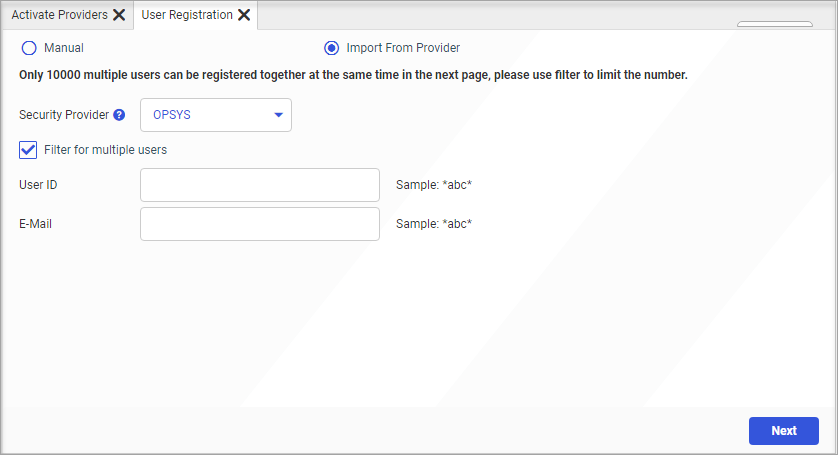
- Select Manual to open the manual version of the User Registration tab, as shown in the following
image.
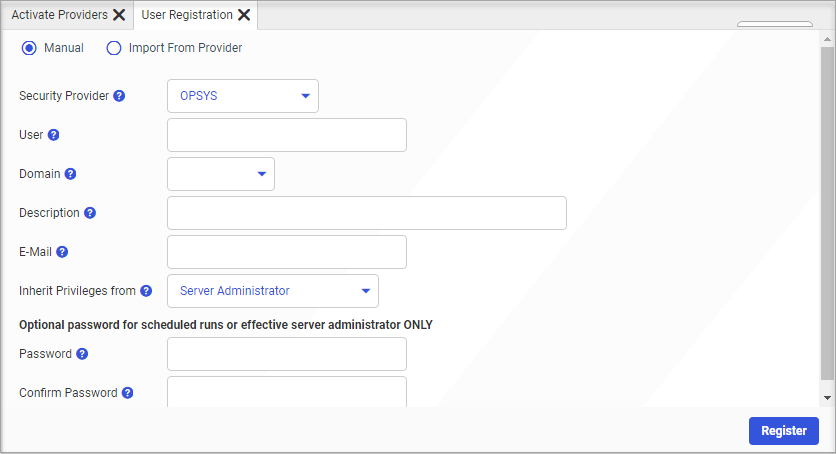
- Select the Security Provider to which the new Server Administrator will be assigned.
The page refreshes to conform to the layout for your selected provider. This layout is the same for each provider with a few minor variations as noted in the following steps.
- Enter the User ID of the new Server Administrator.
Note: Use the domain name\user ID format if required.
- If you selected the OPSYS Security Provider, select a Domain name for the user.
- Enter an optional Description for the Server Administrator if you wish.
- Enter the email address where notifications for this user are to be delivered.
- Accept the default value of Server Administrator in the Inherit Privileges from list.
Select a different Server Role only if required to do so. For more information about Server Roles, see the Server Administration technical content.
- If you selected the PTH<Internal> security provider, enter a password for this administrator in the Password and Confirm Password
fields. If you selected a different security provider, this password is optional.
Note: The WebFOCUS Server uses this password when conducting scheduled report distribution runs.
- When your configuration is complete, select Add and Register, in the PTH<Internal> Security Provider version of the dialog box, or select Register, in any other version.
- When you receive a message saying the New User will be added, select OK.
- After the User Registration page refreshes, confirm that the ID and additional information of the newly-registered user appears on the page.
Procedure: How to Configure a New Primary Security Provider
Before you begin: Ensure that you have created a security administrator for the new primary security provider as described in How to Register a User Account as a Server Administrator. You will be unable to access the Reporting Server browser interface after designating a new primary security provider if you do not have an administrator for it.
- Open the Access Control page of the Server browser interface. If prompted, sign in with a valid Server Administrator User ID, Password, and Security Provider, if the Security Provider list appears on the Sign in page.
- Identify the entry for the new primary security provider, select Primary in the Status list, as shown in the following image.
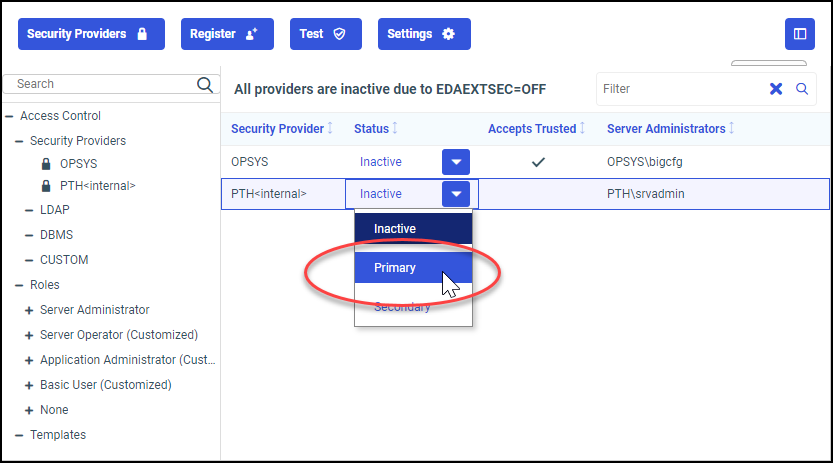
If you previously selected a Primary security provider, the status of that provider automatically changes to Secondary.
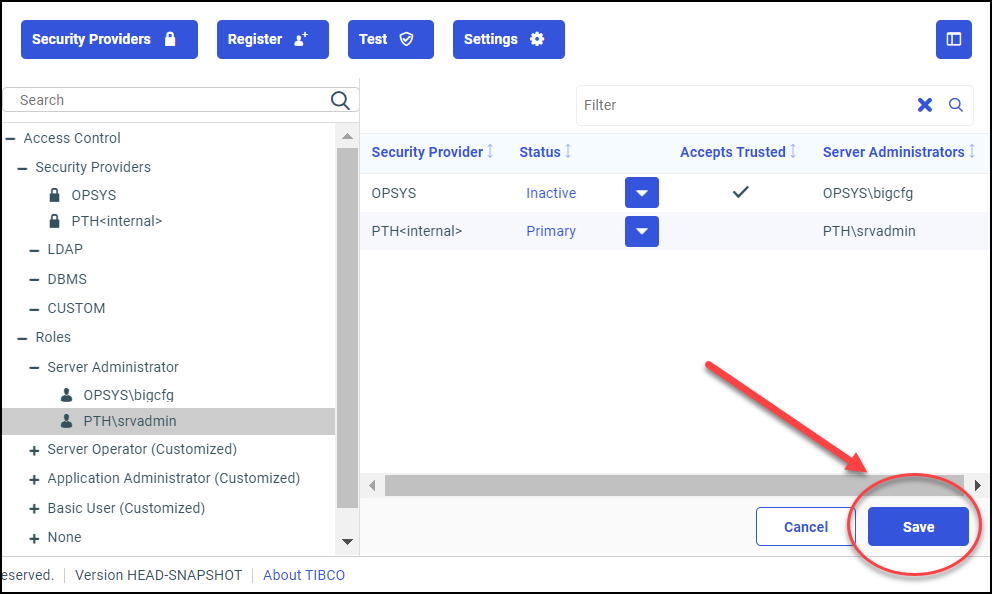
- Review your revised configuration, and select Save, as shown in the following image.
- Review the confirmation page, and select Apply
and Restart Server, as shown in the following image.

The WebFOCUS Server displays a message notifying you that it is restarting.
Note:- The WebFOCUS Server must always be restarted manually when you make OPSYS the primary provider.
- If the browser displays the Workspace restarting message for more than 30 seconds, close and re-open the browser. You should now be able to sign in to the Server browser interface.
- If the new primary provider did not identify a Server Administrator, the WebFOCUS Server notifies you that it is adding a new provider and asks you to register a Server Administrator for the provider. You can register the new Server Administrator as described in How to Register a User Account as a Server Administrator.
- After the WebFOCUS Server restarts, sign in with the user ID and password of the Server Administrator of the new primary security provider. The Applications page opens in response.
- Perform one of the following steps to navigate to the Access Control page.
- If you are on the Hub, refresh the browser to redisplay the Access Control Page.
- If you are in the Server browser interface, select Tools and Access Control to return to the Access Control page.
- In the list of Security Providers on the Access Control page, confirm that the new status appears next to the Security Provider
name, as shown in the following image.
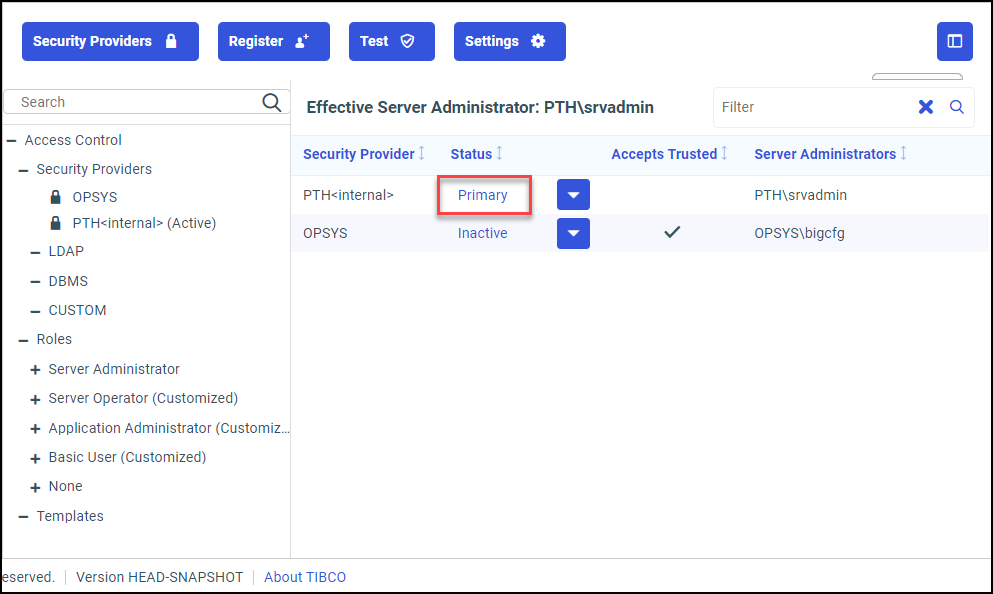
Procedure: How to Change the Status of a Security Provider
Before you begin: Ensure that you have created a security administrator for the new primary security provider as described in How to Register a User Account as a Server Administrator. You will be unable to access the Reporting Server browser interface after designating a new primary security provider if you do not have an administrator for it.
Only one Security Provider can be identified as the Primary Security Provider within the WebFOCUS Server configuration. Therefore, when you replace an existing primary security provider with a different security provider, the existing primary security provider automatically becomes a secondary security provider.
When changing security providers, we recommend that you always retain PTH<internal> as a secondary security provider. This practice ensures that you can continue to access the WebFOCUS Server, even if the primary security provider becomes unavailable.
- Navigate to the Access Control page of the Server browser interface. If prompted, sign in with a valid Server Administrator User ID, Password. and select a Security Provider, if the Security Provider list appears on the Sign in page.
- For each security provider you want to change, perform one of the following steps:
- Select Primary to activate the provider as the primary security provider.
Note: If another security provider is already identified as the primary security provider, the status of that security provider automatically changes to Secondary.
- Select Secondary to activate the provider as an alternative security provider.
- Select Inactive to deactivate the provider.
The tab refreshes after each selection.
- Select Primary to activate the provider as the primary security provider.
- When the tab refreshes, click Save.
- Review the confirmation message prompting you to confirm that the designated security administrator ID is valid within your
newly chosen Primary Security provider, and select Apply
and Restart Server.
Note: If you have activated the OPSYS security provider but have not yet identified a Server Administrator for OPSYS, you receive a message prompting you to register a Server Administrator for the OPSYS security provider, follow the steps described in How to Register a User Account as a Server Administrator.
If you do not receive this message, continue with the following step.
The WebFOCUS Server displays a message notifying you that it is restarting.
- When you receive a message that the WebFOCUS Server is restarting, wait until the WebFOCUS Server has started again.Notes:
- The WebFOCUS Server must always be restarted manually when you make OPSYS the primary provider.
- If the browser displays the Workspace restarting message for more than 30 seconds, close and re-open the browser. You should now be able to sign in to the Server browser interface.
- If prompted, sign in to the WebFOCUS Server again with a valid Server Administrator User ID, Password, and Security Provider.
- On the Home Page of the Server browser interface, select Tools and Access Control to open the Access Control page.
- In the list of Security Providers on the Access Control page, confirm that the new status appears next to the updated Security Provider names.