Add Authenticator
To synchronize the TIBCO MFT Command Center database through LDAP, you must configure an LDAP authenticator. You can add an authenticator to the TIBCO MFT Command Center system through the Add Authenticator page which can be accessed by clicking .
To add an authenticator to the system, configure the required parameters and click Add. Then you can test the authenticator to verify that your configurations will connect successfully and pull the correct users into the database through the Manage Authenticators page (see Manage Authenticators for more details).
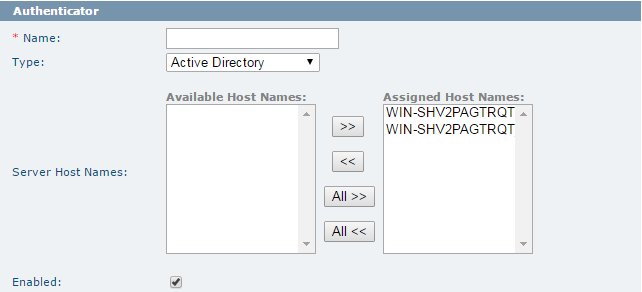
Authenticator
This section defines the authenticator attributes.
The following figure shows the Authenticator section:
The following table lists the parameters in this section:
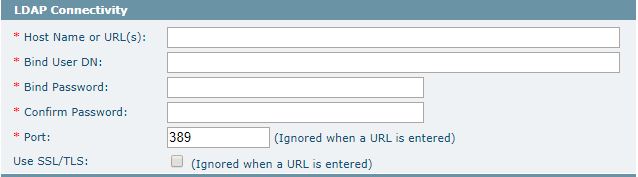
LDAP Connectivity
This section defines the parameters necessary to connect to the directory server and pull in the user and role information for synchronization.
The following figure shows the LDAP Connectivity section:
The following table lists the parameters in this section:
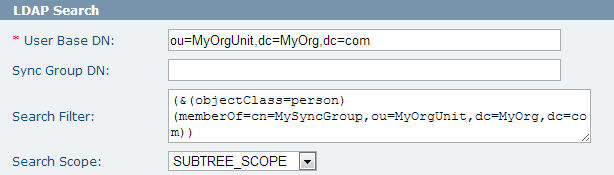
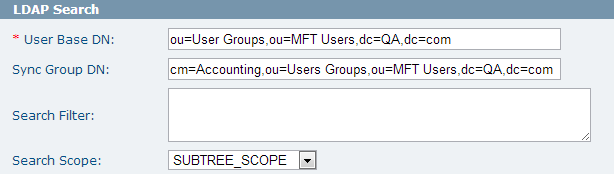
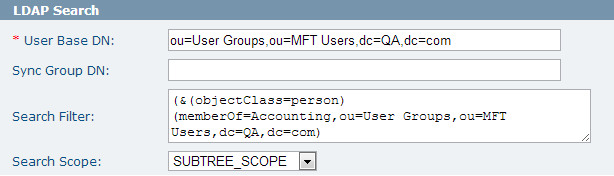
LDAP Search
This section defines the location of the sync group and the users to be synchronized into the MFT database.
The following figure shows the LDAP Search section:
Both the Sync Group DN and Search Filter fields determines which LDAP users can use MFT. Search filter is more efficient because it is applied to the LDAP search directly. The Sync Group DN parameter is less efficient because MFT needs to retrieve and examine each LDAP user in the group until it finds a match or exhausts the list. When search filter can be used to filter out LDAP users, leave the Sync Group DN field empty. The search filter can be any valid LDAP filter that defines the MFT users. Typically a search filter contains references to one or more groups that contain MFT users. The following search filter returns all users that match the following criteria:
objectClass=Person
member of group MFTGroup
(&(objectClass=person)(memberOf=cn=MFTGroup,ou=MyOrgUnit,dc=MyOrg,dc=com))
The following examples demonstrate different configurations you can set up to search for LDAP users (see the figures in Authenticators for reference).
Example 1:
In the following example, 10 active directory users are added to the MFT database (see the first figure in Authenticators for reference. Users are in orange boxes):
Example 2:
In the following example, 2 active directory users are added to the MFT database (see the first figure in Authenticators for reference. The Accounting Properties page displays the two users in the Accounting group):
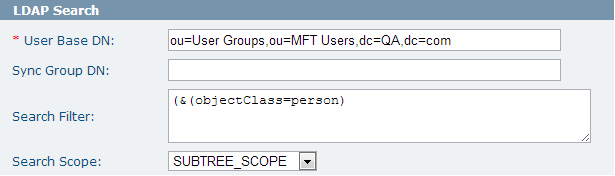
Example 3:
The following example shows how to use search filter to performing the same operation as example 2 (see the first figure in Authenticators for reference. The Accounting Properties page displays the two users in the Accounting group):
- Filter to synchronize multiple security groups in a single authenticator
(|(&(objectClass=user)(memberOf=cn=Accounting,ou=User Groups,ou=MFT
Users,dc=QA,dc=com))(&(objectClass=user)(memberOf=cn=Finance,ou=User
Groups,ou=MFT Users,dc=QA,dc=com)))
- Filter to synchronize all users with mail accounts
(&(objectclass=user)(mail=*))
The following table lists the parameters in this section:
| Parameter | Description |
|---|---|
| User Base DN | Defines the base in the directory tree where users are defined.
The levels searched below this base depend on the Search Scope parameter |
| Sync Group DN | Defines the fully qualified name of the container on the directory server to be used to associate the users with MFT.
Only users who are inside this container are synchronized with the database. |
| Search Filter |
With the LDAP search filter, you can be more selective of the user objects returned during an LDAP search. The search filter can be used instead of or in addition to the Sync Group DN parameter. Synchronizing unnecessary LDAP objects with the MFT server can be avoided when using an appropriate search filter. For example, to synchronize all users from the active directory with mail accounts, the filter string should be as follows: (&(objectclass=user)(mail=*)) If you do not want to use a specified filter to search for users, you can change the value to (objectClass=user). Contact your directory server administrator for more details on constructing LDAP search filters. |
| Search Scope | The directory levels below the base DN that LDAP will search.
The valid values are as follows: SUBTREE_SCOPE: defines that all levels below the defined User Base DN parameter will be searched. This is the default value and should be used by most users. ONELEVEL_SCOPE: defines that only the level defined by the User Base DN parameter will be searched. OBJECT_SCOPE: defines that only the object defined by the User Base DN and Search Filter parameters will be searched. |
LDAP Attributes
This section contains the fields that LDAP reads from the directory datastore server to pull in the correct information.
The predefined values in this section should be confirmed with the directory server administrator. In most cases, no changes are necessary.
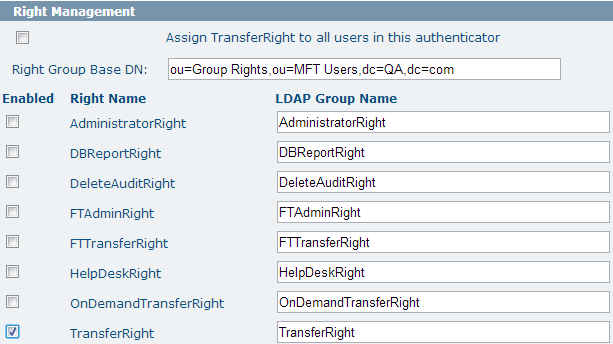
Right Management
In this section, you can enable the rights you want to be managed using the LDAP server.
TIBCO MFT Command Center or TIBCO MFT Internet Server users can be assigned with various rights. The most popular of these rights is TransferRight; without this right being assigned, users cannot perform file transfers. When the Assign TransferRight to all users check box in this authenticator is selected, all users in this authenticator are assigned with TransferRight when they are synchronized. When this check box is selected, you should not select the TransferRight check box to enable the synchronization of TransferRight. Some LDAP environments might want to control which users are assigned with this right and other rights from the LDAP server. When the right is enabled for management through the LDAP server, it cannot be granted or ungranted from TIBCO MFT Command Center or TIBCO MFT Internet Server. A group with the name defined in the LDAP Group Name field must exist on the directory server and the users assigned with this right must be members of the group.
In the following example, any users added from the TransferRight group of the active directory are given FileXpress TransferRight when they are added to the database (see the second figure in Authenticators for reference. Users are pulled from the TransferRight group):
The following table lists the parameters in this section:
| Parameter | Description |
|---|---|
| Right Group Base DN | Defines the location in the directory tree of the OU which contains the MFT rights. |
| Enable | When this check box is selected, that right will be managed on the defined LDAP server. |
| Right Name | Defines the right as it is recognized by MFT. |
| LDAP Group Name | Defines the name of the group on the LDAP server which will be associated with the right in MFT.
This can be the same as the Right Name parameter or be specified as a different group name. The value of the LDAP Group Name field should match the group name on the directory server. |