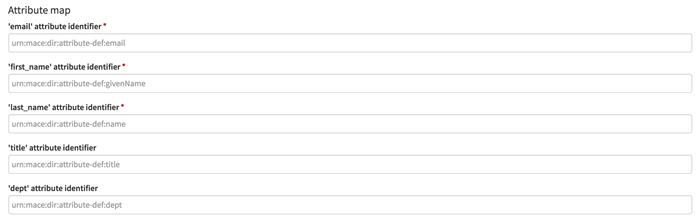
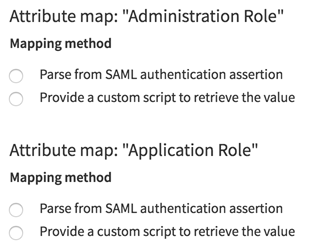
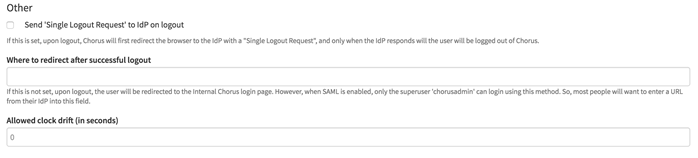
Enabling Single Sign-On - SAML and Configuring SSO Options
You can now use single sign-on with Team Studio to streamline your user provisioning and security.
Note: SAML authentication has been tested with specific configurations of Shibboleth. While SAML is a standard, there is a great deal of variability in configuration between different IDP products, so it is possible that other IDP implementations, or other configurations of Shibboleth, might not interoperate correctly with
Team Studio.
Prerequisites
server_url = http://mytsdsinstallation.mydomain.com:8080
Procedure
What to do next
If you have trouble with your SAML configuration and need to return to the administration panel, you can skip authentication by appending /?skip_saml=true to your Team Studio URL. (For example, http://mytsdsinstallation.mydomain.com/?skip_saml=true.)
For information about configuring the IDP, see Configuring the IDP.
- Configuring the IDP
After you enable single sign-on in Team Studio, when you visit the Team Studio URL and are not logged in, it attempts to redirect to the IDP login page instead of showing the normal Team Studio login page.
Related concepts
Related tasks
Copyright © Cloud Software Group, Inc. All rights reserved.