TIBCO WebFOCUS Server Settings
|
In this section: |
|
Reference: |
To open the TIBCO WebFOCUS Server Settings, click the Configuration tab and expand the Reporting Servers folder. You can:
- Configure basic Client settings for communicating with the Server.
- Create or modify an alternate server mapping.
- Create or modify a Cluster Manager for monitoring server performance statistics and sending requests to the best available server for processing.
- Manage legacy cluster configurations.
Reference: Server Node Properties
The Server Node properties defined in the Basic pane are explained below.
Basic
- Node Name
-
The name cannot be the same as any other node name, and it cannot contain more than forty-eight (48) characters. When the client accesses this server, it will use this name.
- Node Description
-
Optional. The description of the node that appears in the Configuration pane. If this is omitted, the node name will be used.
- Host
-
The Host name or IP address of the Host Server.
- TCP/IP Port
-
The Port number for the TCP listener. The default port is 8120.
- HTTP(S) Port
-
The Port number for the HTTP listener. This is typically one port after the TCP/IP port.
The default HTTP port is 8121.
- Security
-
The security options for the Server connection.
- Prompt for Credentials. The Client makes an explicit connection to the Server with the user ID and password specified in the Web Security tab. This is the default value.
- HTTP Basic. The user ID and
password are extracted from the authorization header. These credentials
are then used to make an explicit connection to the Server.
You should only select this option when your web tier is performing
Basic Authentication.
Note: You can verify that the authorization header is available by selecting HTTP Request Info in the Diagnostics tab.
- Kerberos. The Client passes a Kerberos ticket for the user to the Server, along with the user ID and group memberships assigned to that user. This option enables an end-to-end single sign on solution from the desktop to the Client, from the Client to the Server, and from the Server to supported relational DBMS systems. To use Kerberos authentication, the Server must run in security OPSYS mode.
- SAP Ticket. The Client passes the user MYSAPSSO cookie, which is created on SAP Enterprise Portal, to the Server. The Server then validates the cookie using the SAP security API. This option enables single sign on from the Client to a Server configured with the Data Adapter for SAP for environments using Open Portal Services in SAP Enterprise Portal.
- Service Account. Allows you to specify
a user ID and password to be used for all connections to the Server.
The service account credentials are encrypted and stored in the SECURITY keyword of the odin.cfg file. When defined, the service account overrides any other credentials that may be presented for this Server node, and all users connect to the Server using the same credentials. This approach does not make it possible to identify which user is running a given request on the Server in Managed Reporting deployments, and therefore is not recommended for them.
- Trusted. Allows non-authentication requests to connect
to the Server as trusted. After a user is authenticated
through a pre-authentication mechanism or a Sign in page,
all subsequent requests to the Server are trusted.
To use this option, the Server Security Provider must also be configured to allow trusted connections, and controls should be placed on the Server to ensure that it rejects connections from unauthorized clients. For example, you should employ the Server RESTRICT_TO_IP setting or configure a network firewall so that only your specified clients can connect to the Server.
When you create a new Client Configuration, the Trusted option is selected, by default, and the Pass TIBCO WebFOCUS User ID and their Groups and Custom options appear below it. When you accept the default option, Pass TIBCO WebFOCUS User ID and their Groups, the Client passes the ID and group memberships assigned to the user to WebFOCUS Server. When you select the Custom option, the display refreshes to show the User ID and the User's Groups check boxes allowing you to customize the user information passed to the server. The options TIBCO WebFOCUS script variable and HTTP Header Field appear under both check boxes, as shown in the following image.
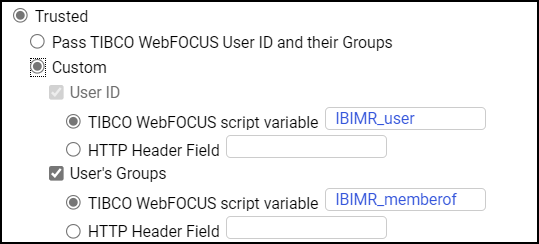
Under the User ID check box, the TIBCO WebFOCUS script variable option displays the IBIMR_user parameter, by default. Under the User's Groups check box, the TIBCO WebFOCUS script variable option displays the IBIMR_memberof parameter, by default. You can type over the default values in the TIBCO WebFOCUS script variable options, and type your own values in the HTTP Header Field options.
Note: When configuring the Client to make trusted connections to the Server, you must also enable the Server to accept trusted connections.
Advanced
The Server Node properties from the Advanced pane are explained below.
- Service Name
-
Contains a description for the Server node. This description displays to end users.
- Use HTTPS
-
Enables encrypted communication between the Client and the Server HTTP listener. The default value is off (check box cleared).
This option must be selected if the Server HTTP listener is configured to use SSL. If you are using a self-signed certificate to enable HTTPS communication with a Server, the certificate must be configured in the Java environment where the Client is installed. This enables HTTPS communication between the Server and the Administration Console.
- TLS
-
Enables data encryption when transmitting data over the internet to ensure data privacy. The default value is off (check box cleared).
When selected, the Compression and Encryption options are hidden because TLS encrypts and compresses the data, by default.
- Compression
-
Enables data compression. By default, data compression is disabled.
- Encryption
-
Sets data encryption ability and the symmetric cryptography method used.
Select one of the following options from the drop-down list:
- 0. Off. This is the default value.
- AES. Advanced Encryption Standard. The AES selections
are in the format
CIPHER(x)(-MODE)
where:
- CIPHER
-
Is AES128, AES192, AES256.
- x
-
Is optional and defines an RSA key length of 1024 bits. When this is not specified, the RSA key is 512 bits.
- CBC
-
Is optional and defines the use of Cipher Block Chaining (CBC) mode. When the mode is not specified, Electronic Code Book (ECB) is used.
For example, AES256x-CBC is the AES256 cipher with a 1024-bit RSA key in CBC mode. AES128 is the AES128 cipher with a 512-bit RSA key in ECB mode.
- Connect Limit
-
Specifies the number of seconds that the Client will hold the pending connection. Other possible values are 0 (no wait) and -1 (infinite wait). The default value is -1.
- Maximum Wait
-
Specifies the time, in seconds, that the Client will wait before timeout. You can optionally specify different return times for the first row and other rows. A single number indicates that the return time is valid for any row. If two numbers are separated by a comma, the first number specifies the return time for the first row and the second number specifies the return time for the subsequent rows. The default value is -1, which indicates an infinite wait time.
- Security Object
-
For any security option, an administrator can specify one or more HTTP header names and/or cookie names as follows:
- Cookie. Specify each
HTTP cookie name separated by a comma (,). For example:
cookie_name1, cookie_name2
- Header. Specify each HTTP header name separated by a
comma (,). For example:
header_name1, header_name2
Note:
- HTTP cookie and header names must not contain commas (,) or colons (:). These are reserved delimiters.
- REMOTE_USER is a special type of HTTP header variable whose contents will not be sent to the Server. Therefore, it is not a valid HTTP header value. Instead, specify the WF_REMOTE_USER variable.
- Cookie. Specify each
HTTP cookie name separated by a comma (,). For example:
Basic Cluster Manager Configuration Properties
- Node Name
-
Is the host name or IP address of the server.
- Node Description
-
Optional. The description of the node that appears in the Configuration pane. If this is omitted, the node name will be used.
- Remote CLM Host
-
Is the Host name or IP address of the Cluster Manager on which a remote Cluster Manager (CLM) is listening. If more than one address is specified, one of the addresses will be randomly selected until a successful connection to the CLM happens. The number of IP addresses defined in this setting must be the same as the number of port numbers defined in Remote CLM Port. Separate multiple host names or IP addresses with a comma.
- Remote CLM Port
-
Is the UDP number of the Port on which the Cluster Manger server is listening. The default port is 8200. If more than one port number is specified, the number of port numbers must be the same as the number of IP addresses defined in Remote CLM Host. Separate multiple host names or IP addresses with a comma.
- Security
-
The security options for the Server cluster.
- Prompt for Credentials. The Client makes an explicit connection to the Cluster Manager with the user ID and password specified in the Web Security tab. This is the default value.
- HTTP Basic. The user ID and
password are extracted from the authorization header. These credentials
are then used to make an explicit connection to the Cluster Manager.
You should only select this option when your web tier is performing
Basic Authentication.
Note: You can verify that the authorization header is available in by selecting HTTP Request Info in the Diagnostics tab.
- Kerberos. The Client passes a Kerberos ticket for the user to the Cluster Manager, along with the user ID and group memberships assigned to that user. This option enables an end-to-end single sign on solution from the desktop to the Client, from the Client to the Cluster Manager, and from the Cluster Manager to supported relational DBMS systems. To use Kerberos authentication, the Cluster Manager must run in security OPSYS mode.
- SAP Ticket. The Client passes the user MYSAPSSO cookie, which is created on SAP Enterprise Portal, to the Cluster Manager. The Cluster Manager then validates the cookie using the SAP security API. This option enables single sign on from the Client to a Cluster Manager configured with the Data Adapter for SAP for environments using Open Portal Services in SAP Enterprise Portal.
- Service Account. Allows you to specify
a user ID and password to be used for all connections to the Cluster
Manager.
The service account credentials are encrypted and stored in the SECURITY keyword of the odin.cfg file. When defined, the service account overrides any other credentials that may be presented for this Cluster Manager node, and all users connect to the Cluster Manager using the same credentials. This approach does not make it possible to identify which user is running a given request on the Cluster Manager in Managed Reporting deployments, and therefore is not recommended for them.
- Trusted. Allows you to connect to the Cluster Manager
with only a user ID. This option is useful when no password is available
for the user. Controls should be placed on the Cluster Manager
to ensure that connections from unauthorized clients are rejected.
For example, you can employ the Cluster Manager RESTRICT_TO_IP setting
or configure a network firewall so that only a particular client
can connect to the Cluster Manager.
When you create a new Cluster Manager Configuration, the Trusted option is selected, by default, and the Pass TIBCO WebFOCUS User ID and their Groups, and Custom options appear below it.
When you accept the default option, Pass TIBCO WebFOCUS User ID and their Groups, the Client passes the ID and group memberships assigned to the user to the WebFOCUS Server. When you select the Custom option, additional settings appear and you can customize the user information sent from the Client to the WebFOCUS Server.
Note: When configuring the Client to make trusted connections to the Server, you must also enable the Cluster Manager to accept trusted connections.
Advanced Cluster Manager Configuration Properties
- Use HTTPS
-
Enables encrypted communication between the Client and the HTTP listener.
The default value is off.
This option must be selected if the Cluster Manager HTTP listener is configured to use SSL. If you are using a self-signed certificate to enable HTTPS communication with a Cluster Manager , the certificate must be configured in the Java environment where the WebFOCUS Client is installed. This enables HTTPS communication between the Cluster Manager and the Administration Console.
- Compression
-
Enables data compression. By default, data compression is disabled.
- Encryption
-
Sets data encryption ability and the symmetric cryptography method used.
Select one of the following options from the drop-down list:
- 0. Off. This is the default value.
- AES. Advanced Encryption Standard. The AES selections
are in the format
CIPHER(x)(-MODE)
where:
- CIPHER
-
Is AES128, AES192, AES256.
- x
-
Is optional and defines an RSA key length of 1024 bits. When this is not specified, the RSA key is 512 bits.
- CBC
-
Is optional and defines the use of Cipher Block Chaining (CBC) mode. When the mode is not specified, Electronic Code Book (ECB) is used.
For example, AES256x-CBC is the AES256 cipher with a 1024-bit RSA key in CBC mode. AES128 is the AES128 cipher with a 512-bit RSA key in ECB mode.
- IBCRYPT. User-defined IBCRYPT DLL is loaded.
- Connect Limit
-
Specifies the number of seconds that the Client will hold the pending connection. This is useful in a cluster deployment to avoid a lengthy delay of failover response. Other possible values are 0 (no wait) and -1 (infinite wait). The default value is -1.
- Maximum Wait
-
Specifies the time, in seconds, that the Client will wait before timeout. You can optionally specify different return times for the first row and other rows. A single number indicates the return time is valid for any row. If two numbers are separated by a comma, the first number specifies the return time for the first row and the second number specifies the return time for the subsequent rows. The default value is -1, which indicates an infinite wait time.
- Security Object
-
For any security option, an administrator can specify one or more HTTP header names or cookie names as follows:
- Cookie. Specify each HTTP cookie name separated by a
comma (,). For example:
cookie_name1, cookie_name2
- Header. Specify each HTTP header name separated by a
comma (,). For example:
header_name1, header_name2
Note:
- HTTP cookie and header names must not contain commas (,) or colons (:). These are reserved delimiters.
- REMOTE_USER is a special type of HTTP header variable whose contents will not be sent to the Server. Therefore, it is not a valid HTTP header value. Instead, specify the WF_REMOTE_USER variable.
- Cookie. Specify each HTTP cookie name separated by a
comma (,). For example:
Configuring TIBCO WebFOCUS Server Connections
Server connection nodes contain all of the information necessary for the Client to connect with and make use of a Server. A Server connection node provides access to one server. A Cluster Manager node provides access to multiple servers. Changes you make to the configuration in this section are captured in the odin.cfg file, located in drive:\ibi\WebFOCUS82\client\wfc\etc on Windows, or located in install_directory/ibi/WebFOCUS82/client/wfc/etc on UNIX or Linux.
The names of all Reporting Server Connection nodes also appear in the Multiple Servers List. This list is located in two places on the Hub. It appears above the Application Directories tree of the Application Directories area and in the Server Administration section of the Management Center area menu.
When you add a Reporting Server Connection node, the name of that node appears on the list. When you delete a Reporting Server Connection node, the name of that node disappears from the list. If you change the name of an existing Reporting Server Connection node, the new name is added, but the name of the existing node remains in the list until you delete the node it represents from the Reporting Server Connections page.
Procedure: How to Open the WebFOCUS Server Console From the WebFOCUS Administration Console
You can make global configuration changes in the server environment by using the Server Console.
- In the Administration Console, click the Configuration tab.
Expand the Reporting Servers folder and expand
the Server Connections folder.
The existing Servers are shown.
- Right-click
a Server node, and click Reporting Server Console.
If you are prompted to sign in, type the credentials of the Server Administrator.
The Server Console opens in a separate window.
For more information about the Server Console, see the Server Administration manual, or click Help.
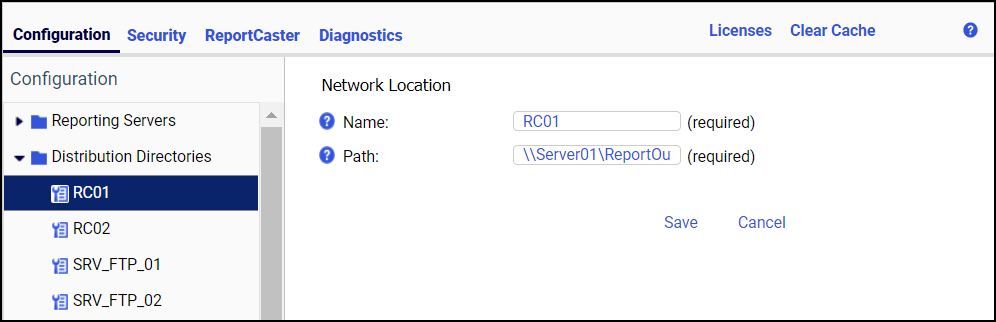
Procedure: How to Add a WebFOCUS Server Server Connection
- In the Administration Console, click the Configuration tab, and expand the Reporting Servers folder.
- Right-click the Server Connections folder
and click New.
The Client Configuration pane opens.
- In the
Client Configuration pane, type the node name, host, and TCP/IP port.
You can optionally specify a node description and HTTP(S) port.
Note: The name cannot be the same as any other node name, and it cannot contain more than forty-eight (48) characters. When the client accesses this server, it will use this name.
- Select the
type of security to use when connecting to this Server.
- If you select Prompt
for Credentials or HTTP Basic,
proceed to step 8.
Note: If you are using HTTP Basic authentication, you can verify the authorization header by selecting HTTP Request Info in the Diagnostics tab.
- If you select Kerberos or SAP Ticket,
proceed to step 8.
Note: See Configuring Kerberos for Single Sign On for additional setup requirements.
- If you select Service Account, proceed to step 5.
- If you select Trusted,
proceed to step 6.
Trusted is the default. This is the recommended approach to connect to a Server.
- If you select Prompt
for Credentials or HTTP Basic,
proceed to step 8.
- If you selected Service Account, type the Service Account ID and password, then proceed to step 8.
- If you selected Trusted,
configure the behavior of the trusted connection between the Client
and the Server:
- If you would like to pass the user ID and group information to the Server using the IBIMR_user and IBIMR_group script variables respectively, proceed to step 8. This is the default behavior.
- If you would like to pass only the user ID, or to pass the user ID and/or group information with a different variable name or using HTTP headers instead of script variables, select the Custom radio button and proceed to step 7.
- If you selected Trusted
- Custom, customize the information sent to the Server, and the script variables or HTTP headers used.
- User ID is pre-selected. Select TIBCO WebFOCUS script variable or HTTP Header field, depending on how you will pass user IDs. Accept the default script variable, IBIMR_User, or type an alternative script variable or HTTP Header field.
- If you would like to pass group information to the Server, select User's Groups, then select TIBCO WebFOCUS script variable or HTTP Header field, depending on how you will pass group information. Accept the default script variable, IBIMR_memberof, or type an alternative script variable or HTTP Header field.
For more information on using TIBCO WebFOCUS script variables and HTTP headers, see Manipulating WebFOCUSDB2 Web Query Variables. For more information on configuring trusted connections on the Server, see Configuring Trusted Connections.
- Optionally,
expand the Advanced section to customize
the properties for service name, Use HTTPS, Compression, Encryption, Connection
Limit, Maximum Wait, and Security Object. If left blank, these options
use the default properties.
Note: When configuring the Client to make trusted connections to the Server, you must also enable the Server to accept trusted connections.
For more information about the Advanced settings, see Server Node Properties.
- Click Save.
A node for the new WebFOCUS Server connection appears in the tree under the Server Connections folder. The name of the new WebFOCUS Reporting Server connection also appears in the Multiple Servers List. This list is located in two places on the Hub. It appears above the Application Directories tree of the Application Directories area and in the Server Administration section of the Management Center area menu.
Procedure: How to Modify a WebFOCUS Server Connection
- In the Administration Console, click the Configuration tab, and expand the Reporting Servers folder.
- Click the server connection you would
like to modify.
The connection properties appear in the Client Configuration pane.
- Make the desired changes and click Save.
Procedure: How to Configure Encrypted Communication with a WebFOCUS Server
This procedure assumes that you have already successfully installed and configured the WFServlet implementation.
- If you are
using Sun JVM with an encryption cipher key that is over 128 bits,
be sure to install the Java Cryptography Extension (JCE). You can
obtain the JCE from the Oracle download website.
Note: The JCE must be installed in the JVM directory that your application is using. For more information, see the JCE documentation.
- Redeploy the webfocus.war file if it is necessary to point to the .war file. Otherwise, point to the web application directory.
- In the Administration Console, expand the Reporting Servers folder, then expand the Server Connections folder.
- Select
the Server node (for example, EDASERVE) you want
to configure for encryption.
The Client Configuration pane appears.
- Click the Advanced arrow to open the Advanced section.
- Click
the encryption cipher you want to use from the Encryption list.
Note: When using any of the AES encryption ciphers, the client randomly generates a new RSA key pair (public and private keys of the specified length) and sends the public key to the server. Upon receipt of the public key, the server generates a random secret key. The length of the secret key depends on the chosen cipher strength. The secret key is encrypted with the public RSA key and sent back to the client, which decrypts it with its private RSA key. After the exchange, the client and the server both share the same secret key, and use it to encrypt and decrypt all communication between them.
- Click Save.
Procedure: How to Set a Default WebFOCUS Server Node
Selecting a default Server node in the Configuration tab sets the node as the IBI_REPORT_SERVER value in the webfocus.cfg file. However, if a site profile, universal profile, or request URL specifies a different default Server node, that value will override this selection. Profiles and request URLs use the IBIC_server setting for that purpose.
- In the Administration Console, on the Configuration tab, expand the Reporting Servers folder, and then expand the Server Connections folder.
- Right-click
a Server node, and then click Set as Default.
A green check mark appears on the server icon indicating the default node.
Procedure: How to Test a WebFOCUS Server Connection
- In the Administration Console, on the Configuration tab, expand Reporting Servers, and then expand Server Connections.
- Right-click the connection
you want to test, and point to Test.
- Select TABLE Request to test a table query on the server.
- Select GRAPH Request to test a graph query on the server.
- Select Stored Procedure to test a stored procedure on the server.
- On the test page, click Run.
- If the Valid credentials are required for reporting server page opens, enter your User ID and Password, and then click Sign in.
- Review the test results.
If you receive a Server Error message, the server connection failed.
If a page opens, displaying the results of your test, the server connection was successful.
- When your review of the results is complete, close the results page, and on the test page, click Cancel.
Reconnecting the Client to the Repository
Whenever a network, operating system, relational database system, or Application Server disruption temporarily disconnects the Client from the Repository, the Client automatically reconnects to the Repository as soon as the disruption is resolved. There is no need to stop and restart the Application Server to re-establish the connection between the Client and the Repository.
If you are able to remain signed in to a session during the disruption, you will automatically reconnect to the Repository as soon as the connection is restored. If the disruption forces you to sign out, you will automatically reconnect to the Repository when you sign in again. After the connection is restored, you can resume your work from the point at which you were interrupted.
Records of the events that disrupt and restore the connection between the Client and the Repository are captured in the System log.
Alternate Server Mapping
You can configure Alternate Server nodes for use with the Managed Reporting Deferred Receipt feature.
Deferred Receipt requests can be processed by using the immediate Server (immediate server) or by using an alternate deferred receipt server (Deferred Server) dedicated to running only deferred requests. The resources for the Deferred Server are managed independently from the immediate server. The Deferred Server must have the same access to applications, data sources, and Master Files, and run in the same environment (for example, UNIX), as the immediate server.
Note: If you use the Server for z/OS, additional configuration is required to use deferred requests. You must set up an alternate server or service to handle deferred requests and then configure the WebFOCUS Client to send requests to that server by setting up a deferred server mapping. For more information, see the Installation and Configuration for Windows manual for your platform.
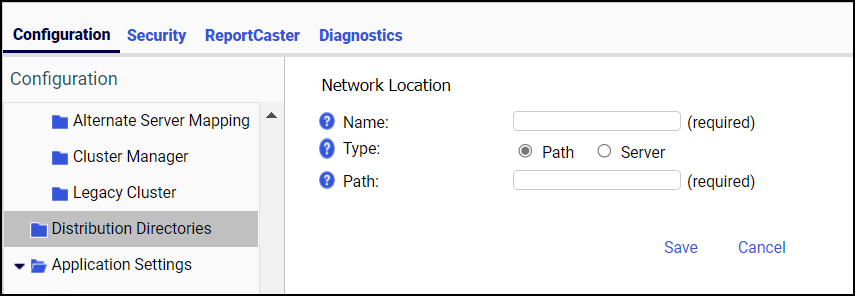
Procedure: How to Add an Alternate Server Mapping
- In the Administration Console, on the Configuration tab, expand the Reporting Servers folder.
- Right-click the Alternate Server Mapping folder and
click New.
The Alternate Server Mapping pane opens.
- Click the main server in the Server list.
- Click the alternate server from the Alternate Server list.
- Click Save.
- When you receive the Successfully Saved message, click OK.
Procedure: How to Modify an Alternate Server Mapping
- In the Administration Console, on the Configuration tab, expand the Reporting Servers folder, and then expand the Alternate Server Mapping folder.
- Click the node of the server mapping
you would like to modify.
The connection properties appear in the Client Configuration pane.
- Make the
desired changes and click Save.
Note: Changes to the main server value automatically clear the value assigned to the alternate server. Therefore, if you change the value in the main server setting, you must also select an alternate server.
- When you receive the Successfully Saved message, click OK.
Procedure: How to Map a Deferred Server Node to an Immediate Server Node
Using the Administration Console, add a node for the deferred server the same way as adding a non-deferred node. Next, perform the following steps to map the Deferred Server to an immediate Server node:
- In the Administration Console, on the Configuration tab, expand the Reporting Servers folder and right-click Alternate Server Mapping.
- Click New to
create a new mapping.
The Alternate Server Mapping page opens, allowing you to edit the altdnode.wfs file.
- Click the name of the immediate server in the Server list, which displays the list of all available Servers.
- Click the name of the deferred server in the Alternate Server list, which displays the list of all available Servers (excluding the immediate server you just specified).
- Click Save.
Note: You can map multiple immediate servers to the same deferred server by repeating these steps.
Managing Clustered Servers
Clustering allows you to automatically send requests to the best available server for processing.
The Cluster Manager (CLM) enables you to define clusters of Servers that can be brought up and down as needed. In addition, the Cluster Manager enables you to configure cluster properties, including response time and dispatch method. It then monitors cluster performance and provides statistics, such as the average response time for requests, the number of connection failures and errors, and how many requests were sent per minute.
For more information, see Server Node Properties.
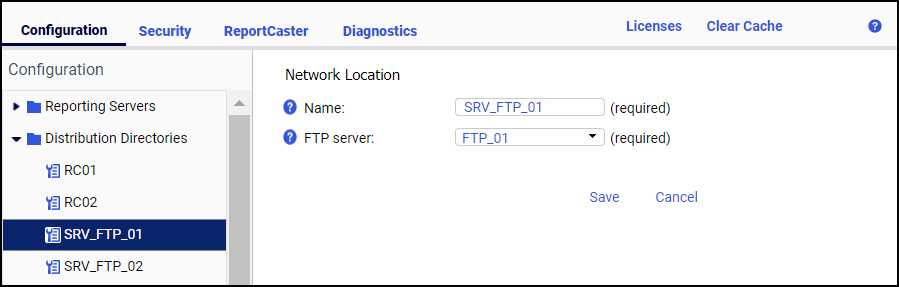
Procedure: How to Add a Cluster Manager Node
This procedure details the steps you take to create a cluster of servers in a node using the Cluster Manager.
- In the Administration Console, on the Configuration tab, expand the Reporting Servers folder.
- Right-click
the Cluster Manager folder and click New.
The Cluster Manager Configuration pane opens.
- In the Cluster
Manager Configuration pane, type the Node Name, Remote CLM host,
and Remote CLM port. You can optionally specify a Node Description.
The default Remote CLM Port is 8120.
Note: The Node Name provided in the Administration Console for Cluster Manager configurations must match the Cluster name of the Cluster Manager Server.
- Select the
type of security to use when connecting to this Cluster Manager:
- If you select Prompt for Credentials, HTTP Basic, Kerberos, or SAP Ticket, click the appropriate option and proceed to step 7.
- If you select Service Account, proceed to step 5.
- If you select Trusted, proceed to step 6.
Note:
- If you are using HTTP Basic authentication, you can verify the authorization header by selecting HTTP Request Info in the Diagnostics tab.
- If you are using Kerberos authentication, see Configuring Kerberos for Single Sign On for additional setup requirements.
- If you selected Service Account, enter a user ID and password. Proceed to step 7.
- If you selected Trusted,
by default, the client passes the user ID and group information to
the Server using the IBIMR_user and IBIMR_group script
variables. You can customize this behavior by using the different
variable names, using HTTP headers instead of script variables,
or not passing group information.
- If you would like to enable the default behavior, select Pass WebFOCUS User ID and their Groups and proceed to step 7.
- If you would like to use a TIBCO WebFOCUS script variable or HTTP header to pass user or group information, select Advanced.
- User ID is pre-selected because you will always send user information. Select TIBCO WebFOCUS script variable or HTTP Header field, depending on how you will pass user IDs. Accept the default script variable, IBIMR_User, or type an alternative script variable or HTTP Header field.
- If you would like to pass group information to the Server, select User's Groups, then select TIBCO WebFOCUS script variable or HTTP Header field, depending on how you will pass group information. Accept the default script variable, IBIMR_memberof, or type an alternative script variable or HTTP Header field.
Note: You must configure the security provider on the Server to accept trusted connections.
For more information on using TIBCO WebFOCUS script variables and HTTP headers, see Manipulating WebFOCUSDB2 Web Query Variables. For more information on configuring trusted connections on the Server, see Configuring Trusted Connections.
- If you are using the default service name, use of SSL, compression, encryption, connection limit and wait time, and are not using cookies or headers, proceed to step 8. If you would like to customize these properties, expand the Advanced arrow and configure the desired fields.
- Click Save.
Procedure: How to Modify a Cluster Manager Node
- In the Administration Console, on the Configuration tab, expand the Reporting Servers folder, and then expand the Cluster Manager folder.
- Right-click the node you want to edit
and click Edit.
The node properties appear in the Cluster Manager Configuration pane.
- Make the desired changes and click Save.
Managing Legacy Cluster Configurations
Previous implementations of Server clustering are still supported through the Legacy Cluster Configuration screen.
Procedure: How to Configure a Legacy Cluster
- In the Administration Console, on the Configuration tab, expand the Reporting Servers folder.
- Right-click the Legacy Cluster Configuration folder
and select New.
The Legacy Cluster Configuration pane opens.
- Type a Node Name and, optionally, a Node Description.
- Select the servers to include in the cluster as follows:
- Click a single server in the Available list box, and click the right arrow.
- Hold down the Ctrl key, click multiple non-adjacent servers, and click the right arrow.
- Hold down the Shift key and click on the first and last adjacent server to include all of them, and click the right arrow.
- Click Save.
Using Client Profiles
|
In this section: |
Client variables are not passed to the Server, so they cannot be included directly in any of the Server profiles (edasprof.prf, user profiles, and group profiles). However, you can make use of Client variables by specifying procedures in the site profile or universal profile. The site profile and the universal profile run after the Server profile processing, but before the report request. The site profile executes from the Client and the universal profile executes code from both the Client and the ReportCaster Distribution Server.
The site profile and the universal profile can also be added directly to webfocus.cfg or site.wfs.
The Client Site Profile
|
How to: |
A site profile is sent to the Server by the Client and is executed on the Server immediately after all Server profiles. It can override settings in the Server profiles and can take advantage of the variable values set by the other profiles. This makes the amper variables exported by the Client with the (pass) syntax available for use on the Server.
For more information on using amper variables, see Manipulating WebFOCUSDB2 Web Query Variables. For more information on Server profiles, see WebFOCUS Reporting Server Profiles.
Customers can use a site profile to:
- Make a series of data source connections dependent on a variable sent from the Client.
- Use a Client variable (for example, &REMOTE_ADDR or &IBIMR_user) in a custom security procedure on the Server, which can set other amper variables that affect subsequent report processing. This is an example of application-based security.
Note: The site profile is only processed when procedures are run by the Client. Use the universal profile to include commands to be processed when procedures are run by the ReportCaster Distribution Server.
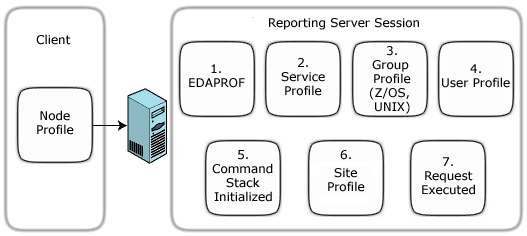
The following diagram illustrates site profile processing. The numbers associated with the files refer to the order in which the files are processed.
Procedure: How to Create a Site Profile
- In the Administration Console, on the Configuration tab, under the Application Settings folder, click Client Settings.
- Type the
name of the desired procedure in the Site Profile (IBI_SITE_PROFILE)
field.
The Site Profile (IBI_SITE_PROFILE) field uses the following syntax:
_site_profile=command
where:
- command
-
Is any valid Server syntax.
Once you have completed these steps, the profile procedure or procedures run automatically. There is no need to restart the Server.
The Universal Profile
|
How to: |
A universal profile is sent to the Server by both the Client and the ReportCaster Distribution Server and is executed on the Server. It runs immediately following all Server profiles.
Unlike the site profile, the universal profile is included during the execution of procedures by ReportCaster. Therefore, it should not include any logic or constructs that will execute only on the Client. For example, HTTP header variables should not be included, because they are available to the Client but not to the ReportCaster Distribution Server.
Procedure: How to Create a Universal Profile
- In the Administration Console, on the Configuration tab, under the Application Settings folder, click Client Settings.
- On the Client Settings page, type the
desired procedure in the Universal Profile (IBI_UNIVERSAL_PROFILE) field.
The Universal Profile (IBI_UNIVERSAL_PROFILE) parameter uses the following syntax:
IBI_UNIVERSAL_PROFILE=command
where:
- command
-
Is any valid Server syntax. The universal profile is executed by both the Client and the ReportCaster Distribution Server. This differs from the Site Profile, which is only executed by a Client request.
Once you have completed these steps, the profile procedure (or procedures) run automatically. There is no need to restart the Server.