This chapter describes how to manage TIBCO BusinessEvents® Extreme security. The TIBCO BusinessEvents® Extreme security model uses these concepts:
System users are formally known as principals.
A principal is defined with a credential (password) and they are granted one or more roles.
Principals are defined using administration commands, or optionally configuration.
A user who installs a node is automatically granted administrative access to the node. This user has full administrative control of the installed node when logged in from the same host on which the node was installed. It is also possible to specify a different user at node installation. That user is also granted full administrative access to the installed node. See the section called “Default Node Security” for details.
Apart from the user that installed the node, other users may administer the node only if they are granted the administrative role. See the section called “Roles” for complete details on the default security roles.
All access to a node is controlled by a username and password that is defined for a principal. This is true for all supported administrative clients, including JMX tools.
![[Note]](images/note.png) | |
When using TIBCO BusinessEvents® Extreme Administrator, you need to also have access permission to the domain management node itself as well as all the managed nodes. See the section called “Domain security model” for more details. |
You can use administration clients without authentication to view some general public properties for each node on the network. These are the properties published by the discovery service.
Access to all other node details - and to the managed elements contained within the node - is controlled via the security service. To access these elements, you need to be authenticated. In TIBCO BusinessEvents® Extreme Administrator you do this by logging in to the domain, after which your credential is cached for future accesses to all nodes managed by the domain. When using the command line client, you must provide the authentication with each command. JMX credential management is specific to the JMX tool.
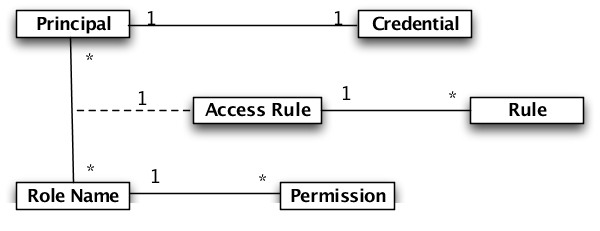
The security model is defined more formally in Figure 5.1, “Security Model”.
The concepts in the security model are:
Principal - an entity that can be positively identified and verified via a technique known as authentication
Credential - password used to control access to information or other resources.
Access Rule - associate permission with a specific role name.
Rule - an access control directive for a specific resource (type) in the system.
A principal definition contains one or more role names that define the access privileges granted to the principal.