Creating an LDAP Container using an LDAP Group
If you are using an LDAP group source in the LDAP container definition, a group DN is used to identify the directory entry that is the group. When a group DN is specified, a member attribute is also specified, which holds the collection of member identifiers (DNs). This provides the list of candidate resources.
Procedure
-
Open the Organization Browser (see
Accessing the Organization Browser).
If any LDAP containers had previously been defined, they are shown in the left pane of the dialog, and the details of the selected container are shown in the right pane.
If there has not been any LDAP containers created yet, the only thing displayed is the Create New LDAP Container button.
Note: After you’ve defined a container, you can edit it by selecting the container in the list, then clicking >
Edit. You can generally follow the same steps in this procedure to edit an existing LDAP container.
>
Edit. You can generally follow the same steps in this procedure to edit an existing LDAP container.
However, if the existing LDAP container contains resources, the LDAP source for that container is fixed; you cannot delete nor change the LDAP source.
Also note that if an LDAP source defined in an LDAP container is currently offline, you cannot edit the container until the LDAP source is back online.
- Click Create New LDAP Container.
- On the New LDAP Container dialog, enter a name and an optional description for the new container.
-
In the
Select Organizations section, you can optionally specify
organization relationships for the new container (note that this is applicable only if there are multiple organizations in your organization model).
If the container has a relationship with an organization, resources in the container will be able to see that organization in the Organization Browser, as well as organizations that do not have an explicit relationship with a container. Resources can be mapped to positions in organizations that the user can see in the Organization Browser.
For more information about organization relationships, see Container Organization Relationships.
If you are not specifying organization relationships for this container, proceed to the next step. (You can specify organization relationships for this container at a later time.)
To specify organization relationships:
- Click Next.
- Ensure that the Group source option is selected.
-
In the
Alias field, select the LDAP source from which you want to obtain resources.
The names in the Alias list are user-readable names that an administrator has assigned to each of the LDAP Servers available in the enterprise.
- Optional:
In the
Base dn field, enter the branch (for example, an organization unit) in which you would like to limit the search in the LDAP directory structure. This increases the efficiency of the search if the LDAP contains a large number of branches.
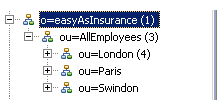
The search base must provide the complete path to the desired branch in the LDAP directory structure. For example (this illustration is from an external application that shows the LDAP source), if you want to limit the search to the “London” organization unit in the following LDAP source ...
... you would enter the following in the Base dn field:
ou=London, ou=AllEmployees, o=easyAsInsurance
You can also leave the Base dn field blank, which causes the entire LDAP directory structure to be searched.
-
In the
Group DN Query field, identify the objectClass of the LDAP directory whose entries are group entries.
This field defaults to "(objectClass=group)". Note that the value must be enclosed in parentheses.
For information about objectClasses, see LDAP Group Sources.
-
In the
Resource name attribute(s) field, enter one or more LDAP attributes by which you want the resources to be displayed in the list of candidate resources.
The resource name attribute is significant for the following reasons:
- It specifies the name by which the user must log into the BPM application.
- It specifies the name by which the resource is listed when mapping resources to groups and/or positions in the organization model. That is, they must be names that the user doing the mapping can use to uniquely identify the resources. For example, you probably wouldn’t want to use only “sn” (surname), as that may not be unique among all resources.
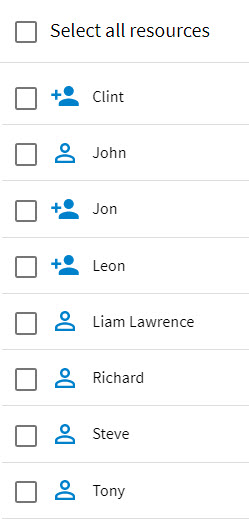
For example, the following shows resources when resource attributes were chosen to identify the resources by both forename and surname:
The default resource attribute is “cn”, which typically contains a full name. But depending on the data in the LDAP source, there may be more suitable attributes for this use.
You can specify multiple attributes in the Resource name attribute(s) field. For instance, you could enter “givenname sn” to display the resource’s first name and last name (again, depending on what is stored in those attributes on the chosen LDAP source).
Once you save the LDAP container you will be able to view the list of resources for the container. For the LDAP entities you see in that list that have not yet been “added”, the resource name will be constructed based on the resource name attribute(s).
After a resource has been added (either using the Add Resource function or by mapping the user to a group or position), you can edit a resource's resource name by selecting the resource, then click
 .
.
It is possible to change the resource name attribute setting for the container, but that will not affect the resource name of resources that have already been added. It will, however, change the name that is constructed for the remaining LDAP entries that have not yet been added. For instance, using the example shown above, if you change the value in the Resource name attribute(s) field to “cn” (which contains "Mr" or "Mrs" with the resource's full name), the resource names now appear as shown below in the list of candidate resources.
Notice that the resources that had been previously added (those that have the
 ), are shown with the resource names they had when they were added; the resources that have not been added yet (blank check box), are shown with the new resource names.
), are shown with the resource names they had when they were added; the resources that have not been added yet (blank check box), are shown with the new resource names.
- Using the Search Scope options, specify the depth to perform the search in the LDAP directory structure, as follows:
-
Click
Fetch Group DN.
This causes the Organization Browser to retrieve all of the group DNs whose objectClass matches the one specified in the Group DN Query field.
- In the Group dn field, select the LDAP directory that contains the group entries.
- In the Member attribute field, select the attribute within the LDAP group entry that holds the collection of DNs that identifies the candidate resources.
- Click Fetch Sample to view the group source sample, then click Close to close the sample dialog.
-
Click
Save LDAP Source.
A summary of the LDAP source is displayed.
-
Optionally click
New LDAP Source.
This optional step is used to define a secondary LDAP source. You can define one or more secondary LDAP sources. For more information, see Primary and Secondary Sources.
- Ensure that Group source is selected as the source type.
-
From the
Alias field drop down list, select the secondary LDAP source you would like to add to the LDAP container.
Note that when choosing a secondary source, the alias that was chosen for the primary source is omitted from the Alias field drop-down list.
-
In the
Base dn field, enter the branch (e.g., an organization unit) in which you would like to limit the search in the LDAP directory structure.
This increases the efficiency of the search if the LDAP contains a large number of branches.
The search base must provide the complete path to the desired branch in the LDAP directory structure. For example, if you want to limit the search to the “London” organization unit in the following LDAP...
... you would enter the following in the Base dn field:
ou=London, ou=AllEmployees
-
In the
Group DN Query field, identify the objectClass of the LDAP directory whose entries are group entries.
This field defaults to "(objectClass=group)". Note that the value must be enclosed in parentheses.
For information about objectClasses, see LDAP Group Sources.
- Using the Search scope options, specify the depth to perform the search in the LDAP directory structure, as follows:
-
Click
Fetch Group DN.
This causes the Organization Browser to retrieve all of the group DNs whose objectClass matches the one specified in the Group DN Query field.
- In the Group dn field, select the LDAP directory that contains the group entries.
- In the Member attribute field, select the attribute within the LDAP group entry that holds the collection of DNs that identifies the candidate resources.
- Click Fetch Sample to view the group source sample, then click Close to close the sample dialog.
-
At this point, you need to make a determination which attributes in the secondary LDAP source will be compared to attributes in the primary LDAP source.
The goal of comparing primary / secondary attributes is to ensure that data from the secondary LDAP source is only merged together with the appropriate candidate resource from the primary LDAP source.
Where a match cannot be found, or where it is not one-to-one, the candidate resource will not have a complete, accurate set of information, and it will be either omitted (where no match is found) or marked as "multiple entries" (where the match isn't one-to-one).
For example, if there are several resources with the same last name, you need to check more than just the last name; maybe checking first name too will be enough, or maybe you need to check more attributes (because there may be multiple resources in the secondary LDAP source with the same first and last name — it would not know which to include). Maybe there are other types of data, such as an employee ID that would work better and would avoid inconsistencies in data entry (typos, nicknames, abbreviations, etc.).
You may need to also go back and view the data in the attributes in the primary LDAP source.
For example, if you know that the “ou” attribute in the primary LDAP source contains the complete name of the resources (Clint Hill, John Eustace, etc.), and the “displayname” attribute in the secondary LDAP source contains the same information, those attributes would be prime candidates to link.
Note: If you choose attributes that contain names, always be aware that there may be differences in the way those names were entered in the different LDAP sources, for example, Bob vs. Robert, Mike vs. Michael, or simple misspellings. Things like employee numbers tend to make good attributes to link.For additional information, see Primary and Secondary Sources.
- In the primary attribute field, choose the primary LDAP source attribute (for example, "ou") that contains data you want to compare to the data in the attribute you will choose in the next sub-step.
- In the secondary attribute field, choose the secondary LDAP source attribute (for example, "displayname") that contains data you want to compare to the data in the attribute you chose in the previous sub-step.
-
Click
 .
.
-
Click
Save LDAP Source.
A summary is displayed that shows the primary and secondary LDAP sources.
- Optionally click New LDAP Source to add another secondary LDAP source, then repeat the sub-steps above to define the new secondary source.
- Click Next.
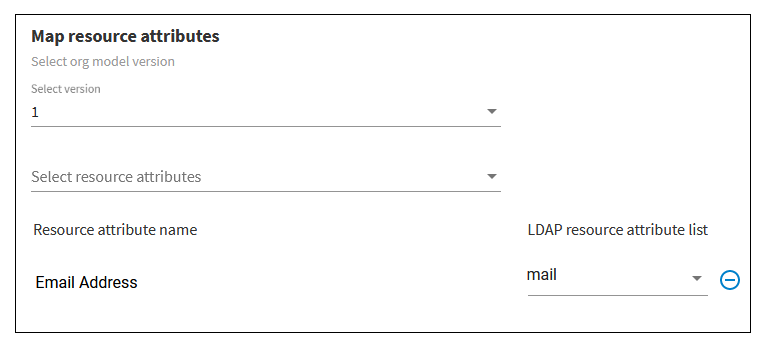
-
Specify any desired resource attribute mapping, as described below.
You may need to map one or more resource attributes to attributes in the LDAP source you have defined in your LDAP container. You may need to do this because the business process does not have direct access to the attributes in the LDAP source, but it does have access to the resource attributes in the organization model.
For the example shown in these steps, assume that the mail attribute in the LDAP source contains data that the business process needs. The business process has been designed in such a way to expect this data in the EmailAddress resource attribute. Therefore, if the mail LDAP attribute is mapped to the EmailAddress resource attribute, the business process will be able to access the user’s email address at runtime.
- Select the version of the organization model that contains the attributes you want to map.
- From the Select resource attributes field, select an attribute from the organization model.
- From the Select LDAP attributes field, select the LDAP resource attribute you want mapped to the attribute you selected in the previous step. For example:
- Repeat the previous two steps to map additional attributes, if desired.
- When you've mapped all of the desired attributes, click Next.
- Click Create LDAP Container.
- Click Show Resources to see a list of the resource candidates in the new LDAP container, Edit to edit the newly created container, or the x to the right of New LDAP Container to see a list of all LDAP containers.


 to the right of the attributes you want to remove.
to the right of the attributes you want to remove.