Testing an Application That Uses SAML Authentication
The following procedures show how to test an application that uses SAML authentication.
Prerequisites
- Resource template and resource instance of type SAML SSO Web Profile Authentication must be created and installed using Administrator UI or CLI.
- SAML SSO Web Profile Authentication Policy must be applied to an application using TIBCO Business Studio.
- Deploy Application in Administrator UI. The Web Application must be SSL enabled.
- Ensure that IdP domain is added in the allowed referrers list of a node.
Testing an application when ADFS is used as an IdP
Procedure
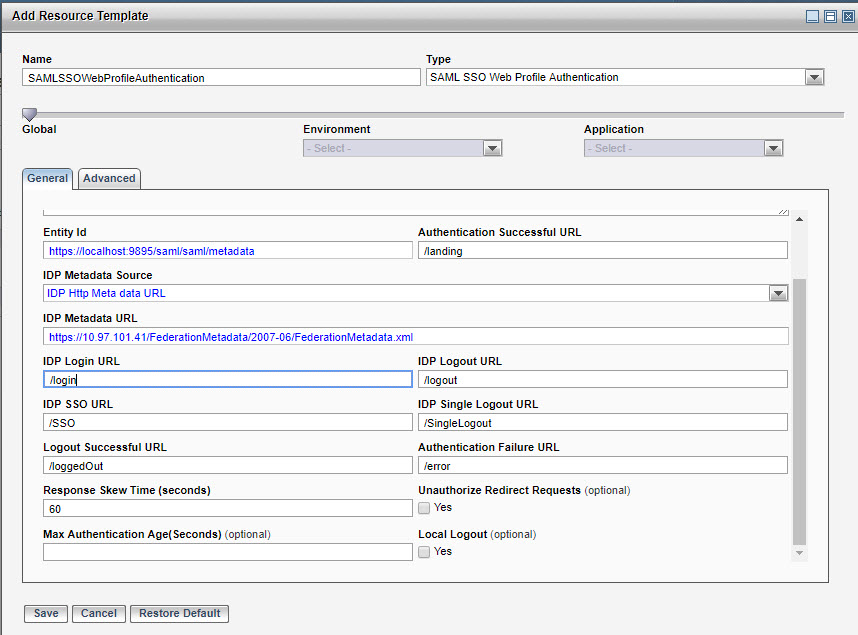
- In a browser go to the URL for the Web application which is the URL configured in the resource template
Authentication Successful URL field. For example, the following image displays sample resource template configuration when ADFS is used as an IdP. You are redirected to the ADFS sign-in page.
Sample Resource Template Configuration
- Enter the login credentials and click Sign in. After successful authentication and authorization, you are redirected to the landing page.
Testing an application when Google is used as an IdP
Procedure
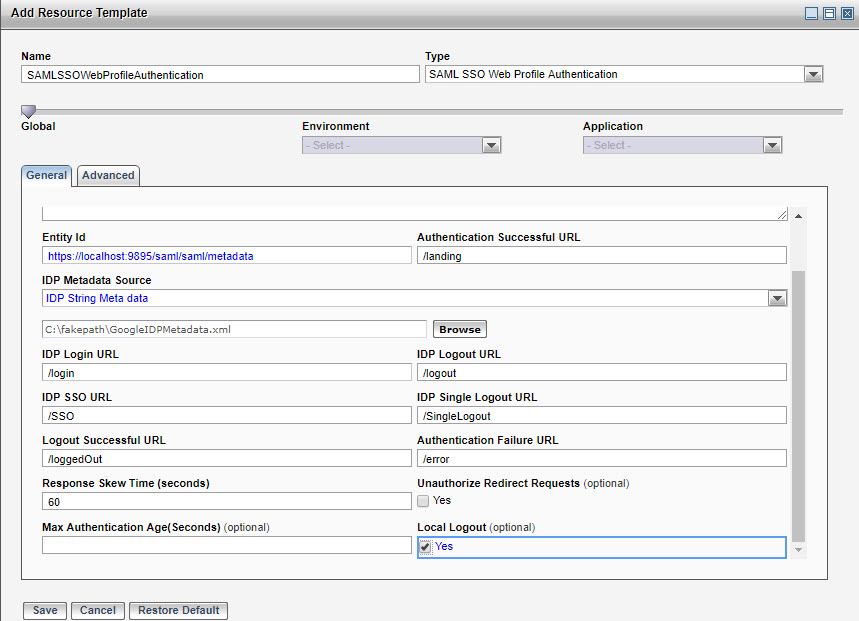
- In a browser enter the URL for the web application which is the URL configured in the
Authentication Successful URL field of the resource template. For example, the following image displays sample resource template configuration when Google is used as an IdP. You are redirected to the Google authentication page.
Sample Resource Template Configuration
- On the Google sign-in page log in with your Google credentials for the registered domain with the IdP. After successful authentication and authorization, you are redirected to the landing page.
Copyright © Cloud Software Group, Inc. All rights reserved.