Enabling SSL on JBoss WildFly Application Server
Enable and verify SSL on JBoss WildFly Application Server.
Default Application Realm
By default, JBoss WildFly application server uses
8443 port for the HTTPS protocol. Type the following URL into your browser:
https://IPaddress:8443/eml/Login. By default, the application realm is available at the following locations in the
standalone.xml file:
-
<security-realm name="ApplicationRealm"> <server-identities> <ssl> <keystore path="application.keystore" relative-to="jboss.server.config.dir" keystore-password="password" alias="server" key-password="password" generate-self-signed-certificate-host="localhost"/> </ssl> </server-identities> <authentication> <local default-user="$local" allowed-users="*" skip-group-loading="true"/> <properties path="application-users.properties" relative-to="jboss.server.config.dir"/> </authentication> <authorization> <properties path="application-roles.properties" relative-to="jboss.server.config.dir"/> </authorization> </security-realm>
-
<http-connector name="http-remoting-connector" connector-ref="default" security-realm="ApplicationRealm"/>
-
<https-listener name="https" socket-binding="https" security-realm="ApplicationRealm" enable-http2="true"/>
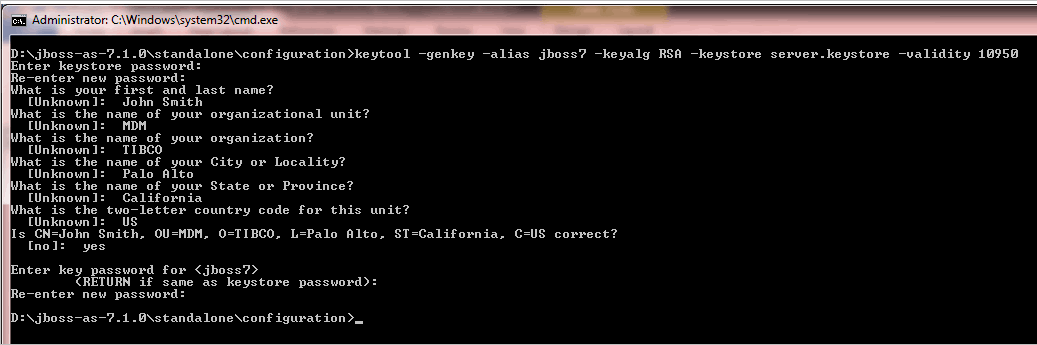
Create Custom Application Realm
If you do not want to use the default application realm, you can create custom application realm using the subsequent steps.
Procedure
Copyright © Cloud Software Group, Inc. All rights reserved.