Example 2 - Single Sign-on Using a SOAP Binding
In this example, a client application supplies a user’s credentials (username and password) when it calls the Mediation application.
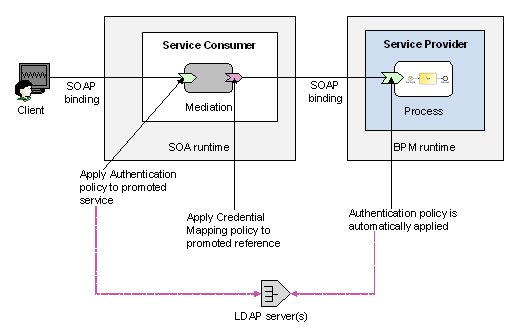
The Mediation application authenticates these credentials, which are automatically propagated to the service exposed by the BPM process across a SOAP binding. If the propagated credentials are also valid for the BPM process, access to the BPM service will be granted.
Note: Note the following points about this scenario:
- The Mediation application must validate the user’s login credentials against the same LDAP server(s) used by the BPM runtime.
- The credentials used to login to the Mediation application must belong to a valid BPM user. If they do not, authentication against the BPM runtime will fail (even if the credentials were successfully validated against the LDAP server by the Mediation application).
To enforce authentication in this way, configure the Mediation application as follows:
Procedure
- Add an appropriate client authentication policy to the promoted service. The policy will be applied at runtime, forcing the Mediation application to authenticate the client’s identity against the referenced LDAP server.
- Add an appropriate credential mapping policy to the promoted reference. The policy will be applied at runtime, forcing the reference to propagate the client’s previously authenticated identity to the endpoint of the exposed service. This identity will then be authenticated by the BPM runtime.
Copyright © Cloud Software Group, Inc. All rights reserved.